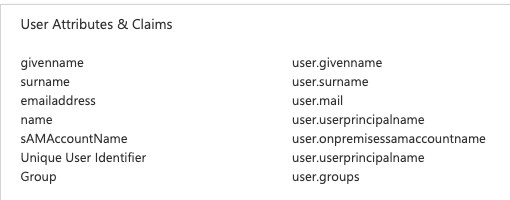
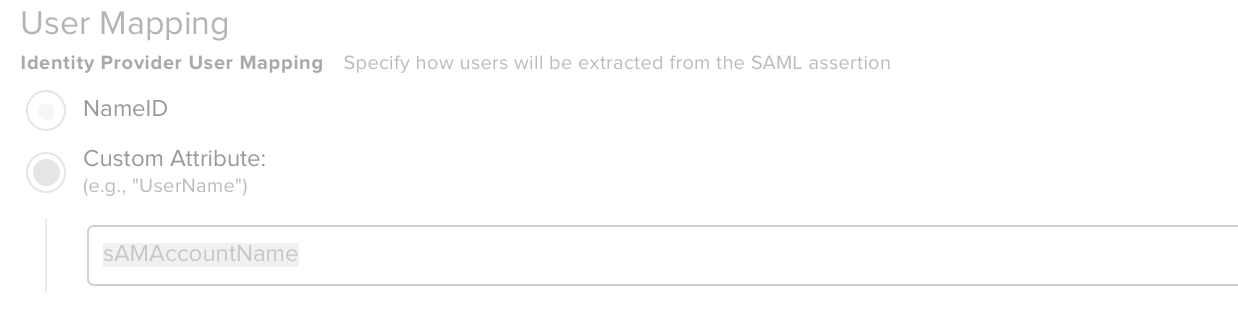
We are deploying a large number of iOS devices and want to use our Google SSO configuration for users to self assign their device.
Users log in and their device is assigned correctly, but we would like to pull additional data from LDAP for the equivalent user. Is there a way to do this automatically?