Hello All,
We’ve just started to implement Jamf Pro in our company. Nearly all configurations are completed except sending compliant information to Microsoft Intune. We have to do this because we’re using Azure (Entra) Conditional Access rules in our company. If a macOS device is not compliant it cannot reach internal company resources. Just a simple rule.
Steps Completed
- Jamf <> Intune compliance partner connector connected successfully.
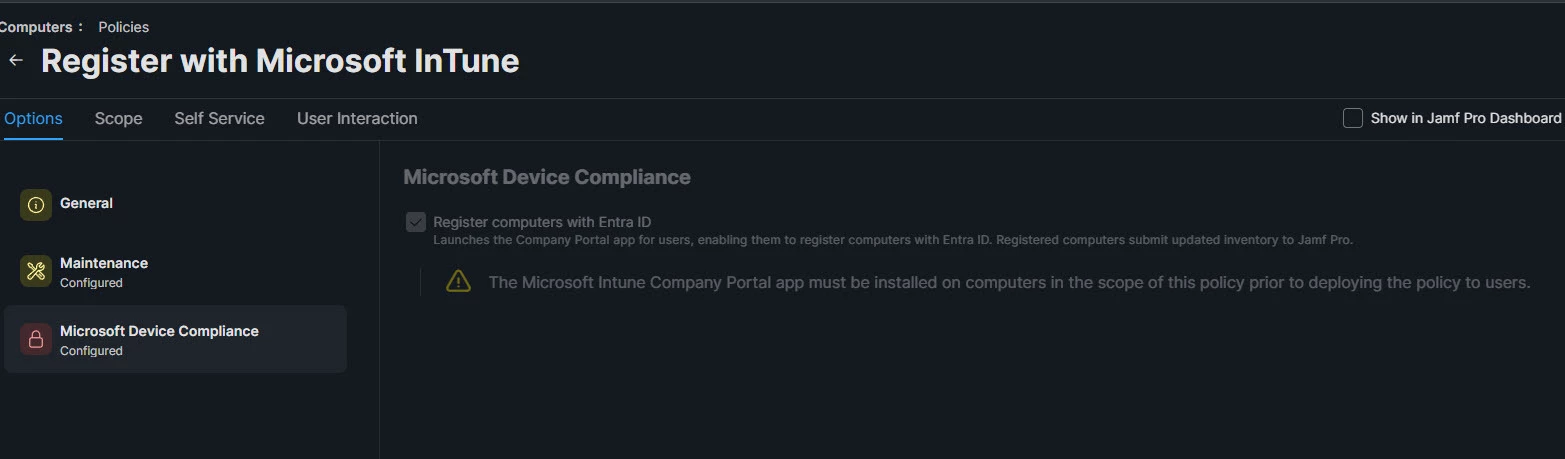
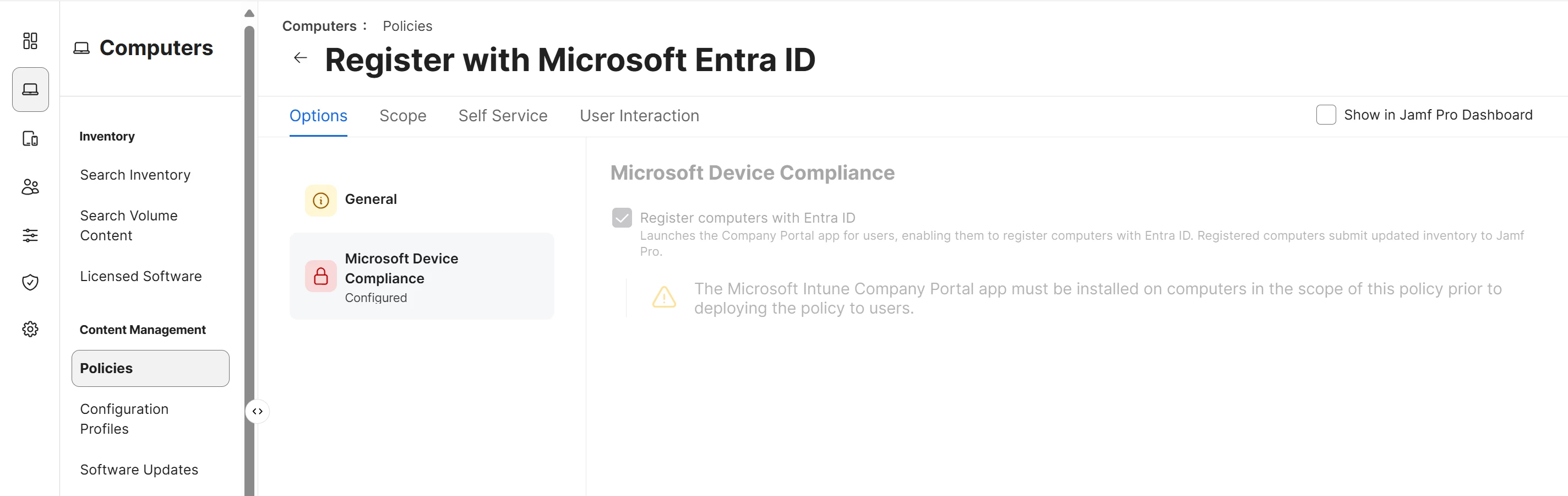
- Microsoft Device Compliance configuration policy prepared in Jamf Policies -https://learn.microsoft.com/en-us/intune/intune-service/protect/jamf-managed-device-compliance-with-entra-id
Problem Summary
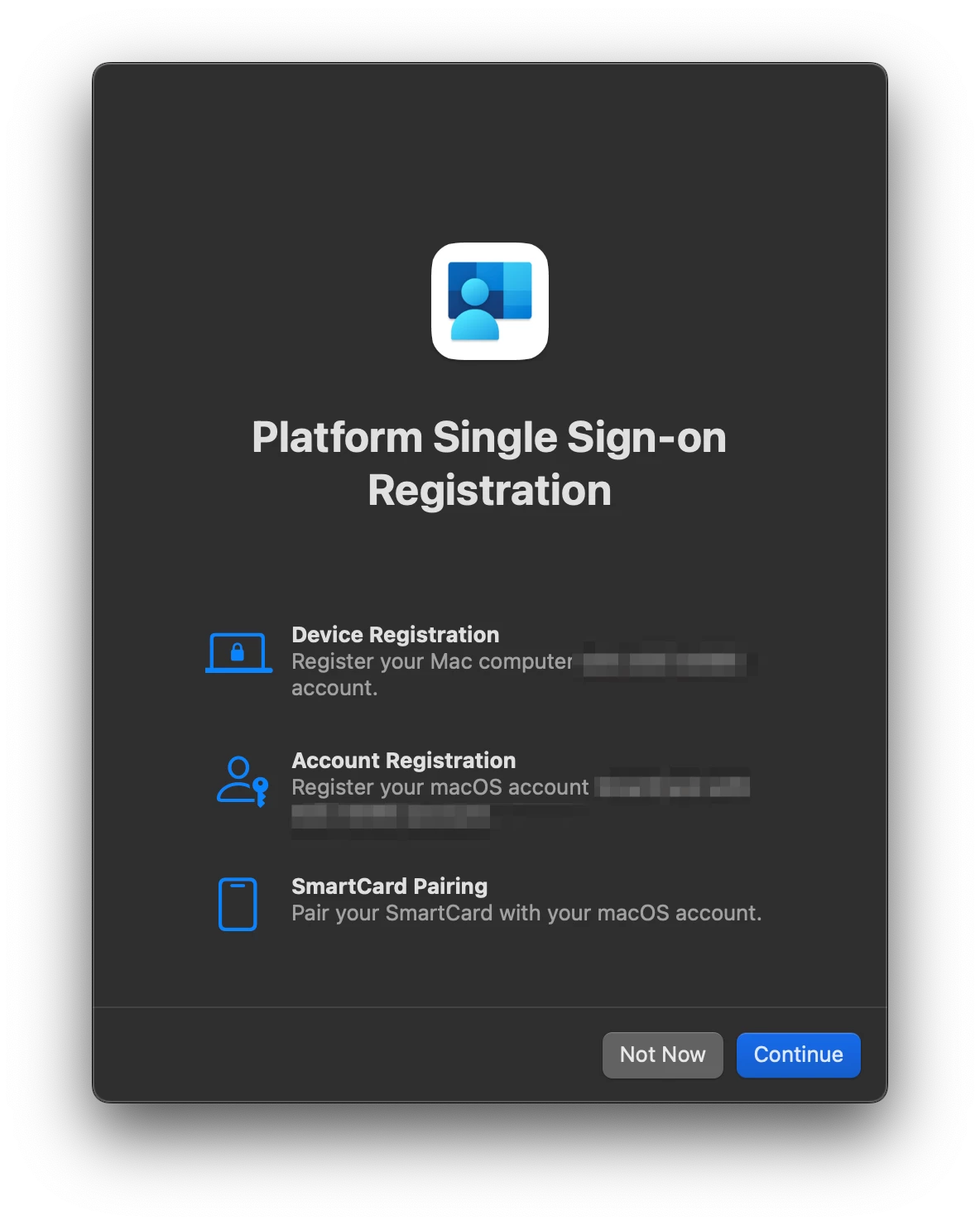
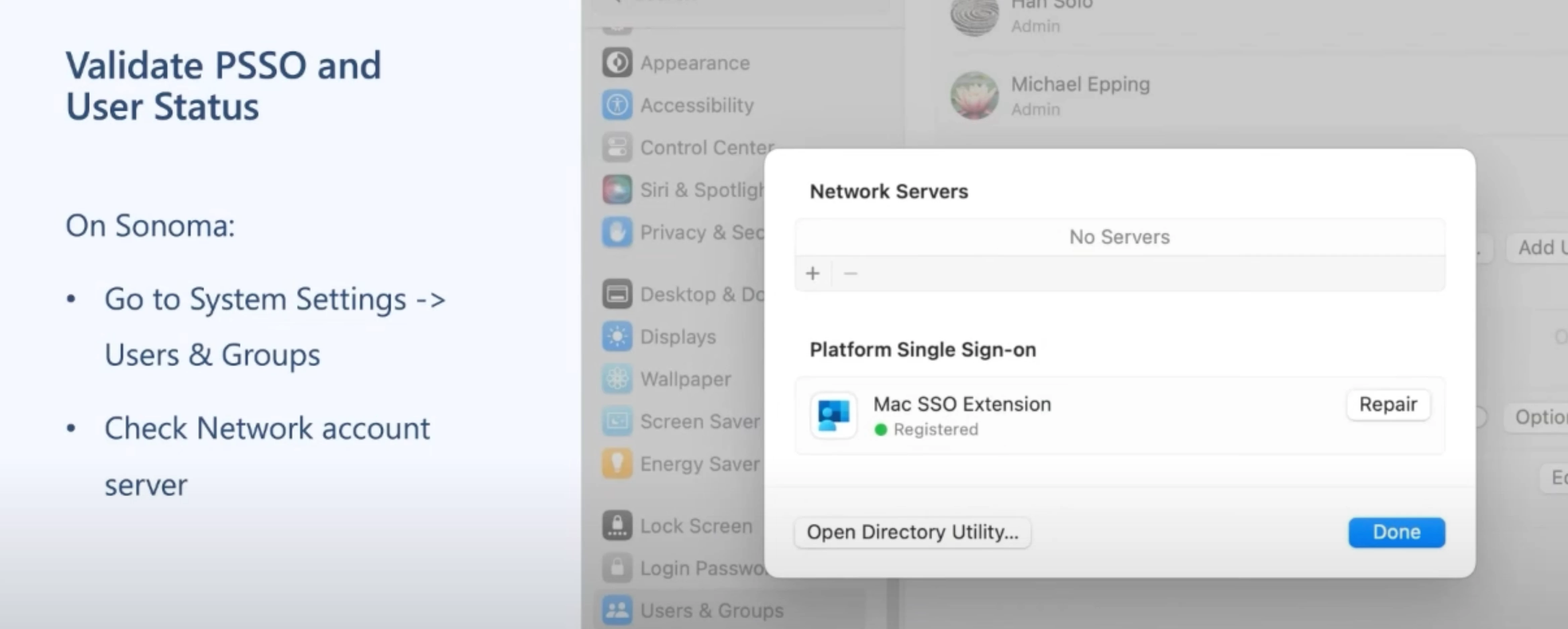
After enrolling to jamf, we are trying to sign in to Company portal and jamf compliance popup appears. Then we are entering our user account details again but somehow Microsoft login page shows that “get app”. It behaves like Company Portal is not installed.
Briefly some of our computers are being Compliant without any problem, but some of others cannot get in compliance and login pages gives us a message asking us to install Company Portal as if it is not installed on the computer.
Do you have any suggestions for this boring problem? I would be happy If you share your experiences or maybe step by step best practices.
Regards