For some years now we've been encountering the odd mac where even though newly-enrolled, the local admin password does not work. With no way to login, we were reduced to Recovery Console, wipe and re-enroll. To mitigate this we created a backup admin account to allow us a way in, but with the advent of Secure Token things have got weirder. Has anyone experienced this? Here is our setup:
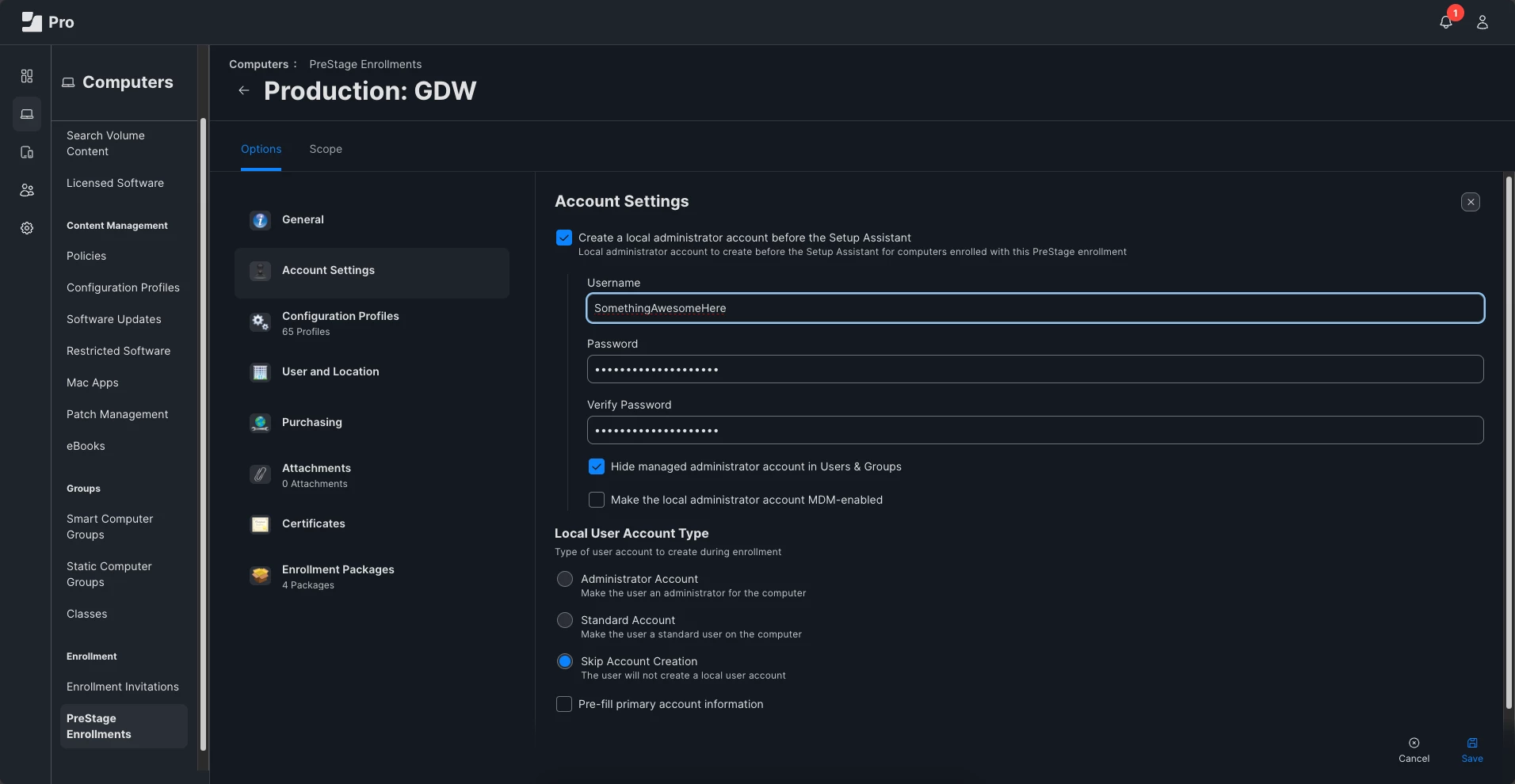
1. Our student macs are enrolled with a prestage where a single local admin account "Admin1" is created before setup assistant.
2. A Jamf policy then creates a second admin account, "Adminbak".
3. Setup assistant does NOT create a local account, instead we later bind the macs to ADS and network users then logon. Adminbak was created to be the first account created after setupassistant, so it would get Secure Token. Our onsite techs can then logon to each machine with Adminbak to enable bootstrap.
Here are our symptoms:
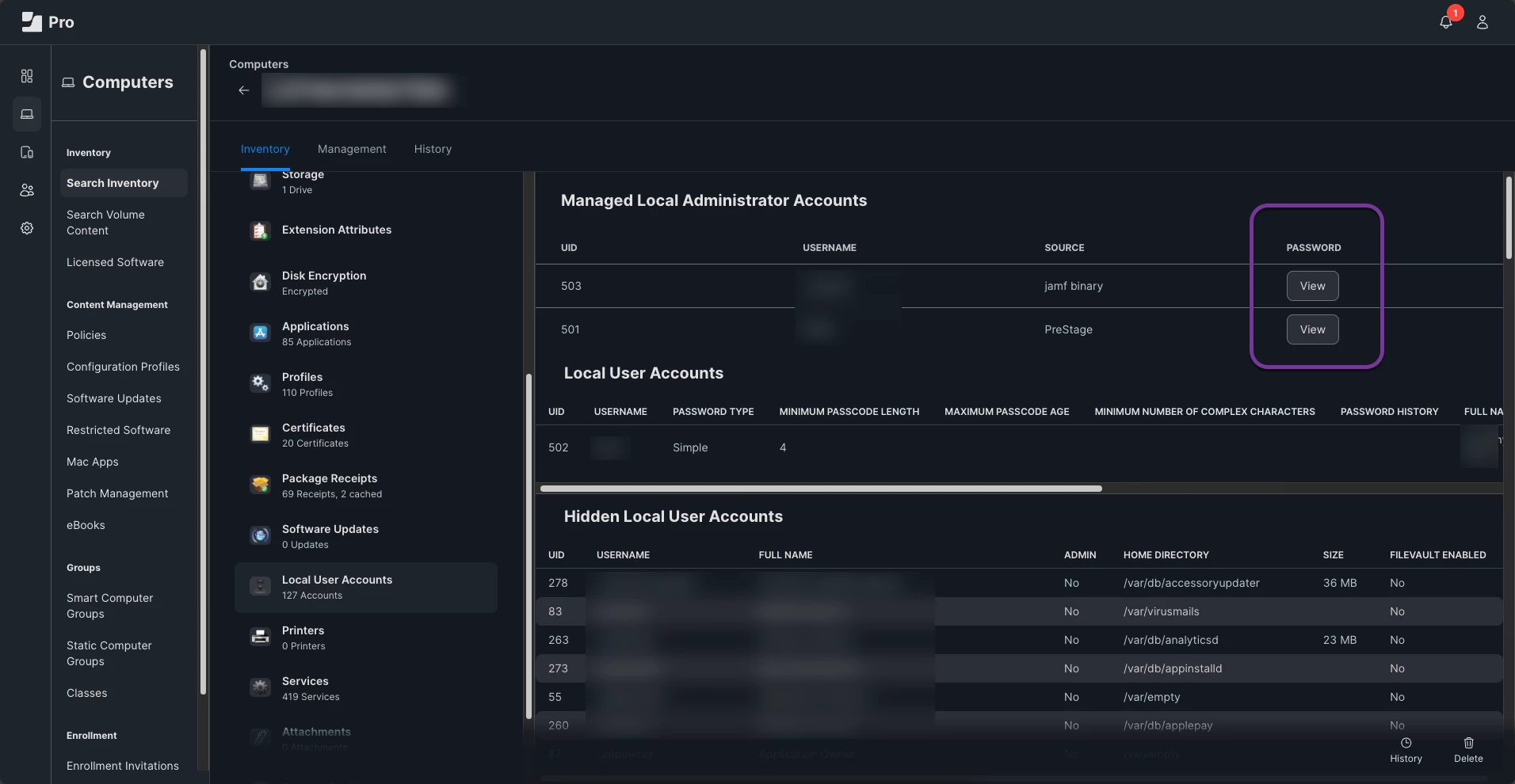
4. We are finding that Admin1 has Secure Token instead. We don't know how this is, since accounts created before setupassistant shouldn't get Secure Token. But we''ll pass that by, as we can live with it.
5. Admin1 password wobbles, will not logon to desktop. Also cannot ssh to it or su to it.
6. Adminbak logs on but does not have Secure Token. Admin1 is the only account with Secure Token, even though it is created by prestage. Hence nobody else can get Secure Token.
7. Although Admin1 exists, there is no home directory.
8. We cannot change the password of Admin1 from Adminbak. We get an error message "One of the parameters provided was incorrect".
9. We cannot delete Admin1, probably because it has Secure Token and no other account does. Attempting to remove it through Jamf Record does not work either.
10. If we run "dscl . -authonly Admin1 [known password]" to validate the password we do not get the error "eDSAuthFailed" as we would expect if the password was wrong. Instead we get "eDSAuthMethodNotSupported".
11. Today we attempted to run "resetpassword" from Recovery Console and change all passwords. This failed with the error "Could not verify credentials because directory server does not support this authentication method", and also left us in the state where the Mac failed Activation. The only solution was to refresh with AppleConfigurator2
The last two symptoms have caused us to conclude that although Admin1 should be a local account, macOS is treating it as a mobile account, and trying to logon to ADS, where there is no account called "Admin1". Hence why we cannot change the password through "resetpassword".
Is this familiar to anyone else? We don't know if it's a macOS or Jamf issue. We are certain that when it has occurred there is no way out of it other than wipe and re-enroll, but it would be good to find the cause and therefore prevent it in the first place.
Cheers
DaveB
Question
Administrator account scrambled into Network account?
 +3
+3Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.