Hey there,
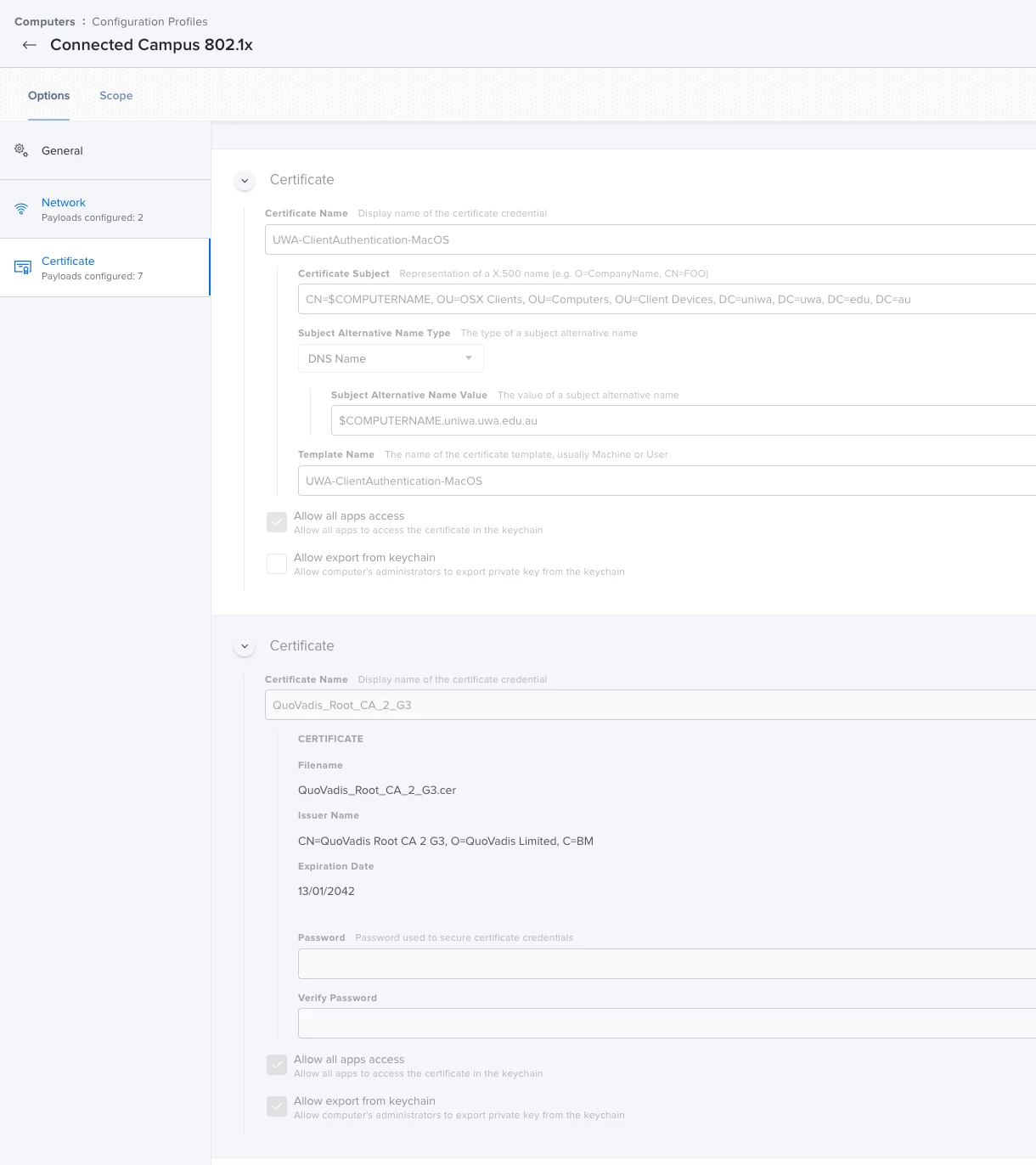
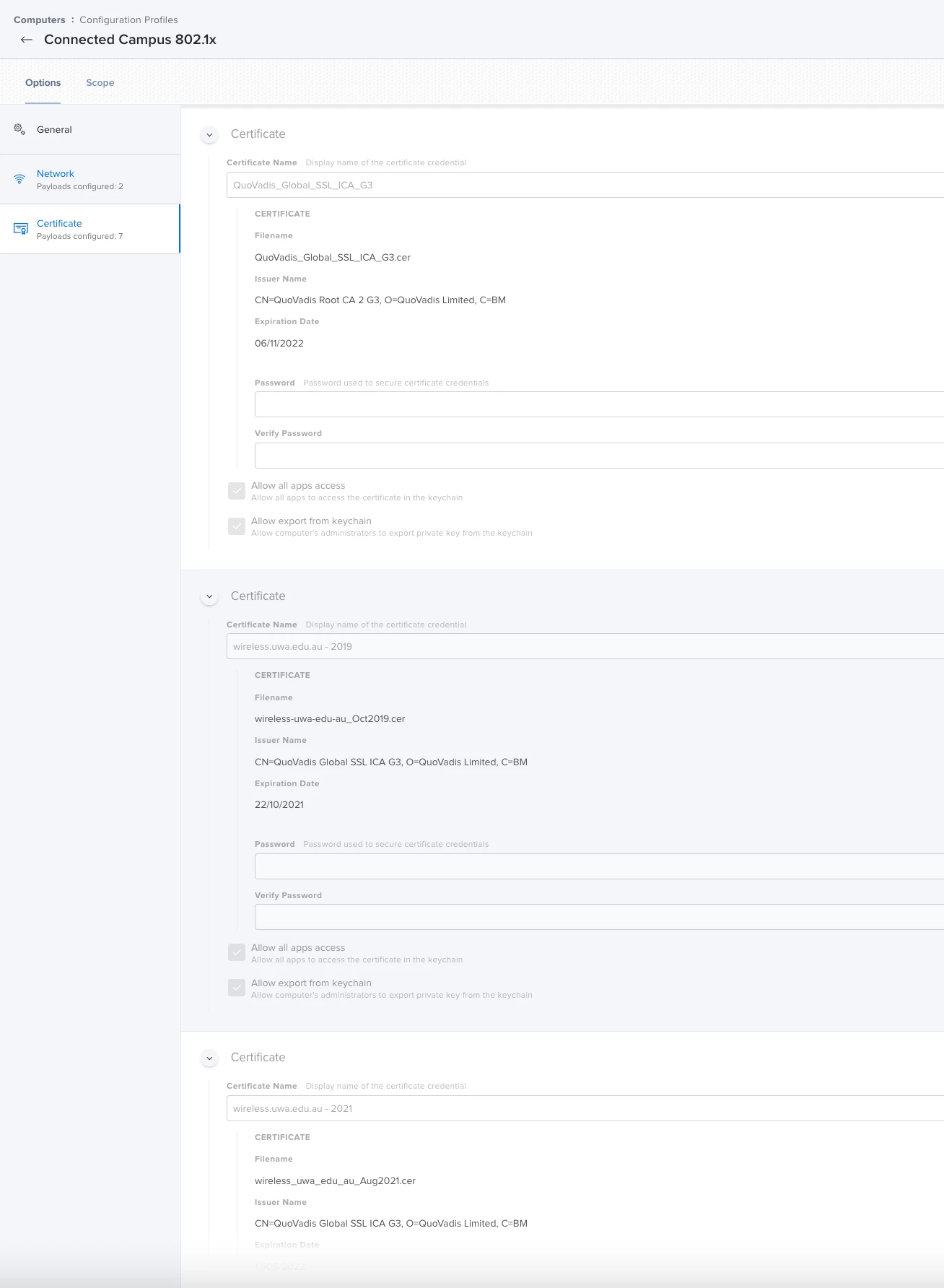
I am trying to get the mac laptops to use certificate based logons for 802.1x. The machine can join to the AD domain, it can generate a certificate and i see that certificate on the machine. However when i try and apply a jamf profile to add the certificate and wireless profile to connect to the network i get the following errors:
mschap: FAILED: No NT/LM-Password. Cannot perform authentication
Login incorrect (eap: Failed continuing EAP TTLS (21) session. EAP sub-module failed): [MS\\lmc02d<FULLHOSTNAMEREMOVED>
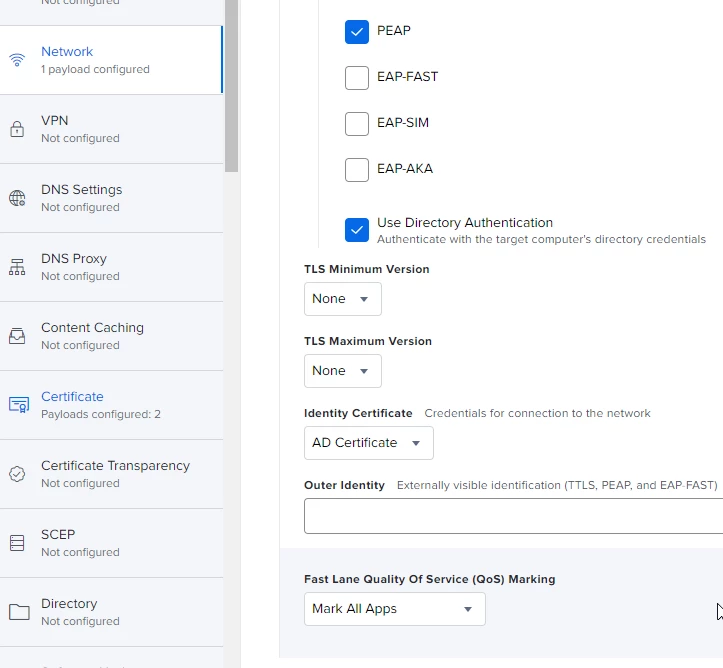
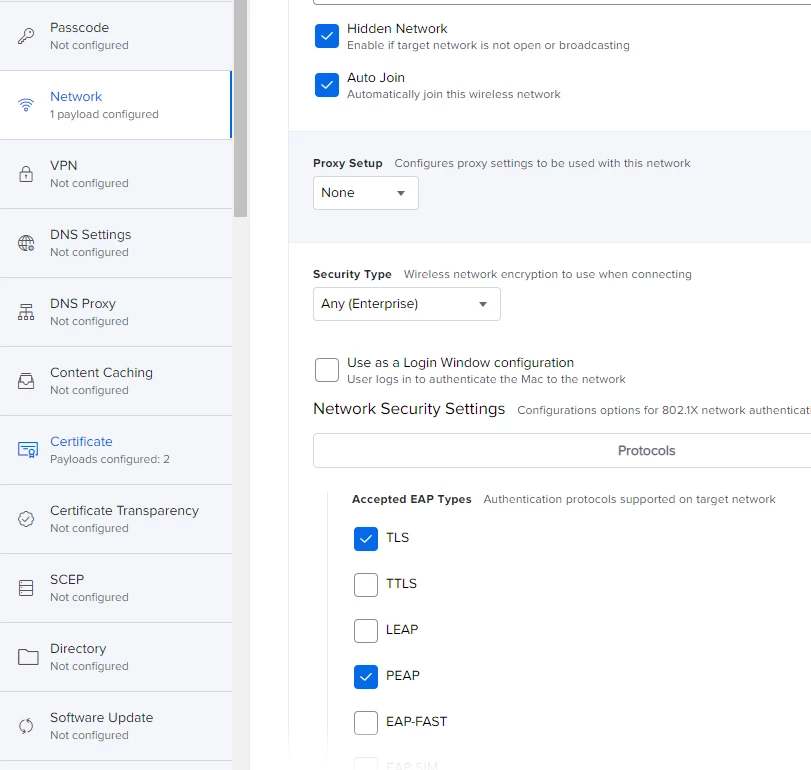
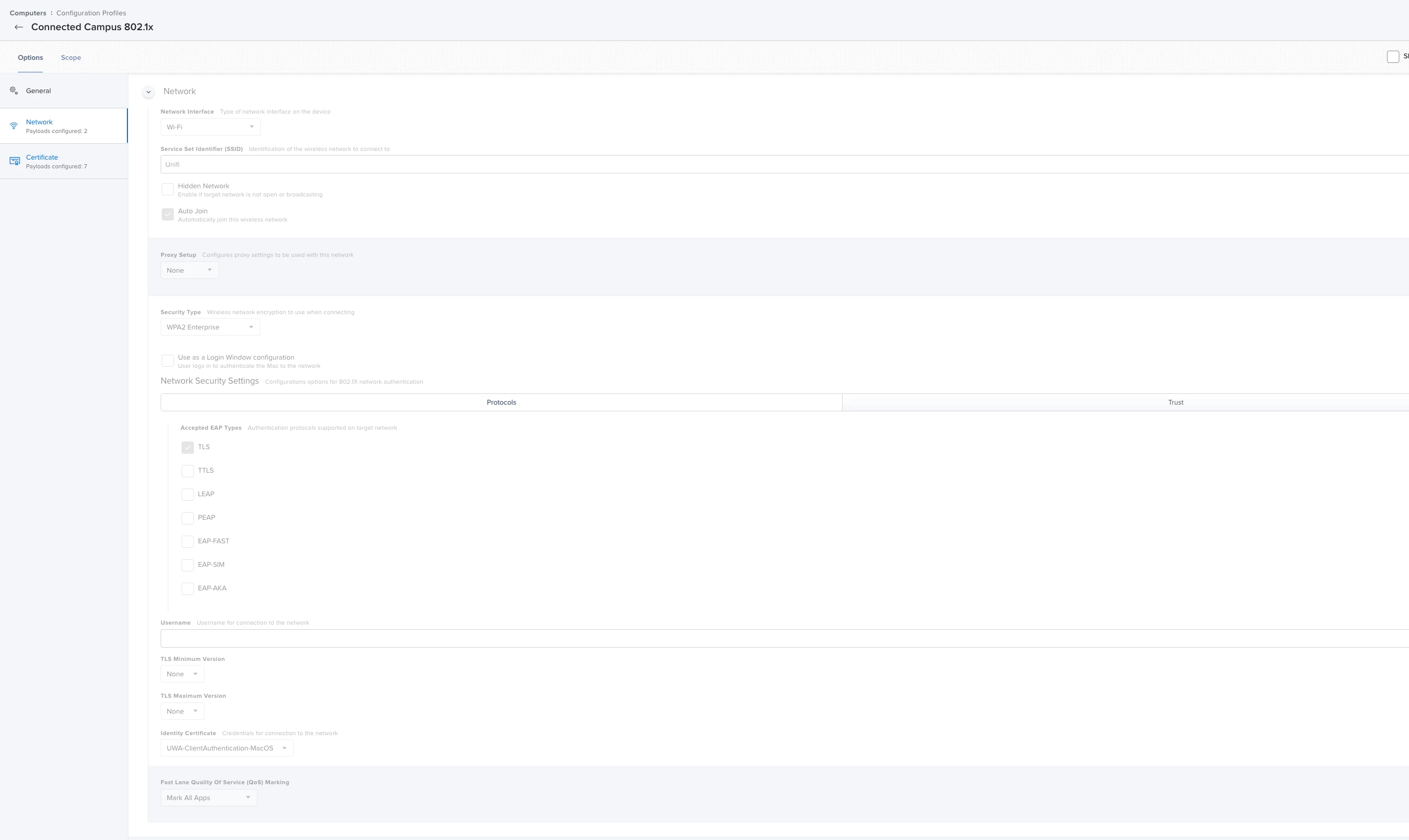
I have tried with PEAP as well as TTLS. On the windows laptops i have connecting using the same infrastructure, they connect fine and do not require any password. What is the point of certificate based logons that require a password? Makes no sense. But jamf / macs appear to need something there. Its very possible my jamf config is the problem here.
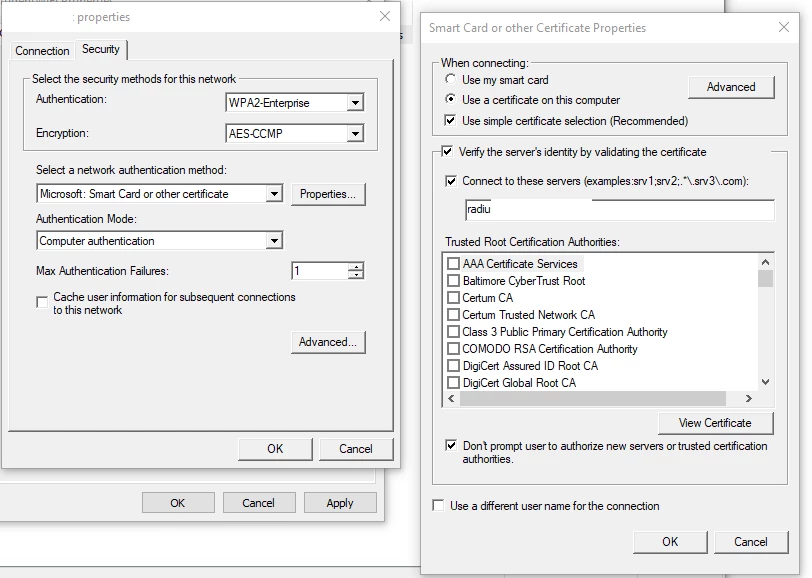
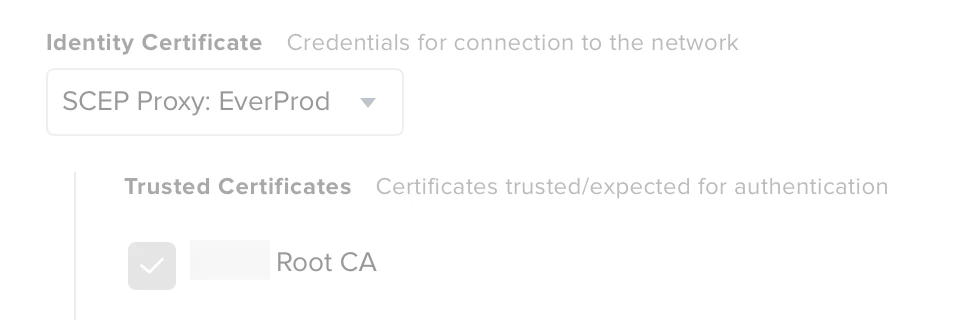
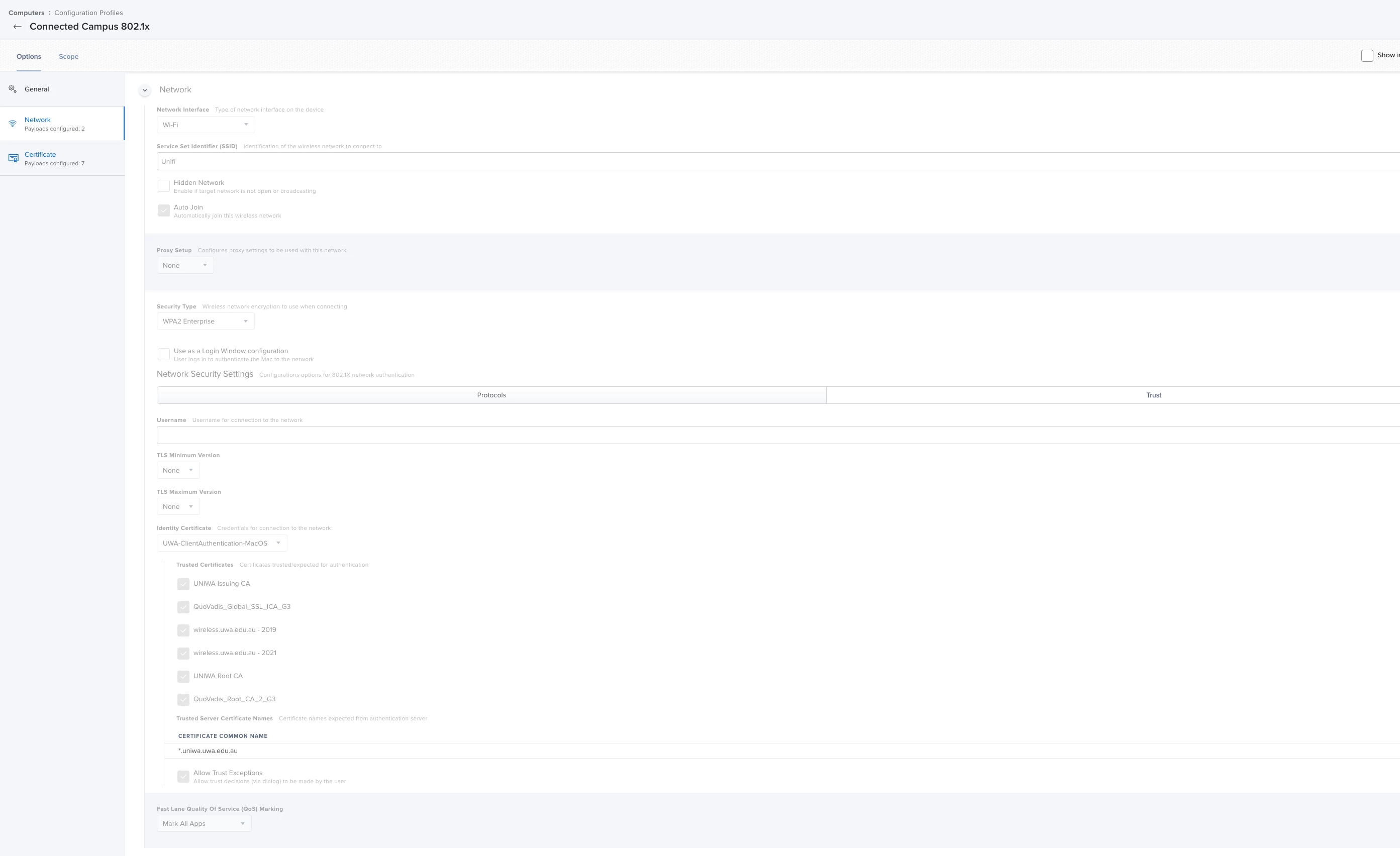
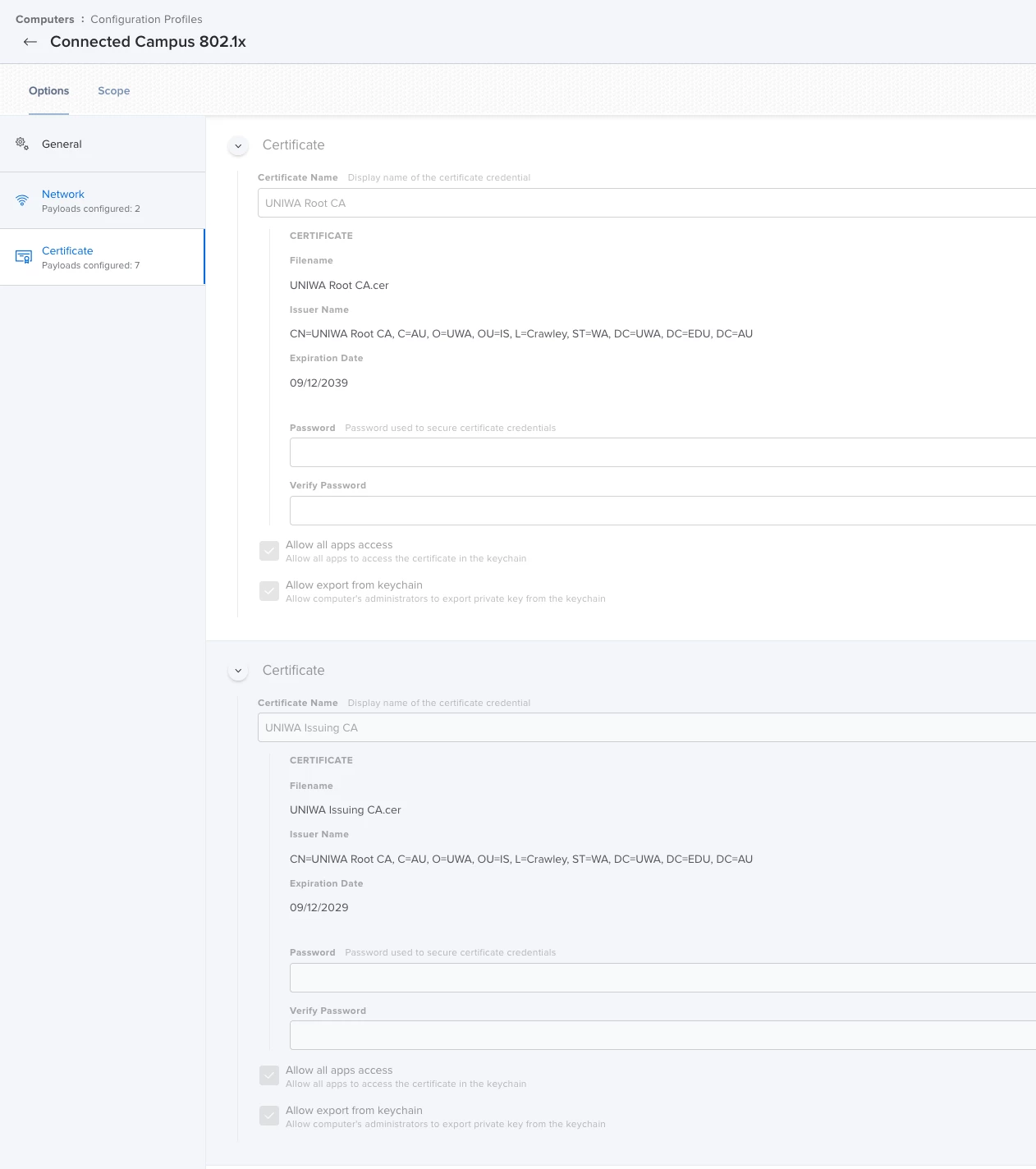
The domain root certificate is SHA-256, and is added to the same profile and trusted on the trust tab. I also put in the names of the radius server and the CA, and allowed trust exceptions.
I have tried all the different auth protocols and the error message changes, but the results are the same.
I have included the windows settings from group policy that do work without issue.