Hi JAMF nation,
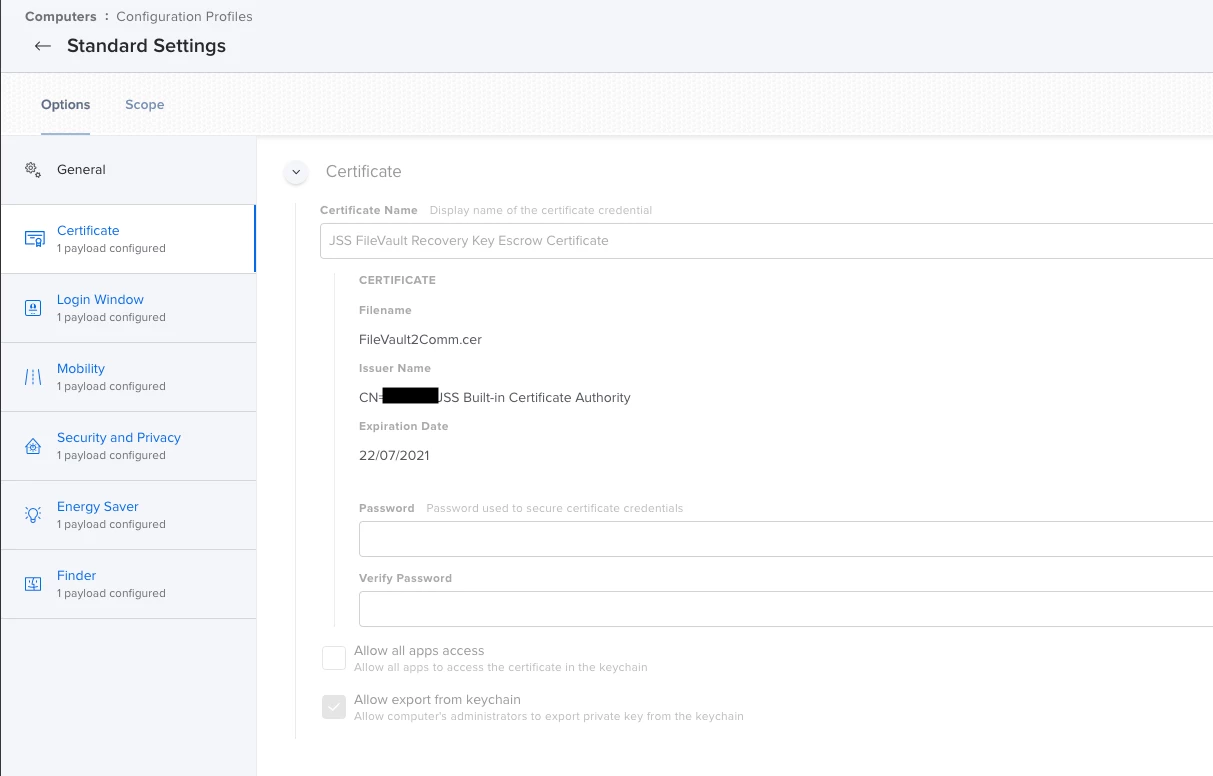
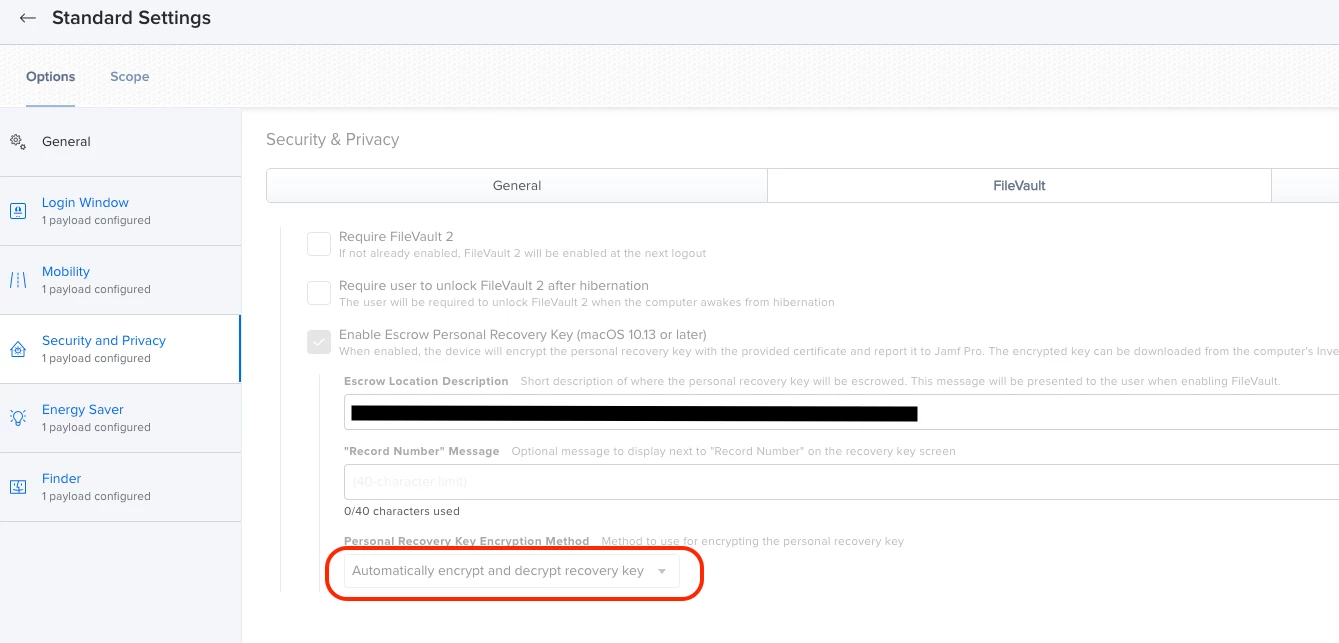
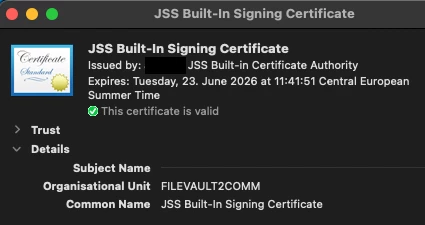
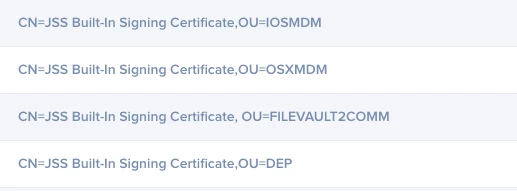
The Cert: CN=JSS Built-In Signing Certificate, OU=FILEVAULT2COMM expired in my paternity leave and when i try to renew it i have only the possibility to revoke it in Settings -> Global Management -> PKI Certificate -> Jamf Pro Built-in CA.
Do i have a chance to renew that? Or do I have to create a new one, but that means to recreate all Recovery Keys, right?
Thank you very much.
BR
Daniel