Hey all,
I'm researching this, but in the interest of not reinventing the wheel, I thought I'd ask the nation...
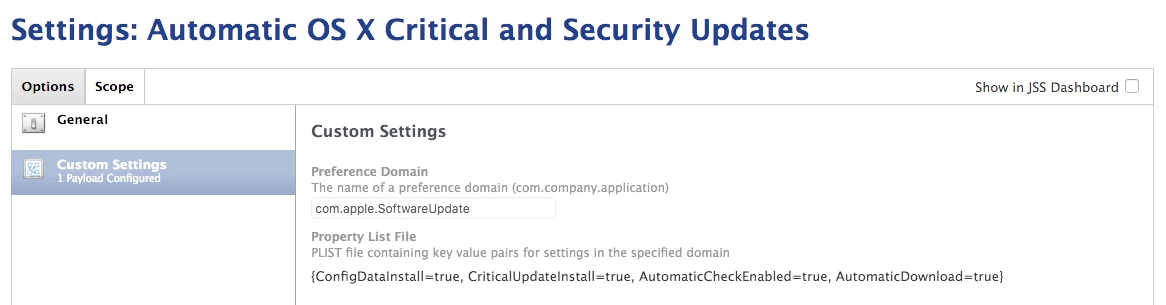
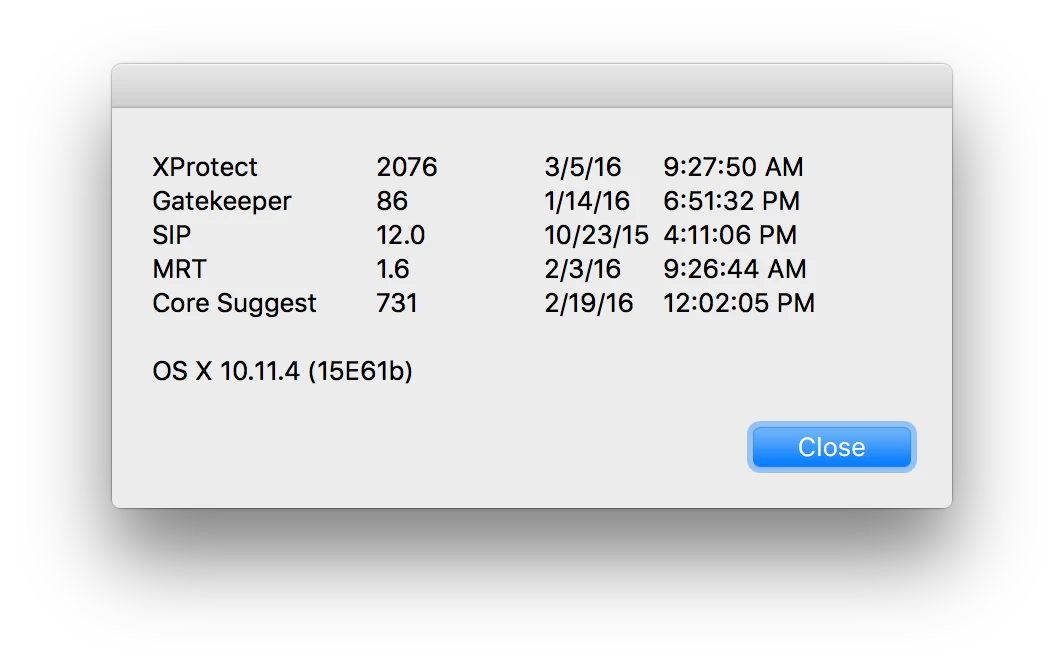
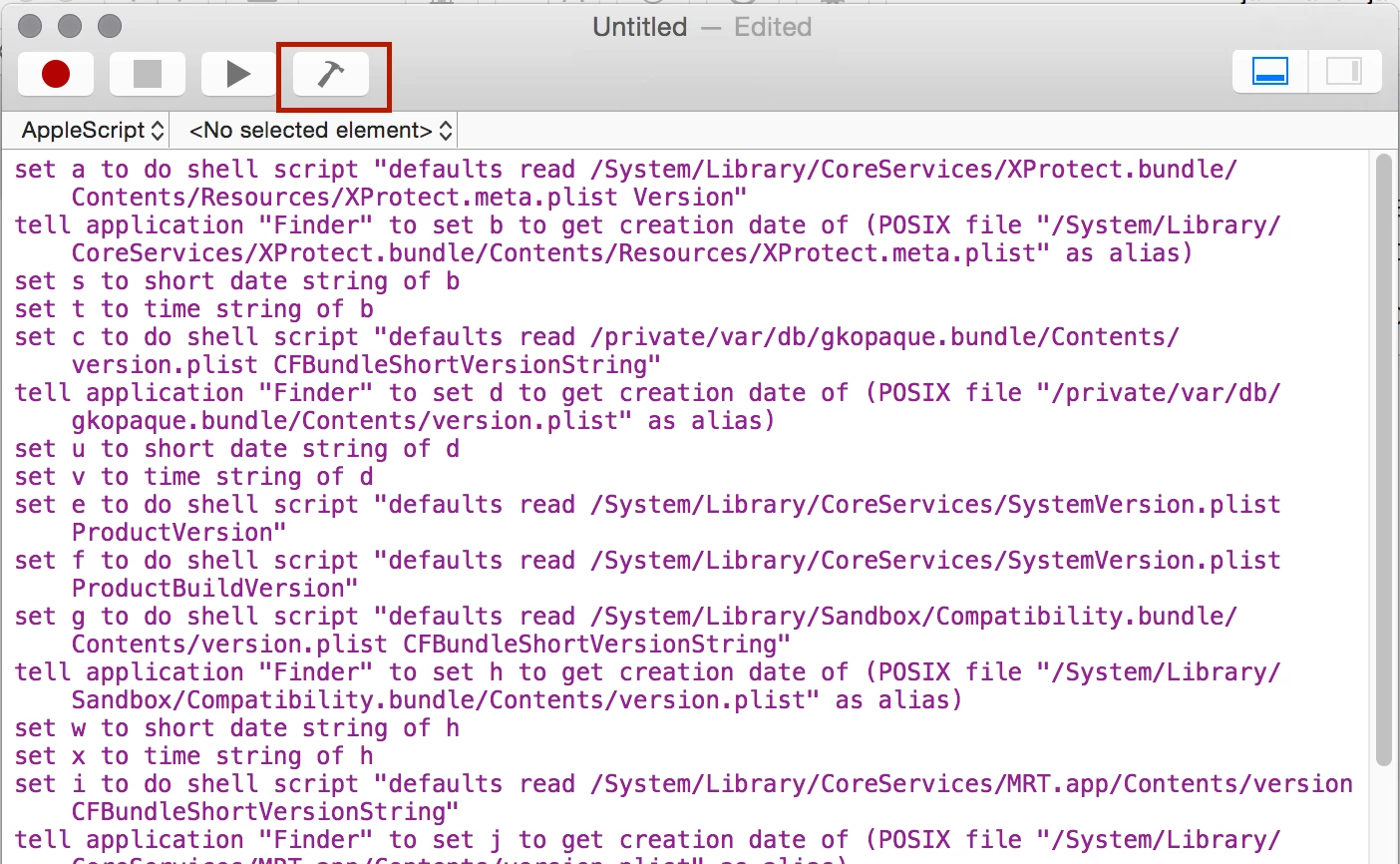
The Xprotect Status extension attribute posted here returns the following on 10.11.3:
The domain/default pair of (/System/Library/CoreServices/CoreTypes.bundle/Contents/Resources/XProtect.meta, LastModification) does not existI've looked through the file referenced and there's no instance of a date or the words "modified," "modification," change," or "update" in the XML. Does anyone know where to look for the last Xprotect update?