Hello everyone
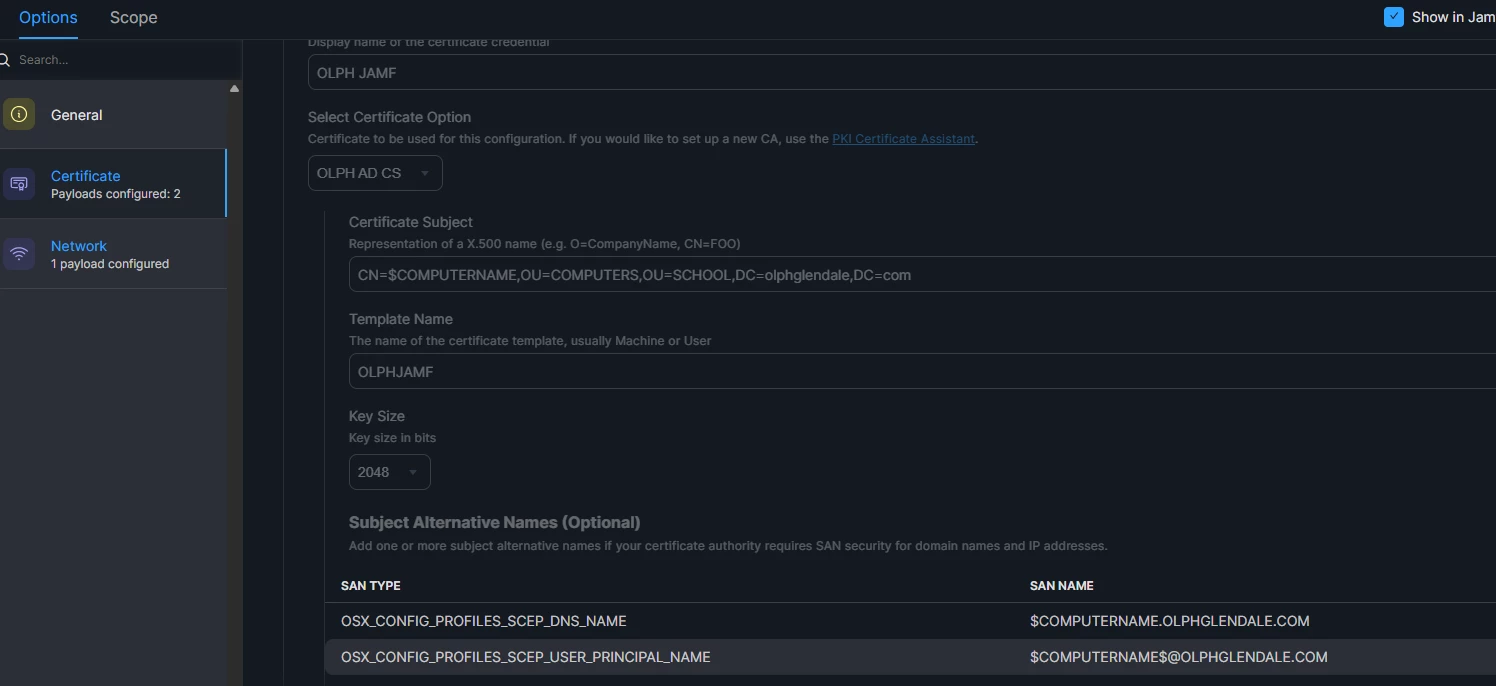
My context: wi-fi authentication based on 802.1x through a Windows Server (NPS). Computer certificates are deployed by Jamf (Configuraton Profile) and through the Jamf ADCS connector.
Macs are not bound to the Windows domain but a computer object is created for every laptop (it's mandatory with a NPS server).
Everything is working as intended.
As you may know, in may 2022 Microsoft published an important security update that changes the way certificates are validated by domain controlers.
https://support.microsoft.com/en-us/topic/kb5014754-certificate-based-authentication-changes-on-windows-domain-controllers-ad2c23b0-15d8-4340-a468-4d4f3b188f16
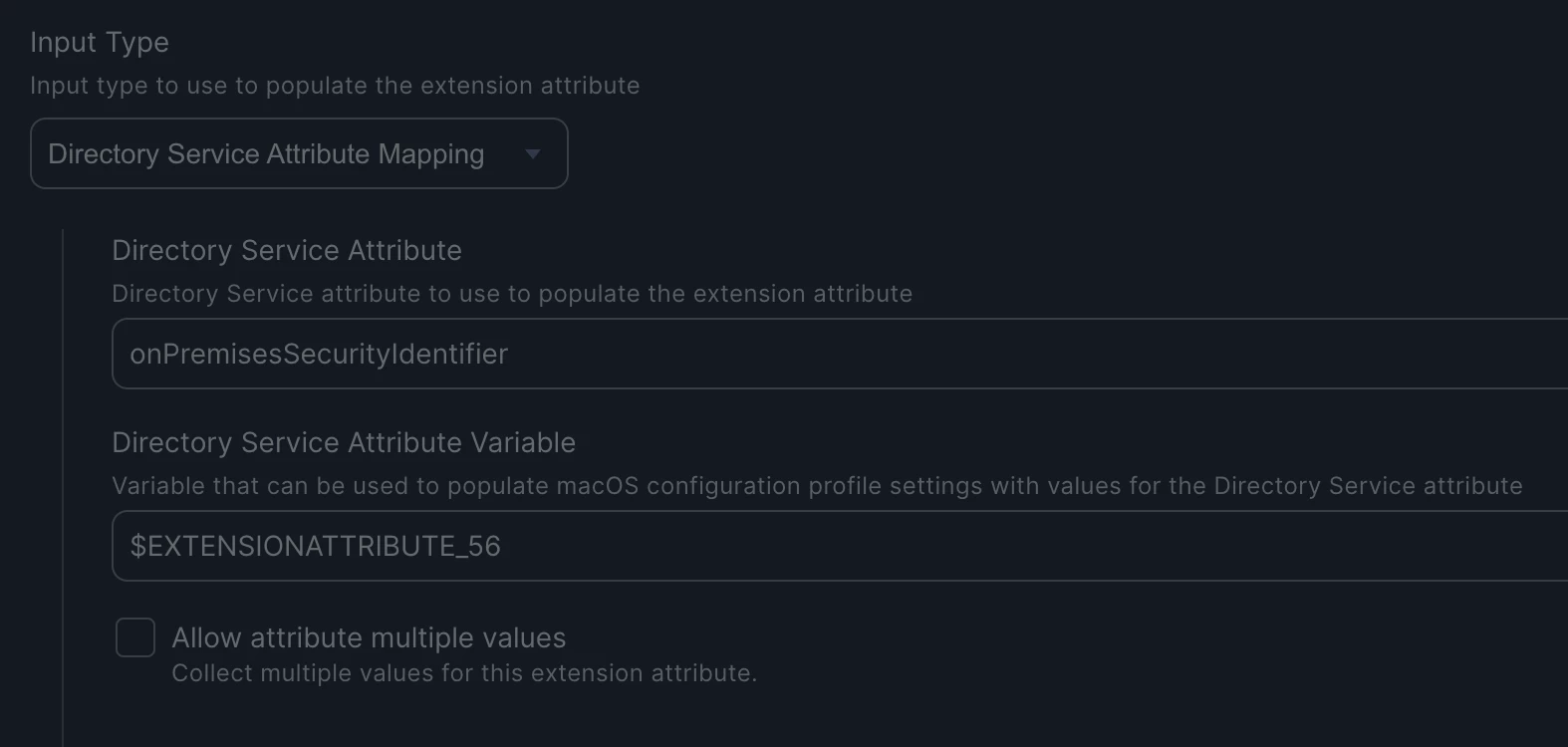
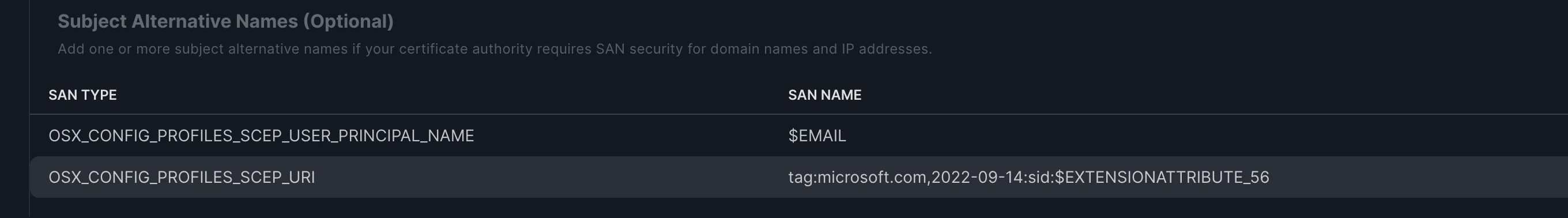
A new extension identified by the OID "1.3.6.1.4.1.311.25.2" is now included in certificate templates, but only for the ones that build the subject information from Active Directory.
Unfortunately, certificates issued through the Jamf connector are "offline", meaning that the subject information (CN, DNS name) are supplied in the request (the settings come from Configuration Profile). And Microsoft has not updated this template (yet?). I guess that Jamf will have to modify the Configuration Profile options as well.
As soon as you update your Domain Controlers, Macs are no more able to connect to the wi-fi because their certificates do not include the OID "1.3.6.1.4.1.311.25.2" (and values based on computer object SID).
How do you deal with this restriction, please ?
Do you manually map certificates to object in AD (as referenced in the MS link above) ?
I do not want to bypass the security by tweaking the registry and placing domain controlers in Disabled mode (this option will be removed on February 14, 2023)
I'm stuck at the moment and I'm searching the best solution to keep the automation (certificates deployment) as easy as it is currently.
Best