For those of you who wake up to Zoom Exploit news.
You can set ZoomOpener.app as a Restricted Software.
Kill Process
Restrict to exact process name
Kill Process.
I would not recommend turning on Send Email or Message to the user.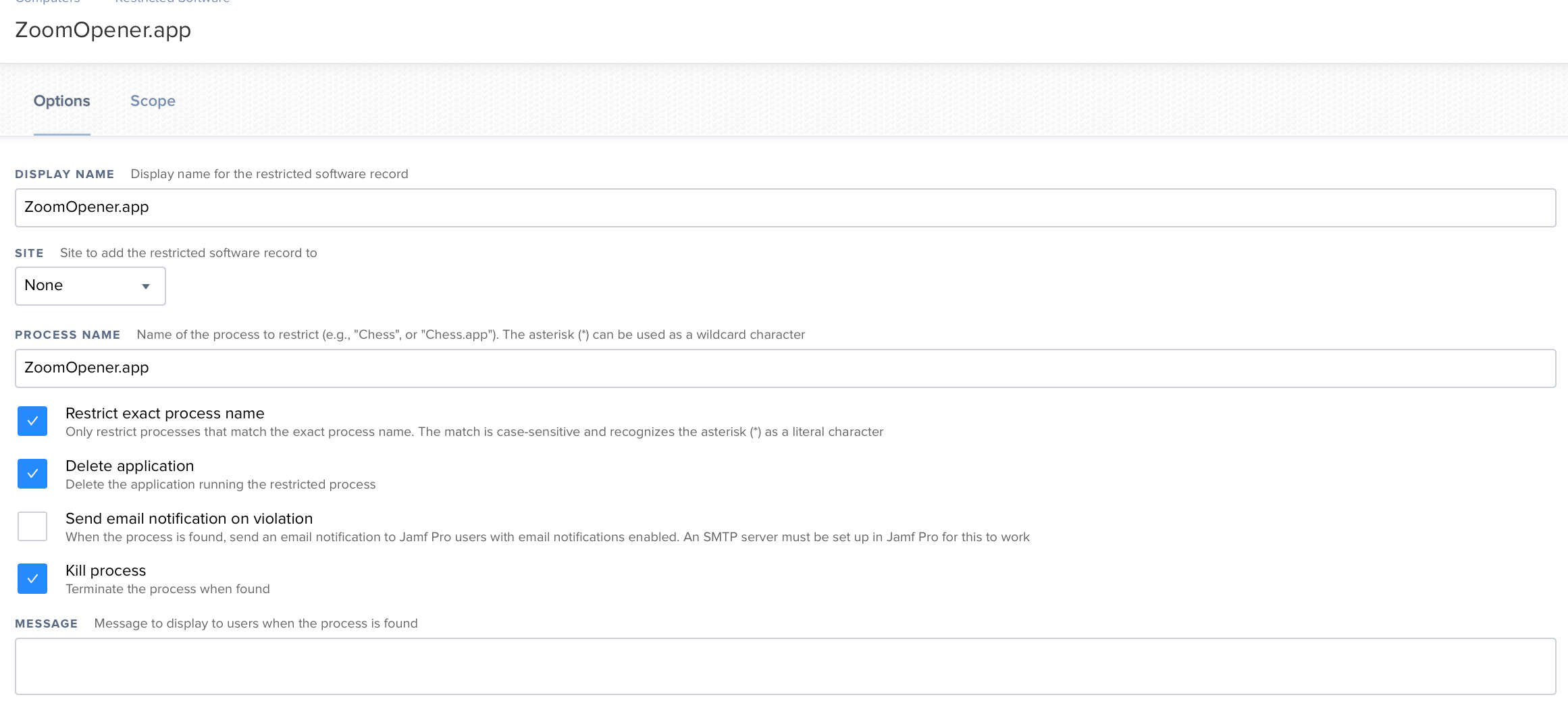
 +3
+3For those of you who wake up to Zoom Exploit news.
You can set ZoomOpener.app as a Restricted Software.
Kill Process
Restrict to exact process name
Kill Process.
I would not recommend turning on Send Email or Message to the user.
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.