Hi,
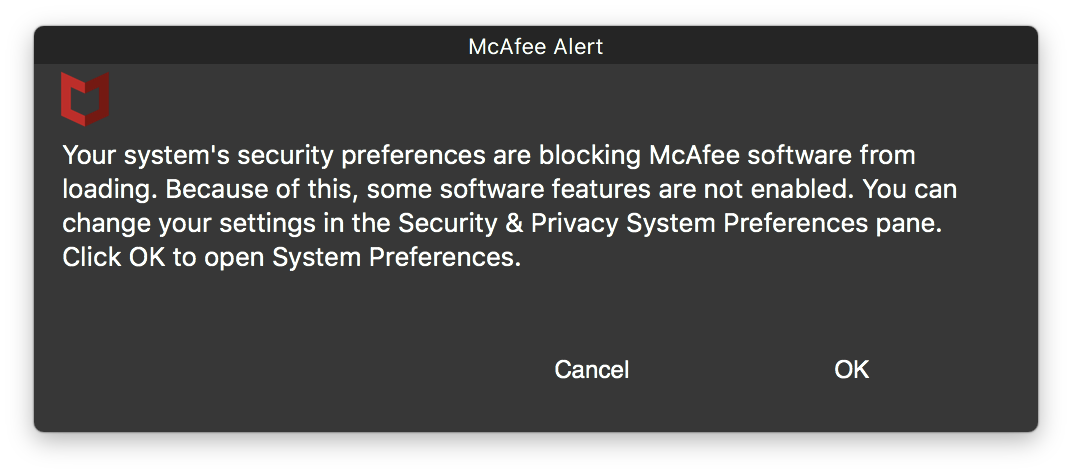
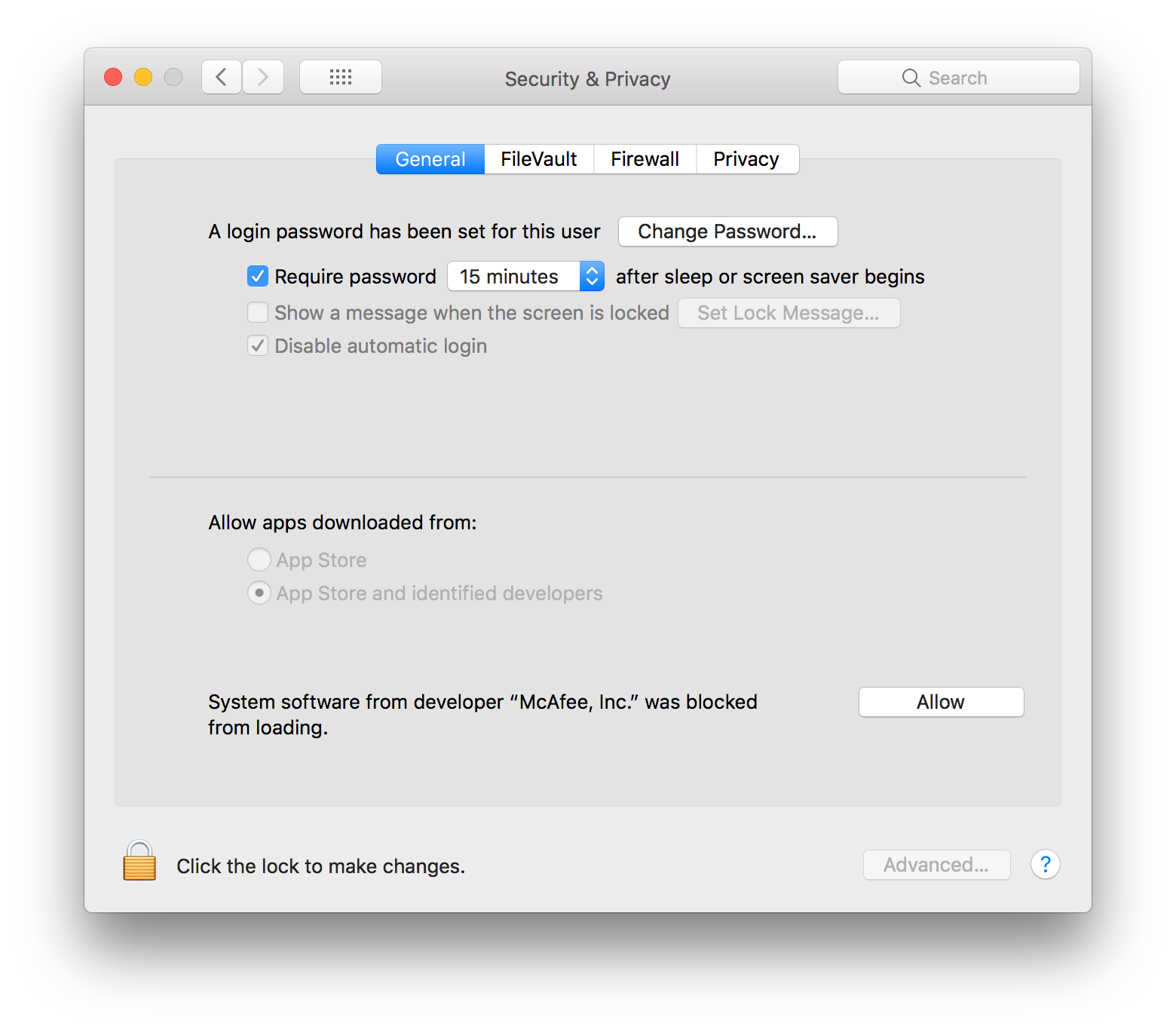
I've been trying to deploy Mcafee EPO on High Sierra. Secure Kernel Extension Loading of High Sierra seems to block it, no matter if I
sudo dpctl --master-disablon machine and "Allow apps downloaded form" change to "anywhere"
the client still needs to Allow this Kernel Extension by manually.
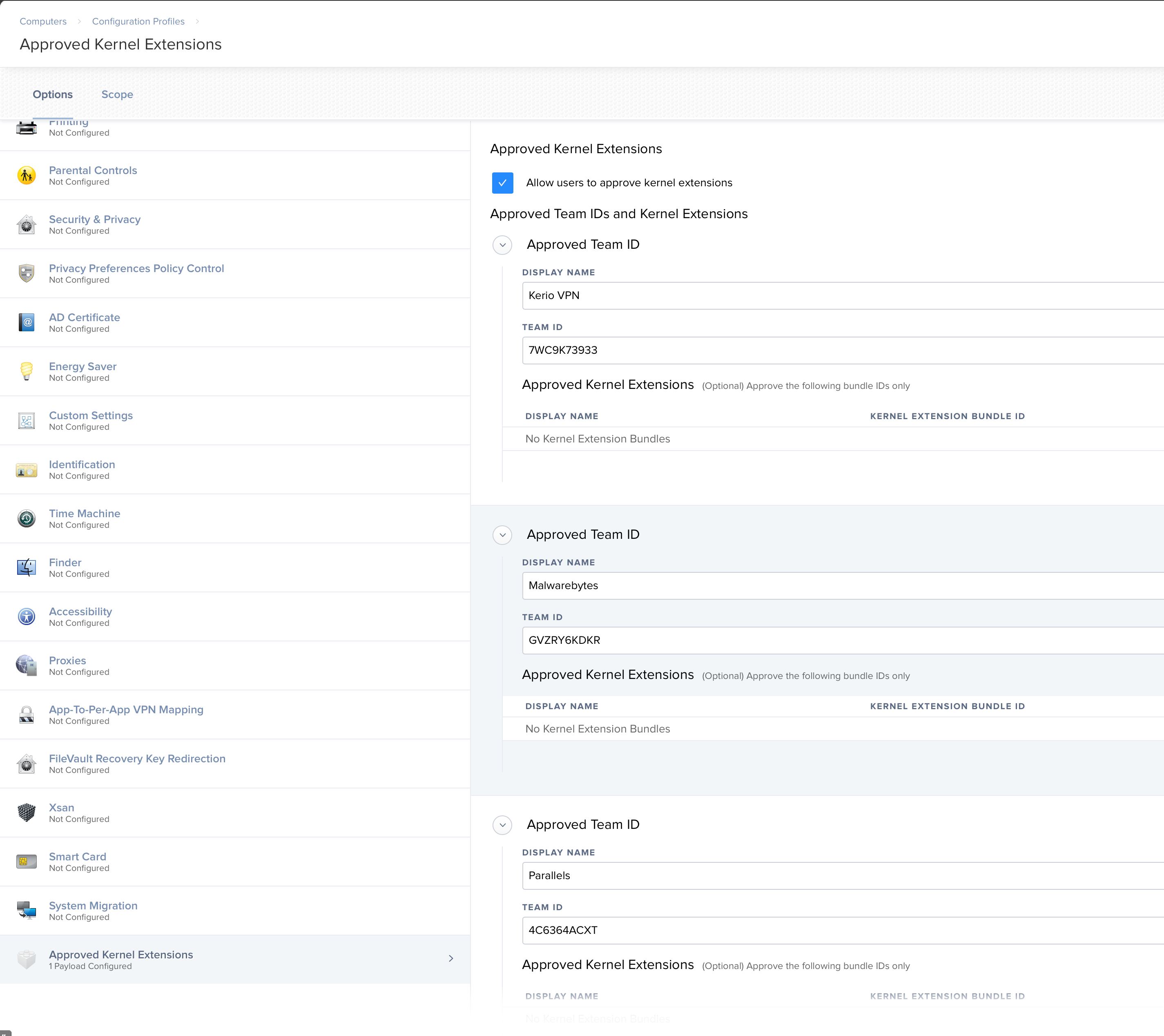
is there any way to allow it by command line or script?
Thanks ,