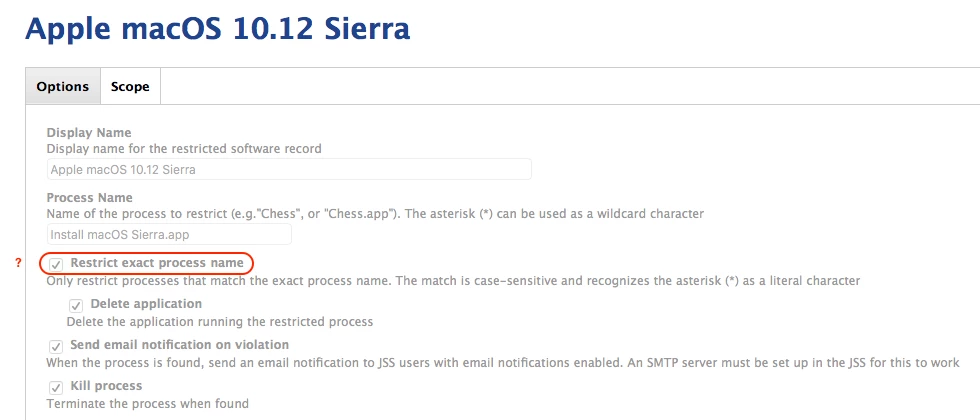
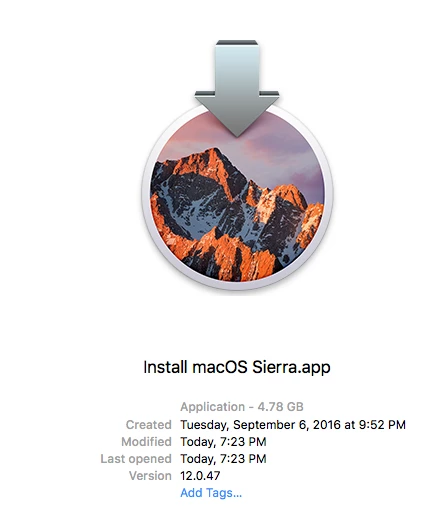
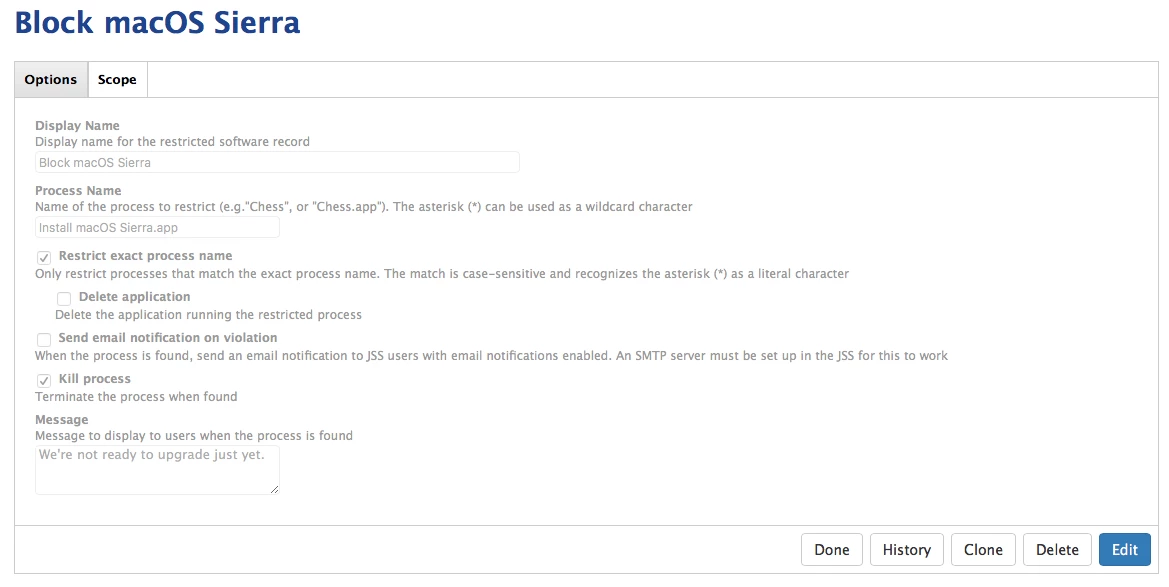
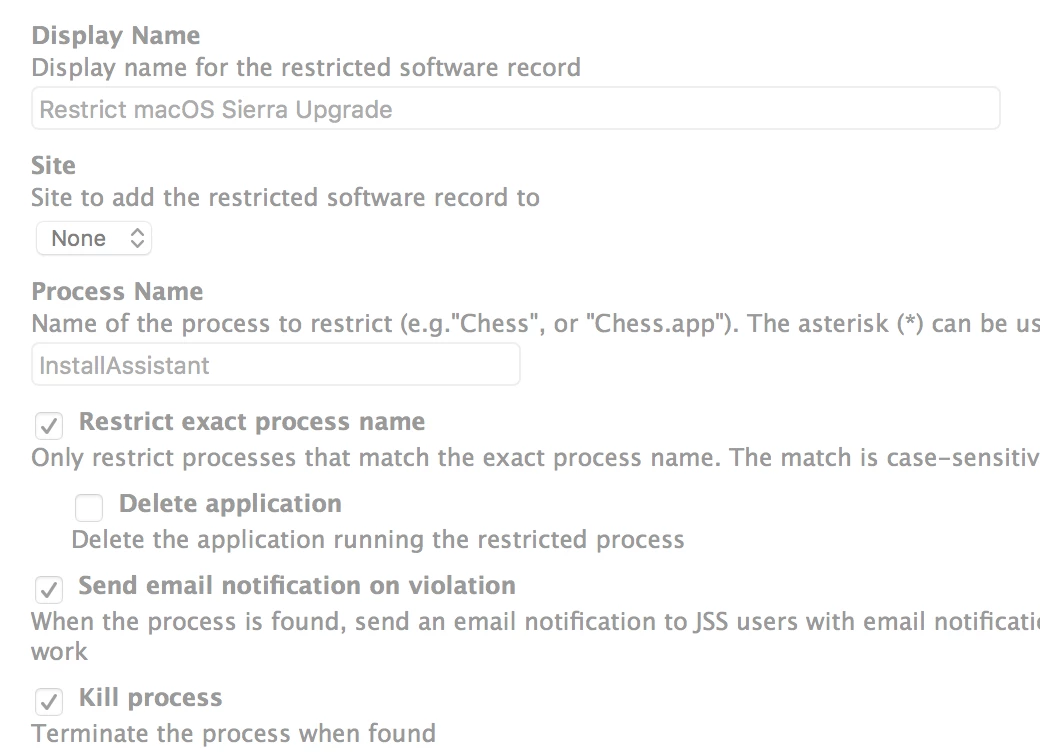
Does anybody have the process name for the Sierra installer, so I can add it to restricted software? I need to make sure the Sierra is not installed on any of the Macs in my environment. The Sierra installer should have a unique name, right?
Question
Restrict Sierra betas and retail
 +11
+11Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.