We are receiving a "Tomcat SSL Certificate Expiring in 20 days" warning.
Apparently, we are using the built-in Certificate authority but since we updated this a long time ago, we aren't sure what to do.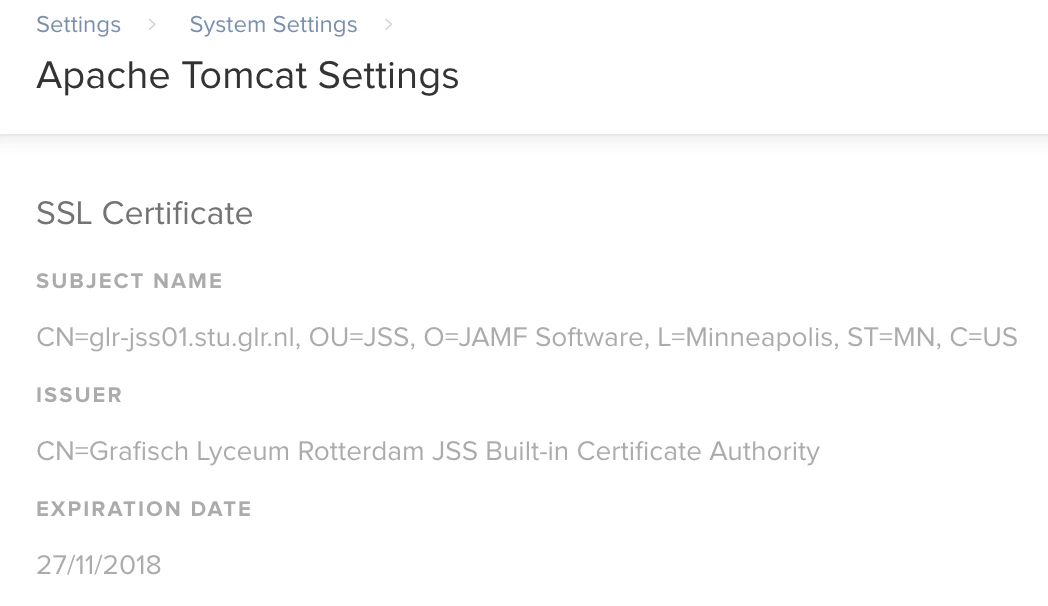
Do we need to choose the first option, since we don't want our clients to lose their connection?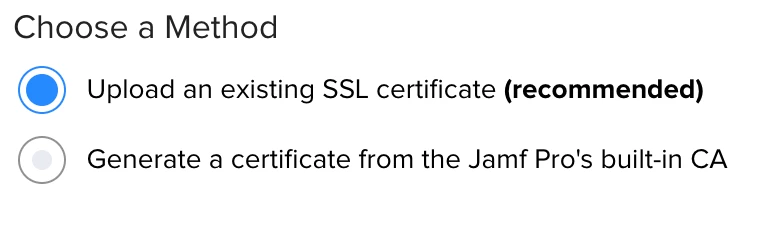
And if so, how and where do we obtain (download) this SSL Certificate Keystore for uploading into the JSS?
Your help is appreciated.









