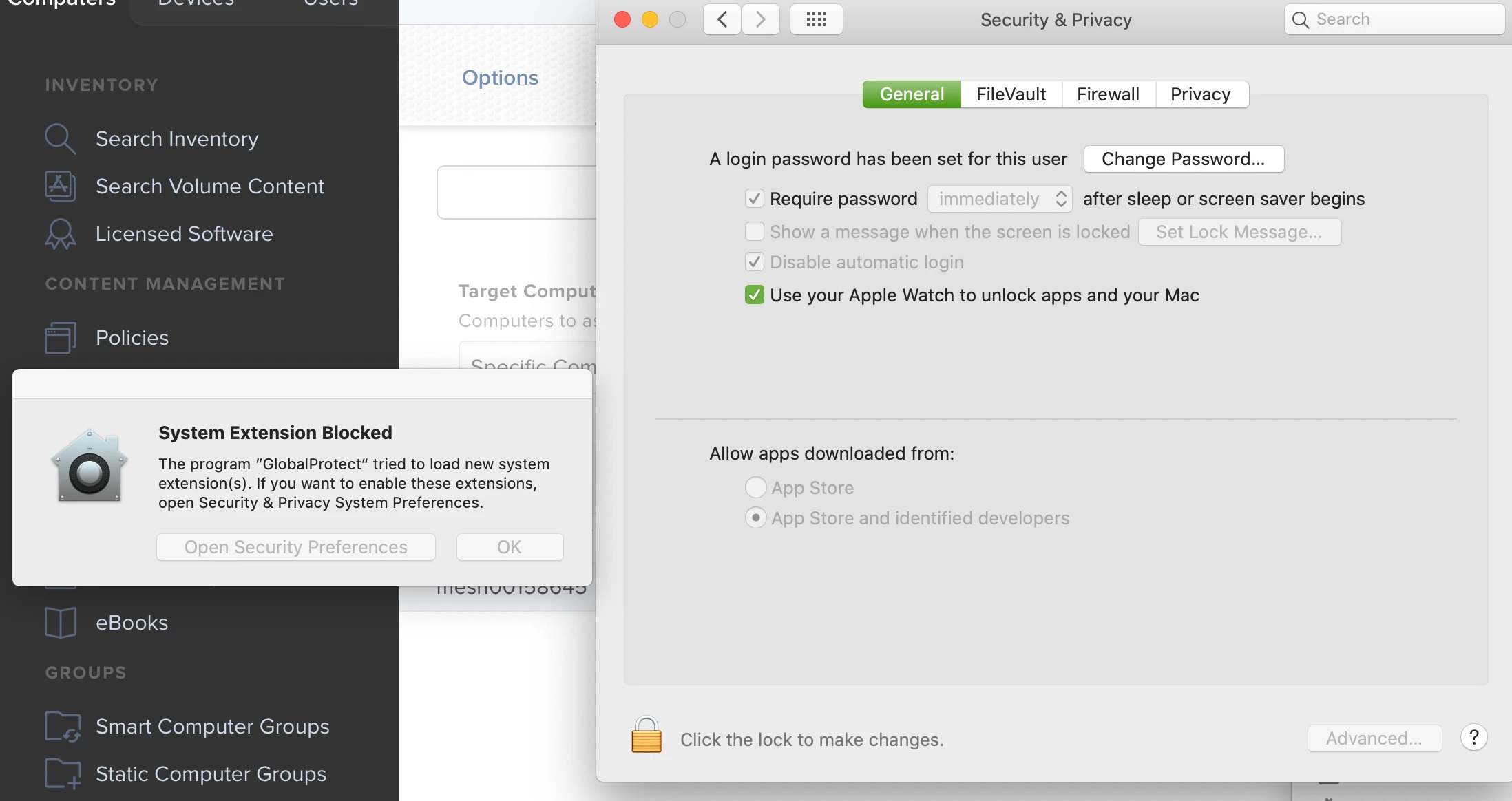
I'm working on setting up a policy for GlobalProtect 5.1.4 which switches to System Extension from Kernel Extensions.
I've set up a config profile to approve the system extension.
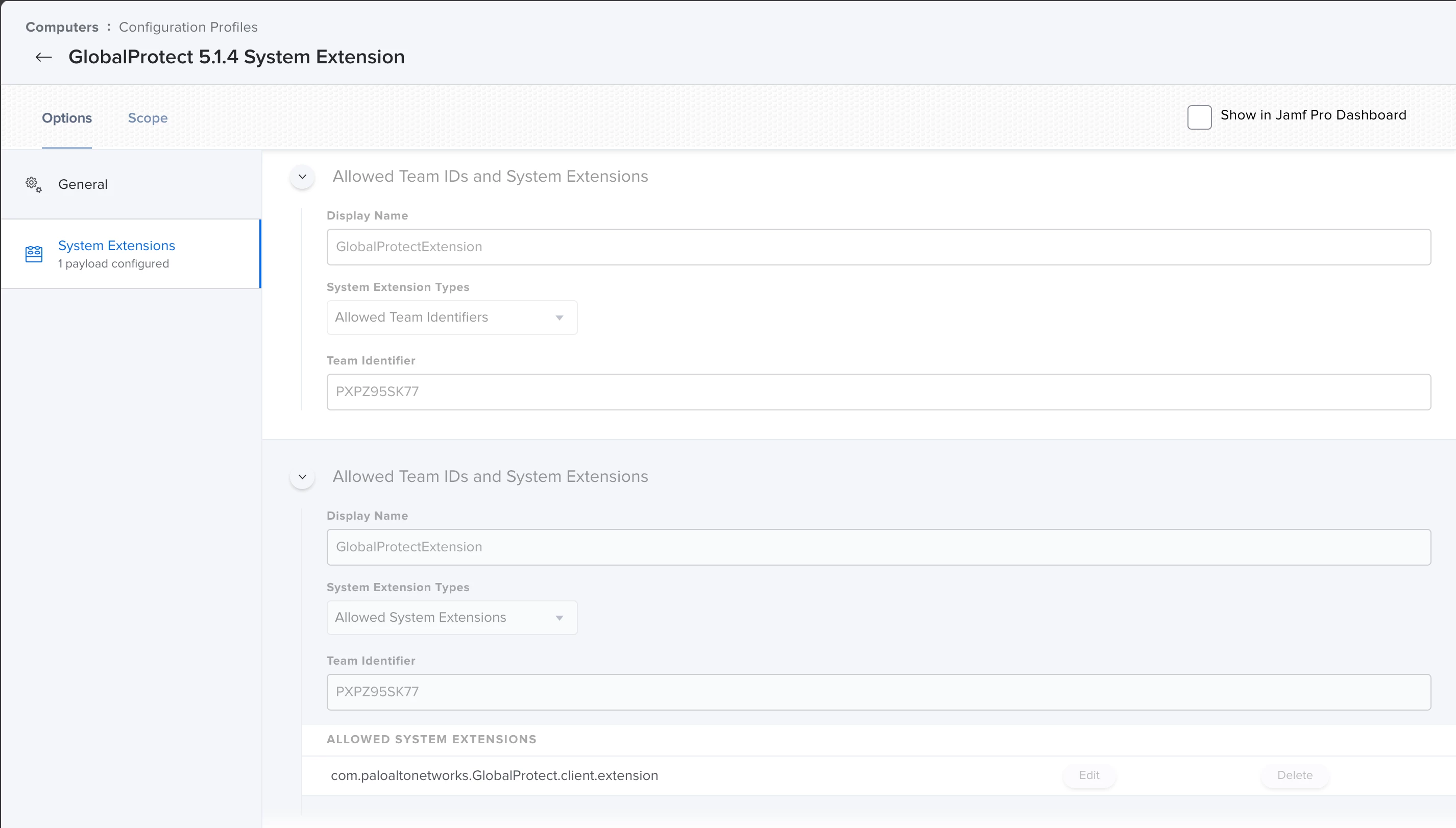
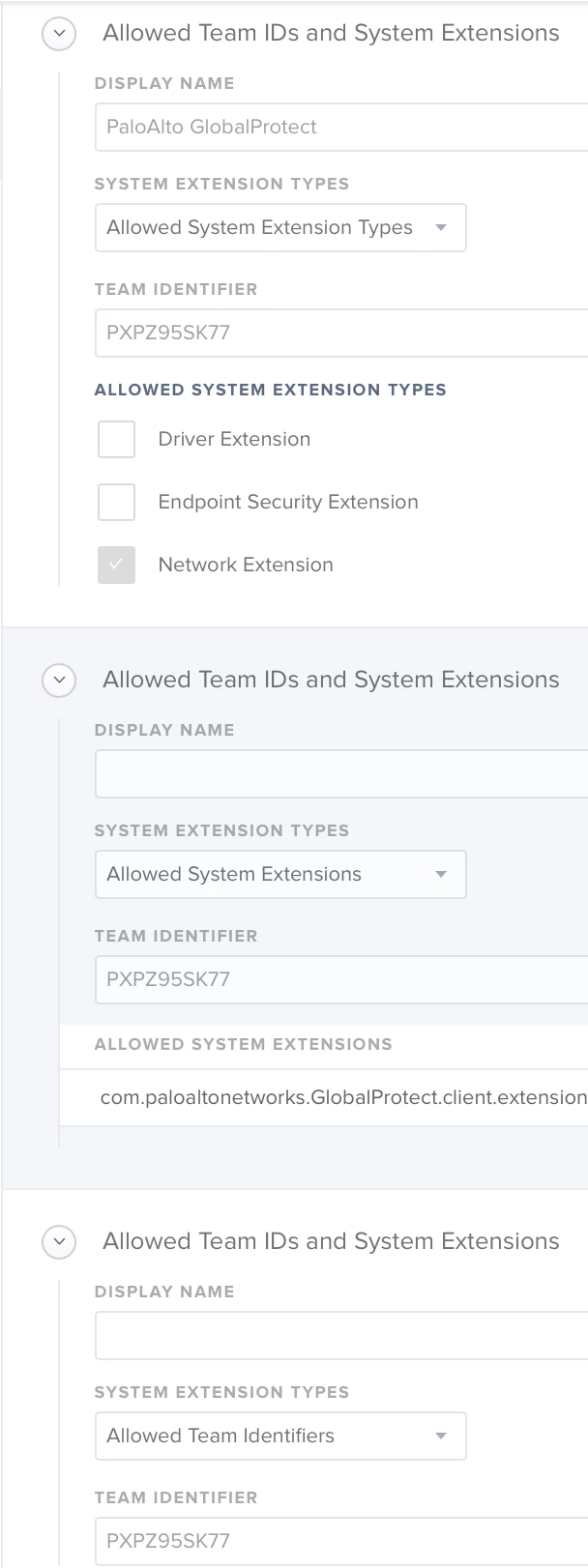
First I tried just the team ID, then I added the ALLOWED SYSTEM EXTENSIONS as well.
but when I run systemextensionsctl list I get
1 extension(s)
--- com.apple.system_extension.network_extension
enabled active teamID bundleID (version) name [state]
* PXPZ95SK77 com.paloaltonetworks.GlobalProtect.client.extension (5.1.4-45/1) GlobalProtectExtension [activated waiting for user]and System Preferences>Security & Privacy still has this prompt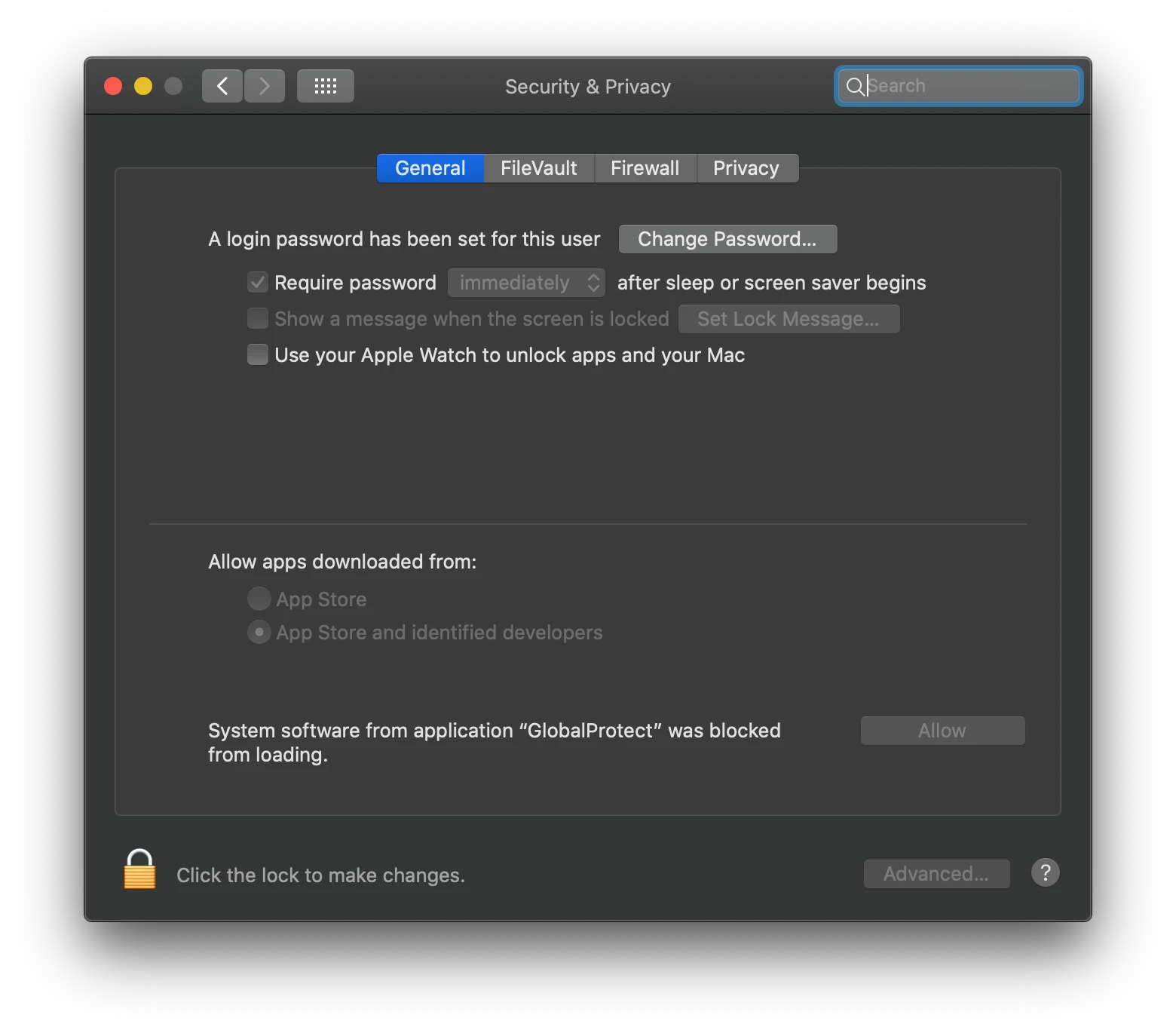
How can I approve this for the user?
I tried a blanket PPPC config profile that just gave it all access, but still have that prompt.
Anyone know how to solve this?