Hey guys. Bare with me, I have taken oven my company's JAMF environment and have now faced some issues.
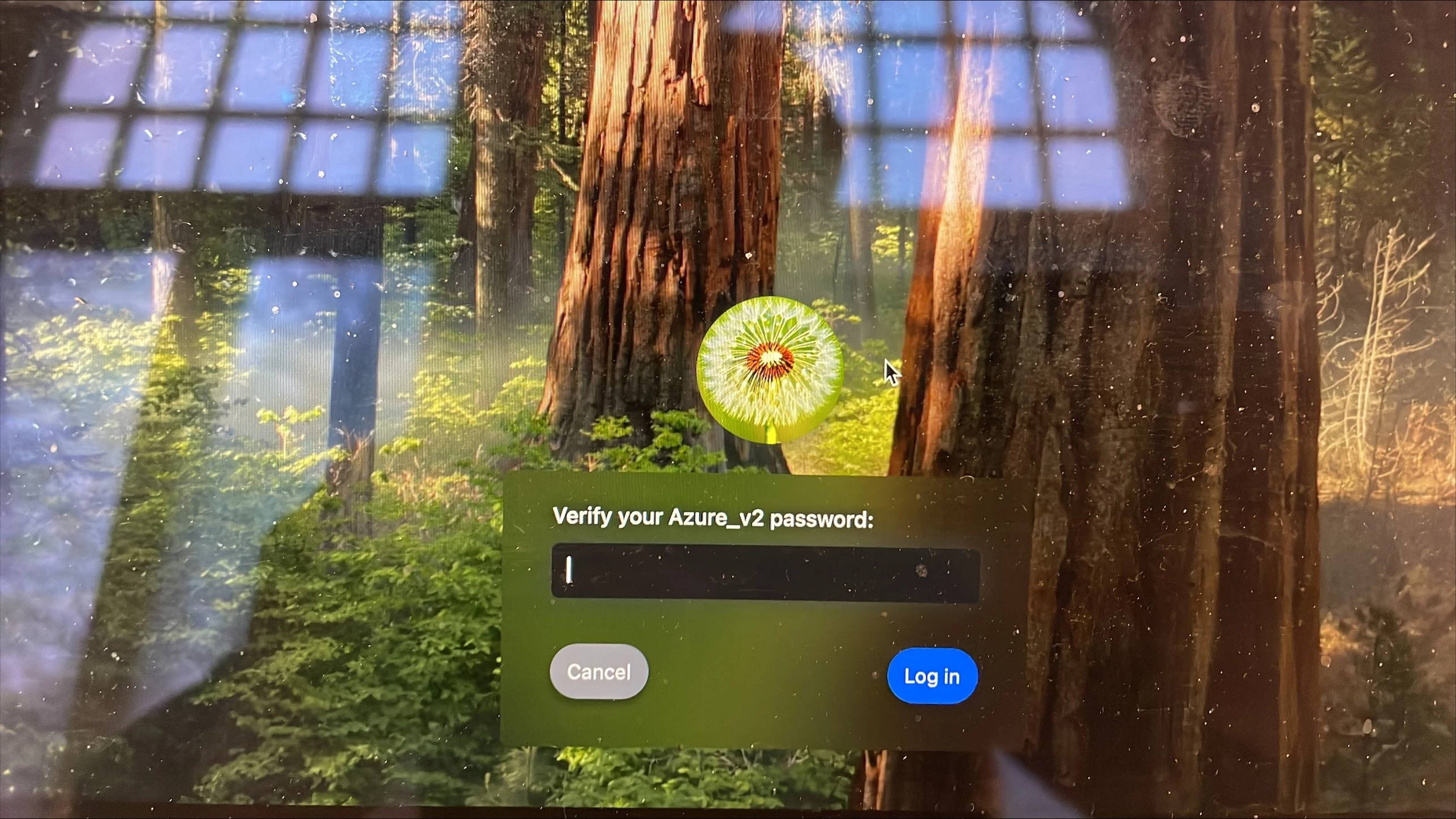
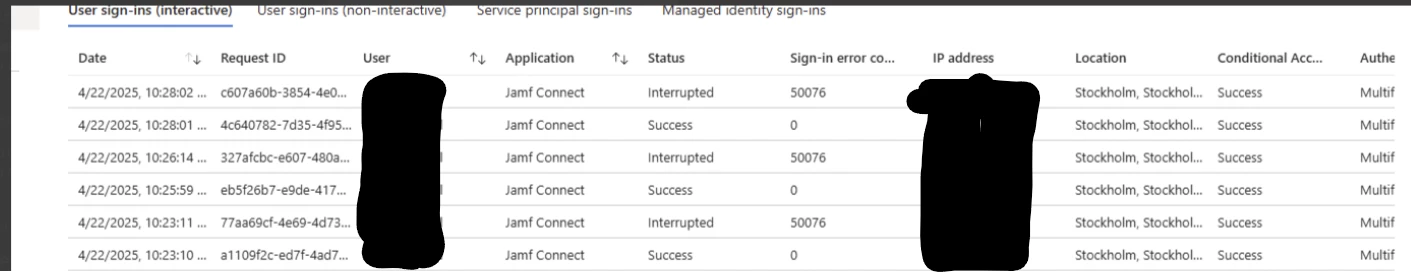
When logging in to the computer they type in their company email + password then authenticate with MFA. When this is done they face this window "Verify your Azure_V2 password:" and they type in their password and log in. This usually works. But now we have faced issues with user not coming through this step, they are "bounced" back to 365 log in window.
This is something pretty new, maybe something changed in azure - but not sure how to remove this step. We have "Passtrouh authentication with Jamf Connect"