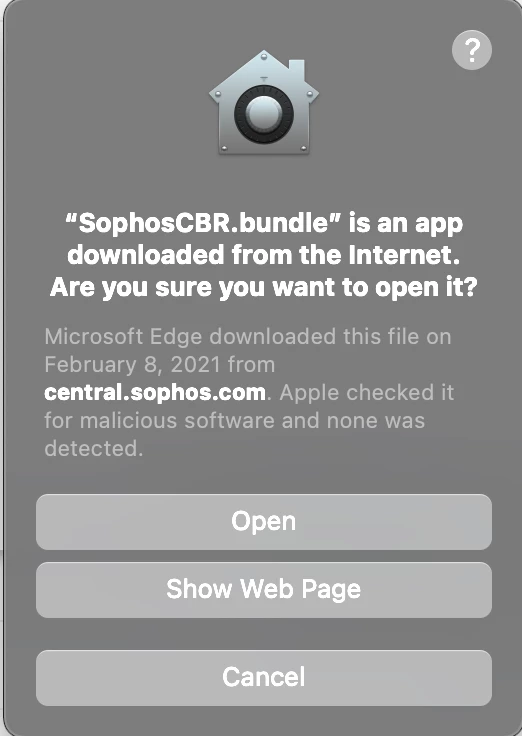
Hey everyone,
I am in the home stretch of an application deployment but have one user experience issue I would like to resolve if possible. I have a new working Sophos deployment, however I get the attached pop up any time the policy runs for install. It must be accepted to install the software and bypassing that for our end users would be excellent.
So far i have tried
xattr -d com.apple.quarantine /var/tmp/SophosInstall/Contents/Helpers/SophosCBR.bundlebefore the install kicks off with no success. Any input would be greatly appreciated on if this is even possible to prevent.