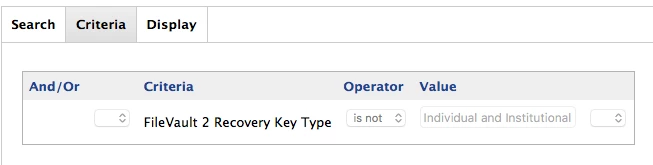
Working through a migration performed on JSS servers a while back. I'd set up a policy to reissue the FileVault 2 key following a few people's work (mostly @rtrouton's FV2 stuff) by deploying a .plist, importing, reissuing, yada yada yada. It's failed on a group that has some bad user identities (wrong admin service account that has local FV2 rights, etc). I don't mind manually touching each one to do
fdesetup add -usertoadd JAMFSERVICEACCOUNTbut I'm having a hard time identifying the right search criteria to separate
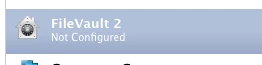 out the 2 configurations to identify the FV2 not configured. I've tried a number of the search criteria around FV2 and none of my attempts seem to properly identify the group which shows as
out the 2 configurations to identify the FV2 not configured. I've tried a number of the search criteria around FV2 and none of my attempts seem to properly identify the group which shows as
"Not Configured"Please help me. I'm stuck in a forest and I desperately can't find the trees.