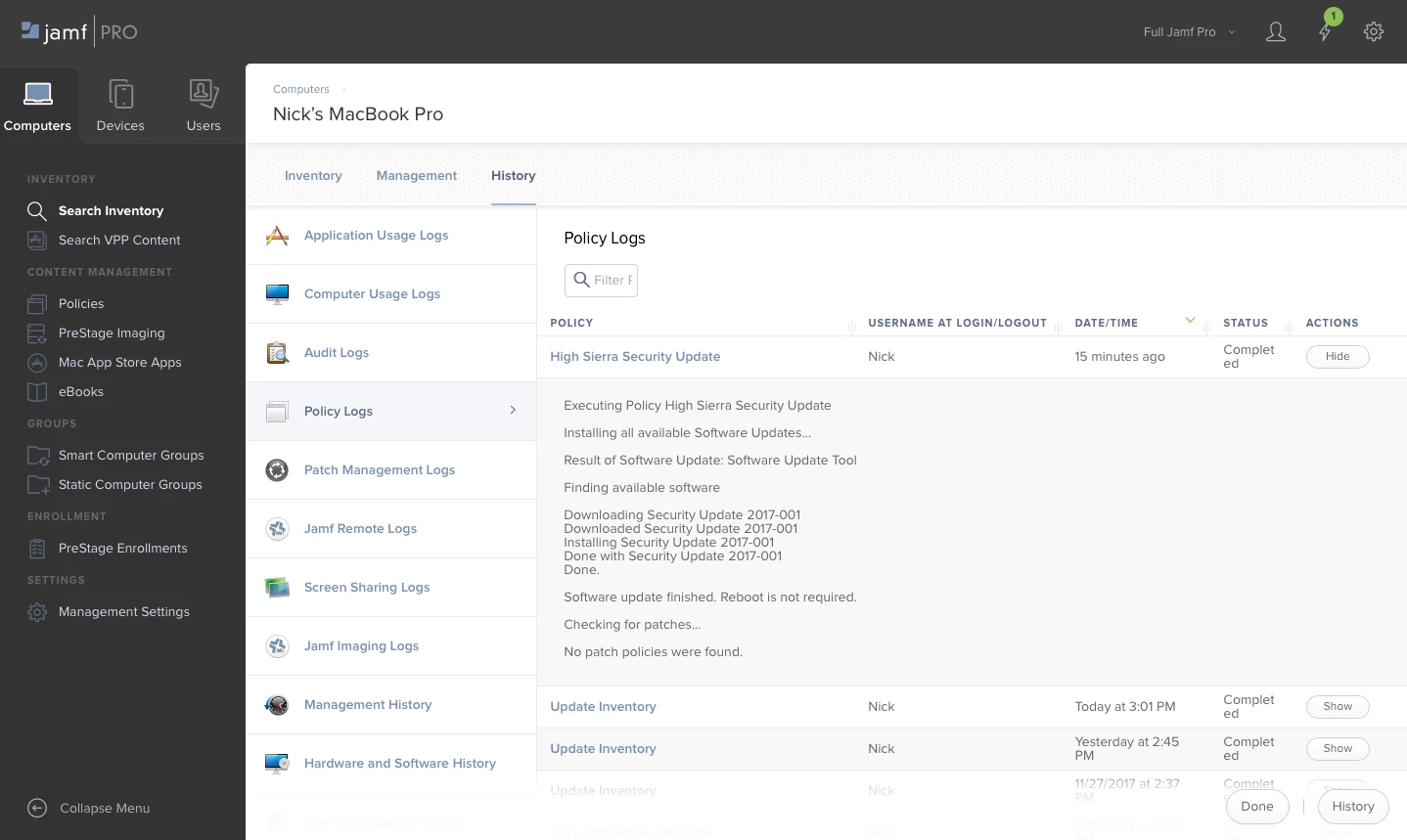
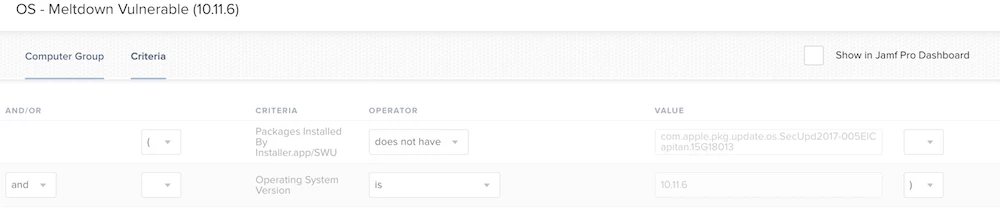
Apple has released a Security Update for High Sierra (HT208315), and Jamf recommends anyone with High Sierra run it as soon as possible. For a full description of the security update visit: https://support.apple.com/en-us/HT208315.
This particular security vulnerability allows a user or attacker to gain access to a Mac with default settings sans a password. In addition, this issue also allows standard users to gain elevated privileges in System Preferences, access via a script, and most importantly at the Login Window.
Why does this matter? All Mac devices have what’s known as a root account, or a super-user account that has access to the internals of any Unix or BSD-based operating system. The issue is made possible by the fact that the root account has a blank password and can login prior to the update being run. This issue requires physical access to a device or remote access via a tool like Apple Remote Desktop.
- In general, the root account should not be enabled unless it’s being used. To disable this manually, use https://support.apple.com/en-us/HT204012.
- There is a Jamf Nation community discussion addressing this, available at: https://www.jamf.com/jamf-nation/discussions/26290/vulnerability-10-13-root
Screenshot of Jamf Pro with patch applied.