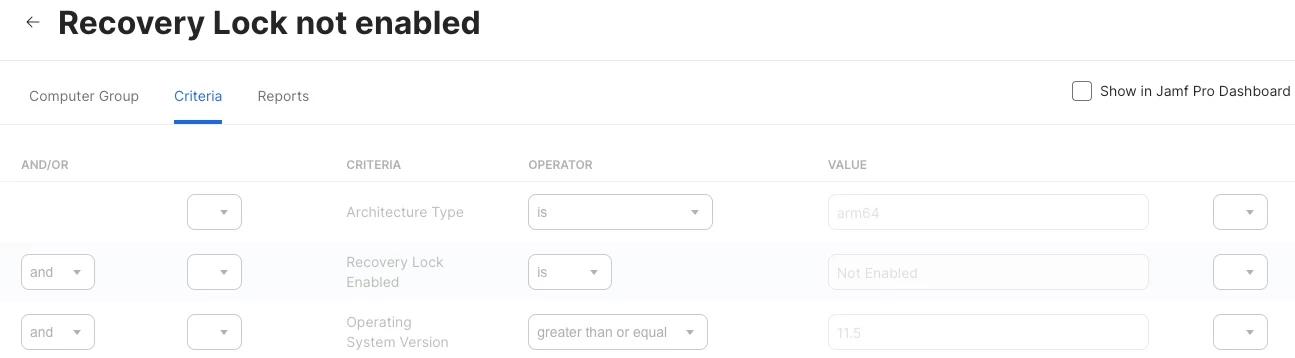
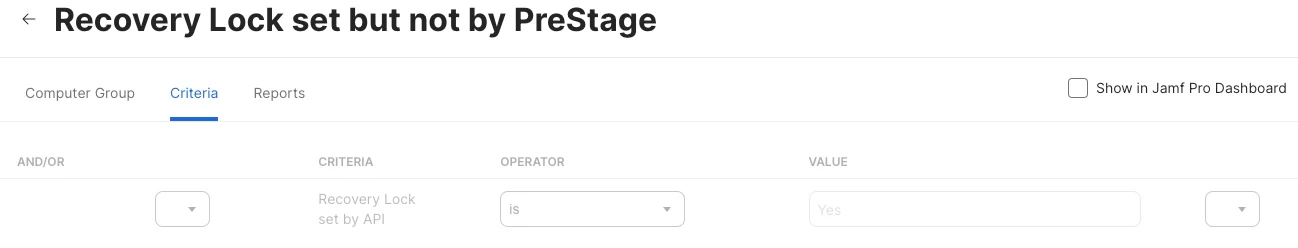
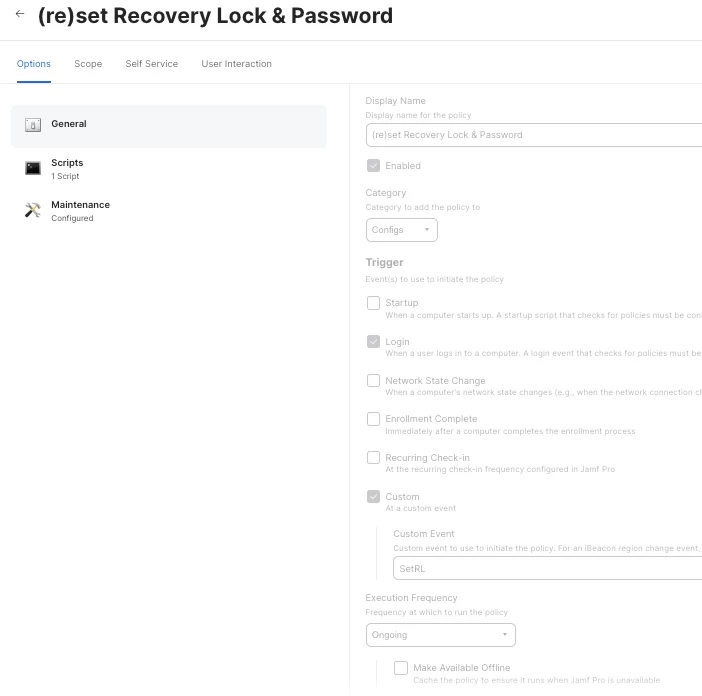
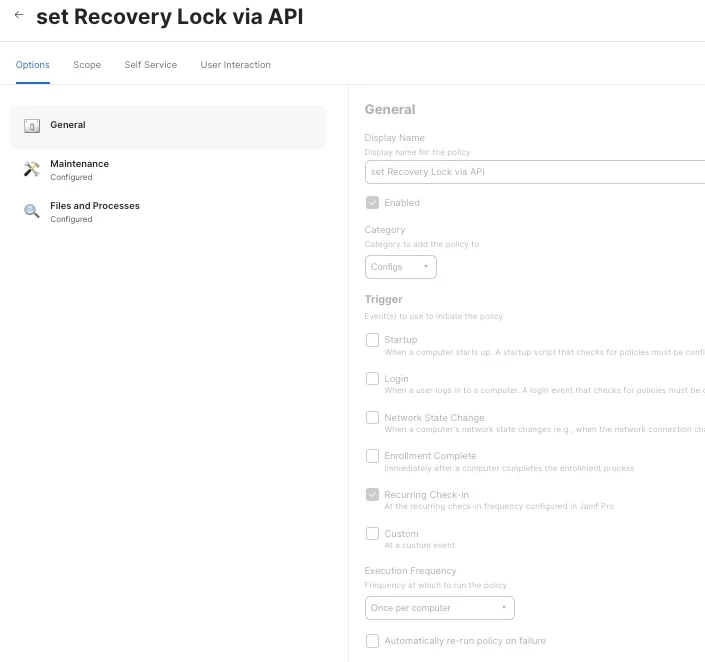
If the Apple Silicon Mac computers can not be enrolled through PreStage Enrollment, the Recovery Lock can only be set from remote command, here's how to do it in Jamf API.
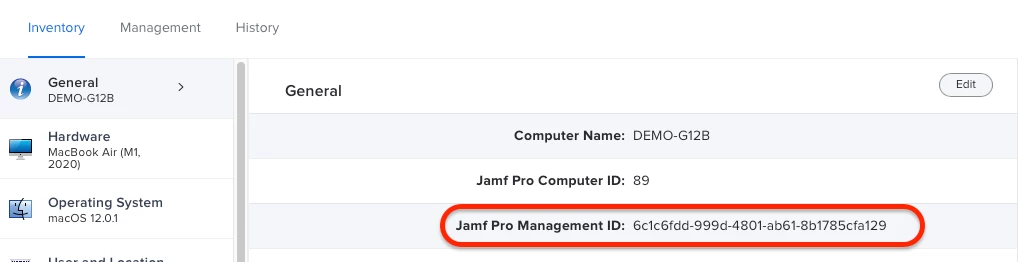
1. First, we need to know the managementId of the target computer. we can copy it from computer‘s inventory. (Jamf Pro Server 10.50.0 and above)
2. Open the Jamf Pro Server API page (https://yourInstance.jamfcloud.com/api, or https://yourjss.domain.com:8443/api) , and choose Jamf Pro API PRODUCTION View.
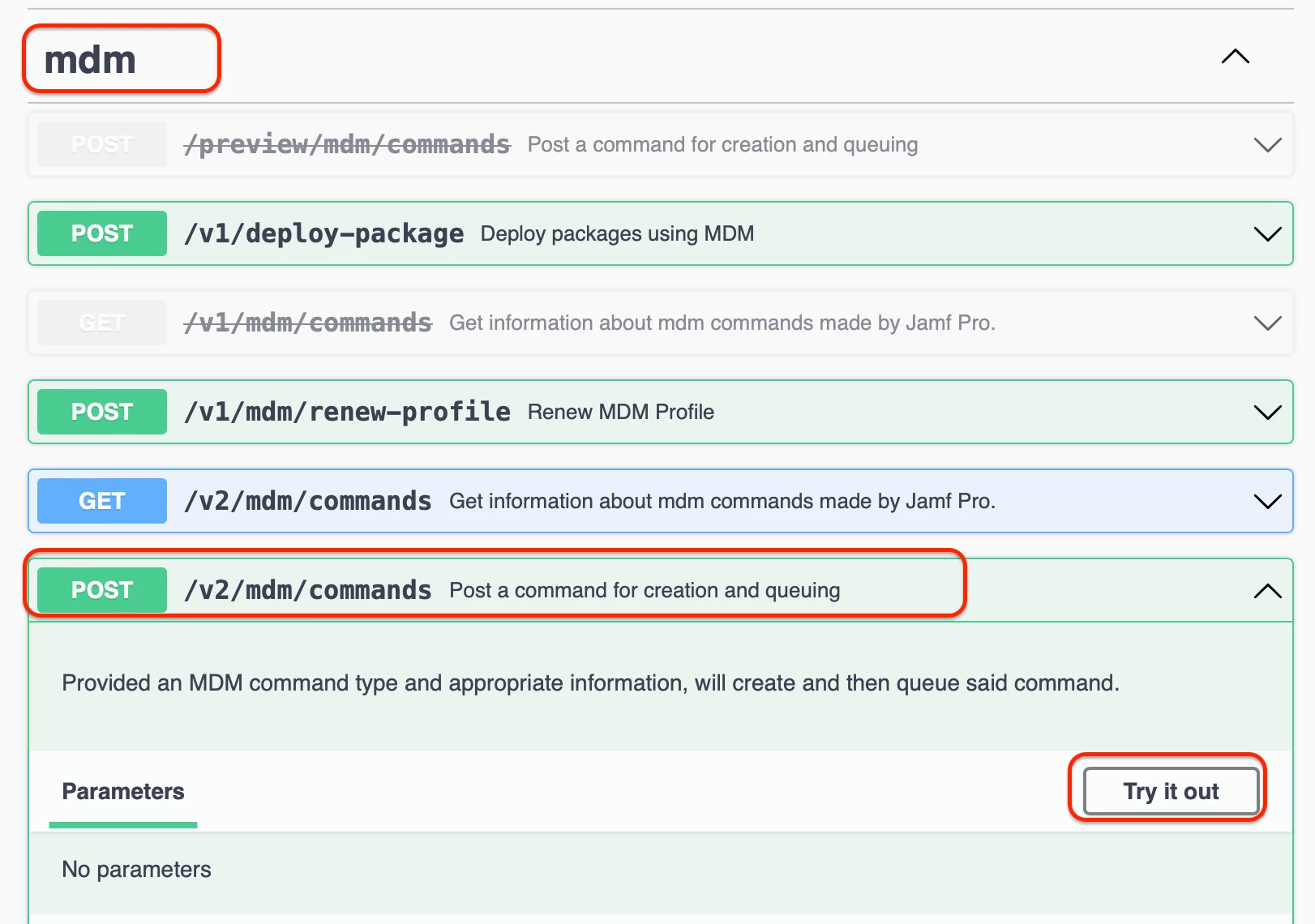
3. Navigate to "MDM", and choose "POST /v2/mdm/commands", then click "Try it now".
4. Modify the request json body. Input the managementId and the recovery lock password. Set to empty ("") will remove the recovery lock password, set to a different one from previous can RESET the existed recovery lock passcode directly. (PS: Firmware/EFI passcode cannot be reset, must be removed and then set a new passcode.)
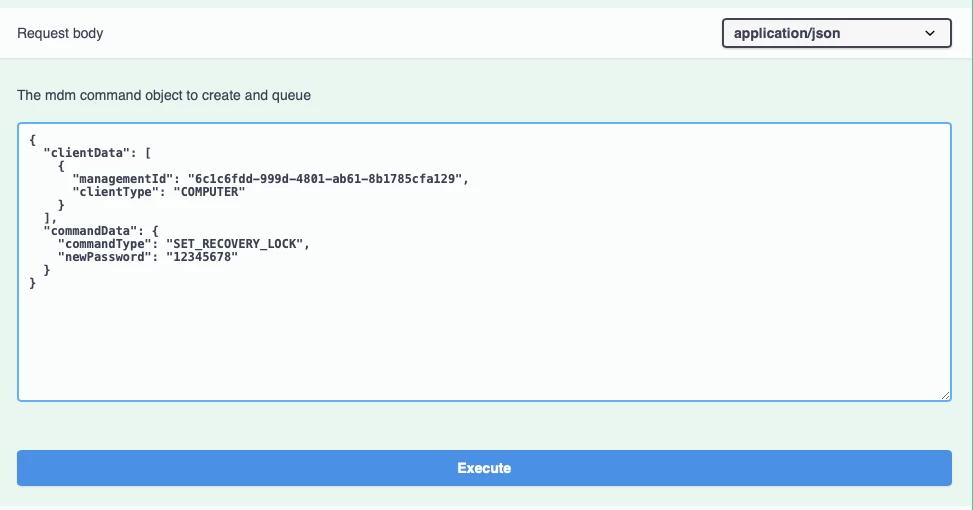
(copy paste and modify it)
{
"clientData": [
{
"managementId": "6c1c6fdd-999d-4801-ab61-8b1785cfa129",
"clientType": "COMPUTER"
}
],
"commandData": {
"commandType": "SET_RECOVERY_LOCK",
"newPassword": "12345678"
}
}
4. Click Execute.
5. The SetRecoveryLock command status can be found in computer's Management History.
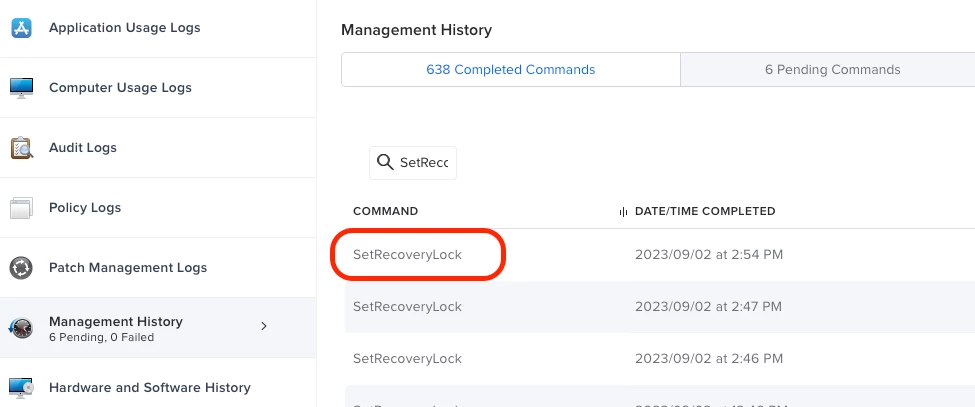
That's all steps to set recovery lock passcode for one Apple Silicon computers in Jamf Pro API page. We can also set it for all Apple Silicon computers from a script.