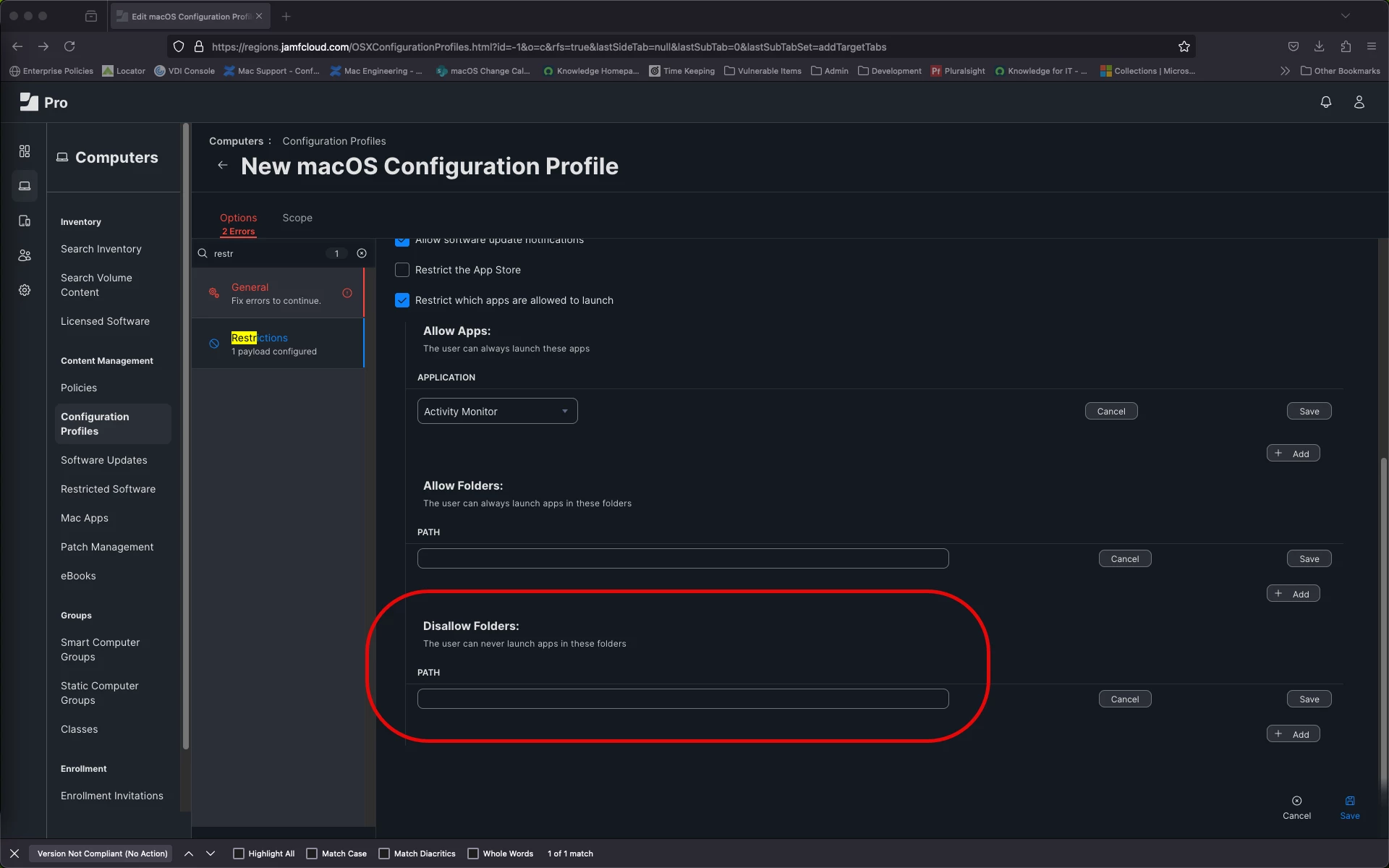
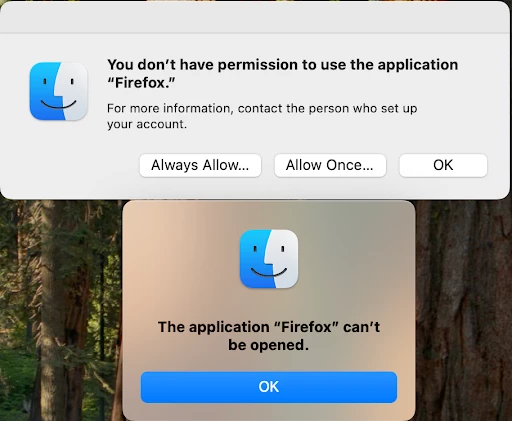
I've been tasked with finding a way to prevent users from running applications out of unapproved locations such as their Desktop and Downloads folders. I found a nearly 10 year old thread talking about doing exactly that, and it doesn't seem like much has changed in the years since. That said, any decade old device management thread is going to be really out of date.
Are there any major gotchas I should be aware of while building out the test Restrictions here? Things like needing to whitelist unexpected directories for Microsoft or Google products? Should I hold off until the Restrictions payload gets updated to match the modern Jamf payload setup?