Last week our cyber security team provided us the newest Fireeye client for Mac OS 11.
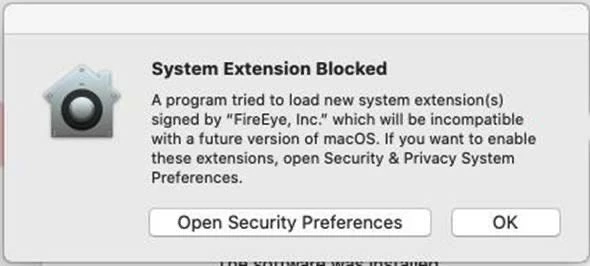
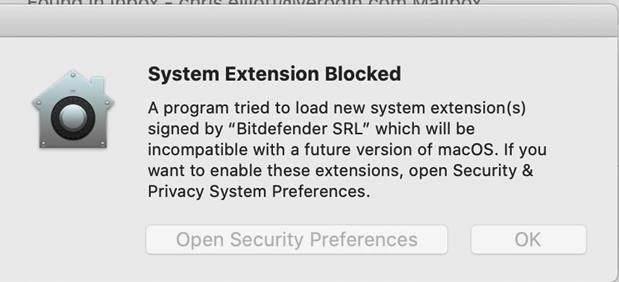
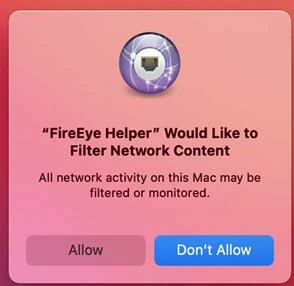
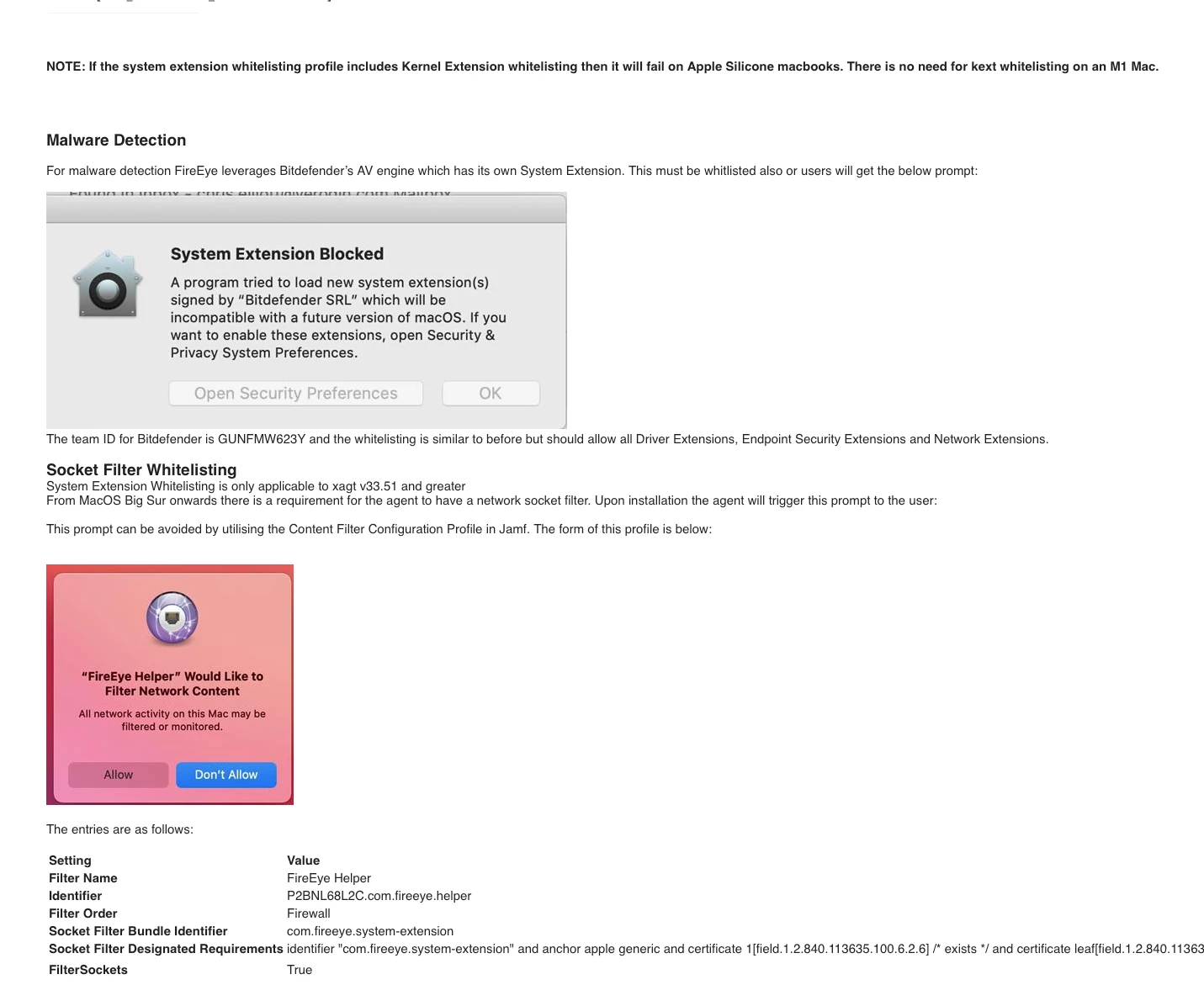
Installing via Jamf Pro Cloud pkg is causing a dialog for the user to consent to the P2BNL68L2C.com.fireeye.helper system extension. It's the same dialog on a standard install.
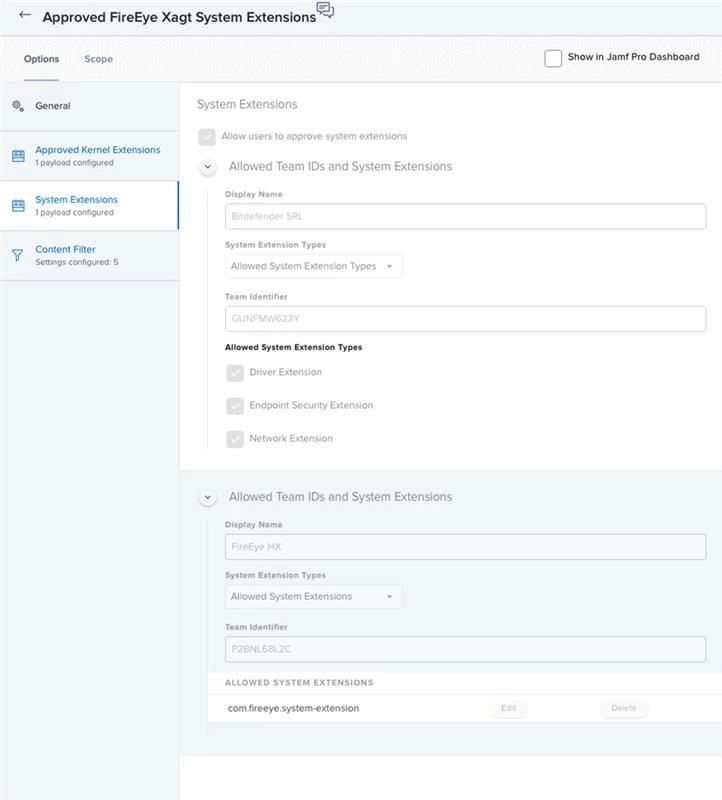
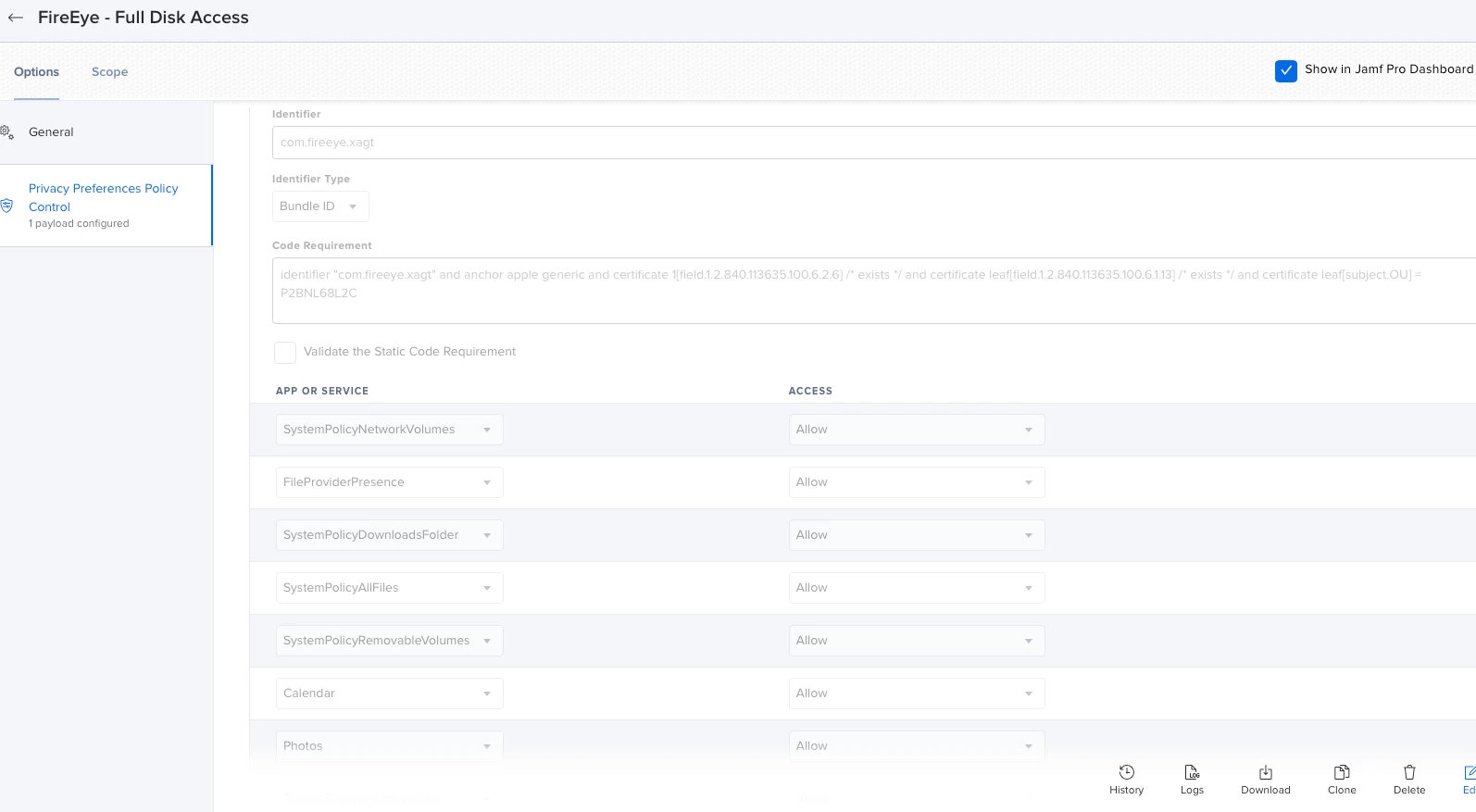
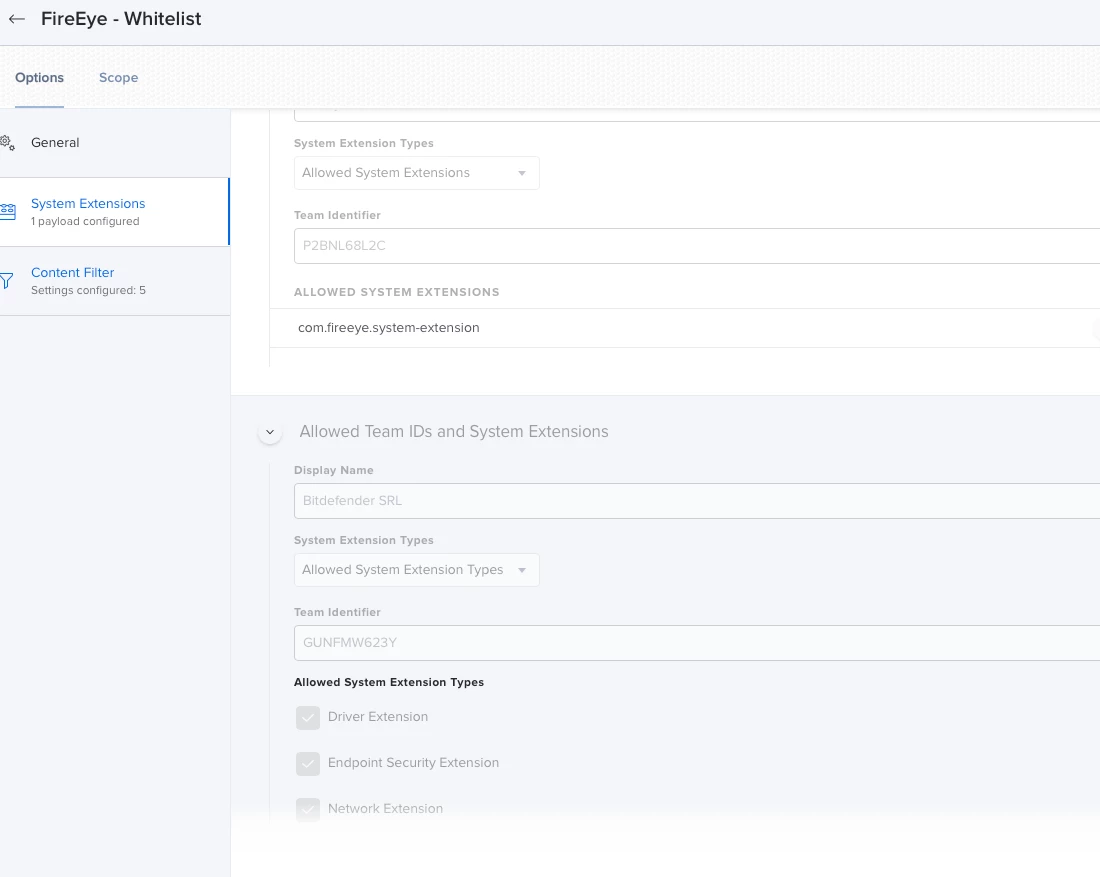
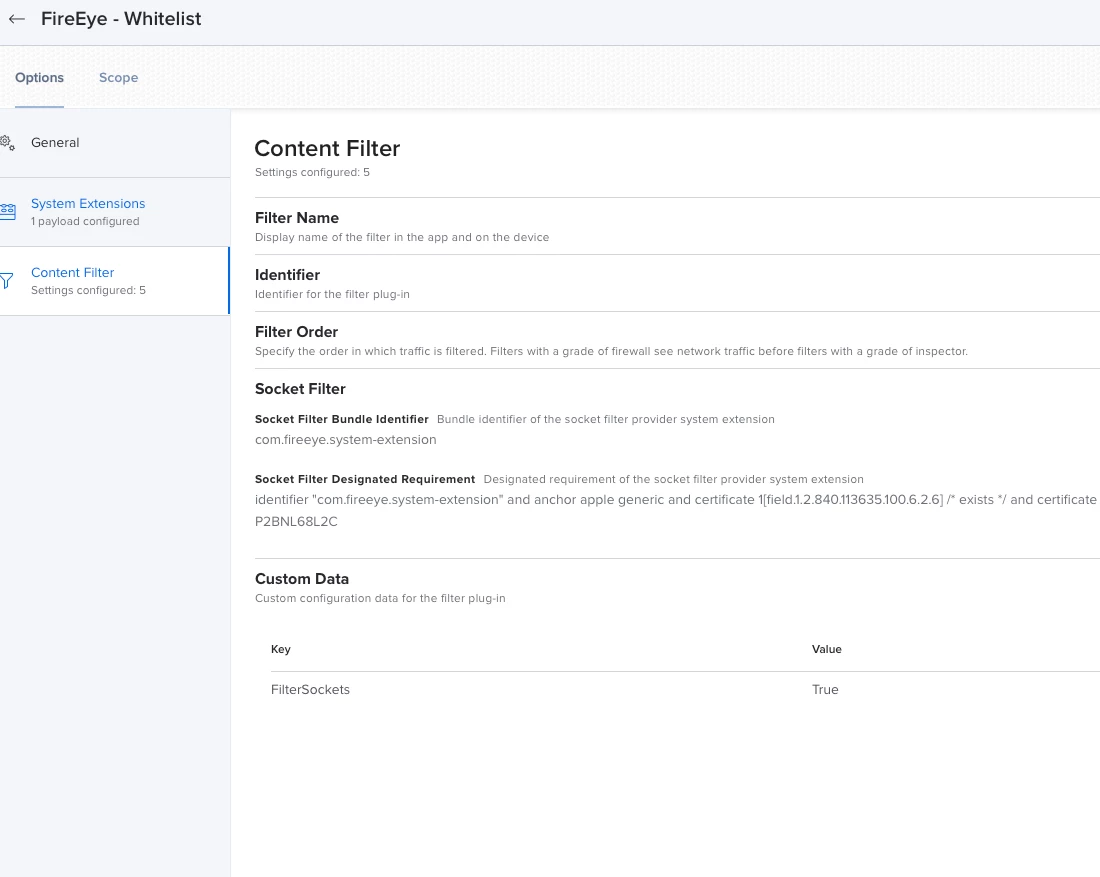
We've testing out the initial app install and get an install prompt that requires manual intervention. Even added P2BNL68L2C.com.fireeye.helper to system extensions, approved kernel extensions to see what would happen: Intervention was still required. We’ve been pretty liberal with the PPPCs and have had the prior kext which doesn’t appear to be used in Big Sur both included and not.
When reaching out to Fireeye support they initially offered assistance after a few emails gave a blanket "Silent uninstallation with MDM solutions is not currently supported on macOS 11.". They plan on adding support in future releases.
Prior versions of the Fireeye Client for Mac OS packaged and performed silent installs without issue and we're hoping someone here has seen and figured a work around.
thanks in advance.
Bill