This page consolidates the links and code samples referenced in the JNUC 2019 presentation "A Deep Dive into Deploying Jamf Connect."
Links to Guides:
Jamf Connect Evaluation Guide
Jamf Connect Administrators Guide
Flowchart - Places where a user may interact with a password: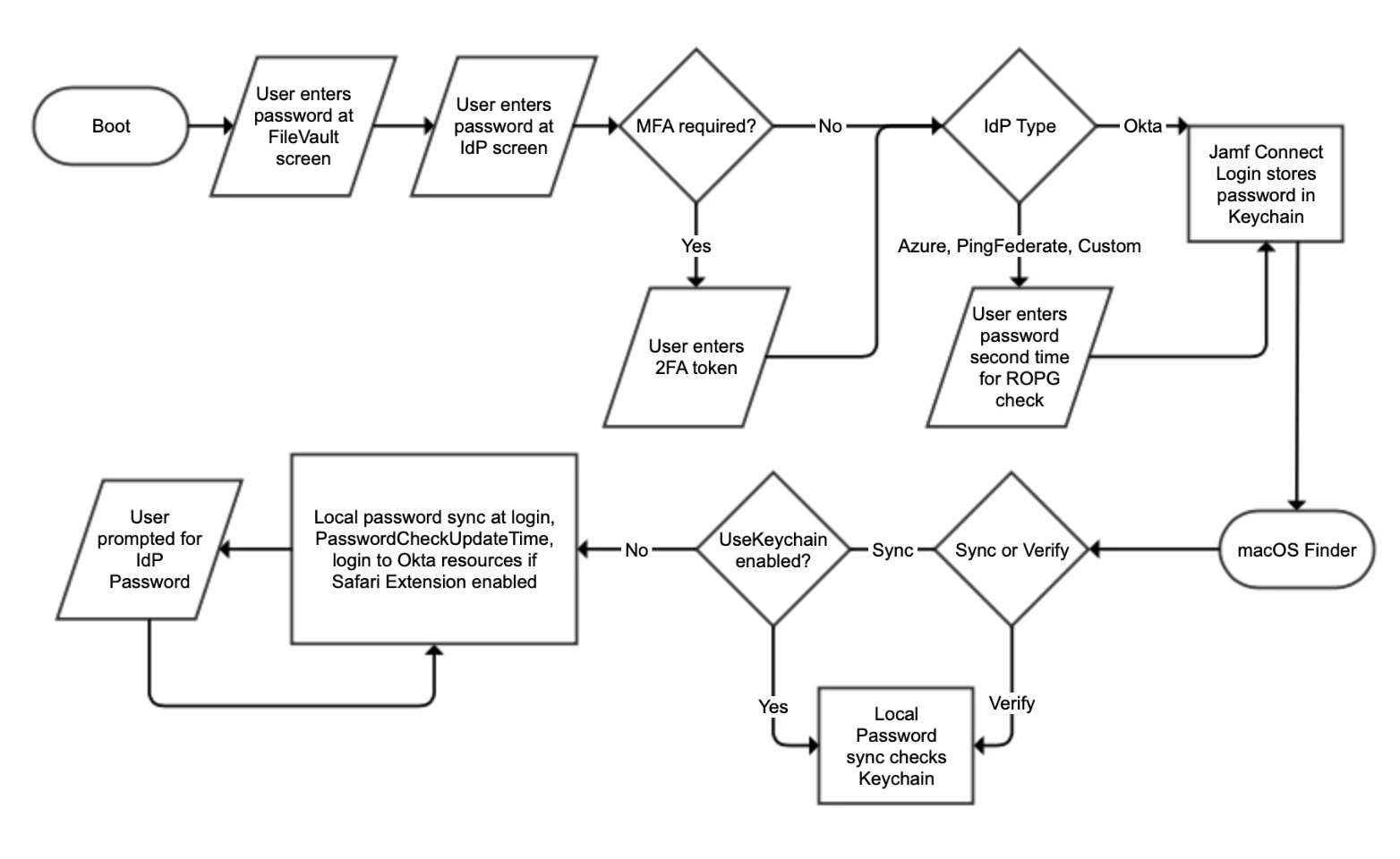
Using Jamf Connect with ADFS and Azure AD Guides:
Configuring Jamf Connect with Azure AD Hybrid Identity Solutions
Understanding Jamf Connect Authentication with Azure AD Hybrid Identity Solutions
IdP Compatibility Guide:
IdP Compatibility
Example of starting Jamf Connect Verify and Sync with the -v for verbose logging:
#!/bin/sh
/Applications/Jamf Connect Sync.app/Contents/MacOS/Jamf Connect Sync -v
/Applications/Jamf Connect Verify.app/Contents/MacOS/Jamf Connect Verify -vCapture logs in real time with Jamf Connect Login:
#!/bin/sh
log stream --predicate 'subsystem == “com.jamf.connect.login"'
—debug --info >> /path/to/file.txtLocation of logs from last login with JCL: /private/tmp/jamf_login.log
Command to trigger loginmechanism while logged in as a user:
#!/bin/sh
sudo security authorize system.login.consoleFileVault Login Considerations - aka why do I not see the Jamf Connect Login screen:
Using FileVault with Jamf Connect
Sample postinstaller script for a zero touch workflow prestage enrollment metapackage:
#!/bin/bash
# postinstall script for:
# Jamf Combo Installer for DEP Prestage
TMP_PATH=/private/tmp
LOGIN_FILENAME=JamfConnectLogin-x.pkg
VERIFY_FILENAME=JamfConnectVerify-x.pkg
SYNC_FILENAME=JamfConnectSync-x.pkg
# Install Login
installer -pkg "$TMP_PATH"/"$LOGIN_FILENAME" -target $3
# if Okta installation, use this command:
# installer -pkg "$TMP_PATH"/"$SYNC_FILENAME" -target $3
# FANCY VERSION: Okta with EULA and post login script with Notify mechanism
# /usr/local/bin/authchanger -reset -Okta -DefaultJCRight -preAuth JamfConnectLogin:EULA JamfConnectLogin:RunScript,privileged JamfConnectLogin:Notify
# BASIC VERSION: Just Okta Login. No scripting or EULA.
# /usr/local/bin/authchanger -reset -Okta
# If OIDC provider, use this command:
installer -pkg "$TMP_PATH"/"$VERIFY_FILENAME" -target $3
# FANCY VERSION: OIDC with EULA and post login script with Notify mechanism
# /usr/local/bin/authchanger -reset -OIDC -DefaultJCRight -preAuth JamfConnectLogin:EULA JamfConnectLogin:RunScript,privileged JamfConnectLogin:Notify
# BASIC VERSION: Just OIDC Login. No scripting or EULA.
/usr/local/bin/authchanger -reset -OIDC -DefaultJCRight
# Use the killall command to make sure that a slow network connection will kill the standard macOS login window after the pkg has fully installed.
/usr/bin/killall -9 loginwindow
exit 0 ## Success


