I feel like I'm playing whack-a-mole with these but our students with macbook airs are finding ways to get around everything I have in place and still managing to install VPNs
Students have a standard account
I have a profile in place to prevent adding chrome extensions
I have the App Store set to updates only
Student devices have Securly at home filtering set up
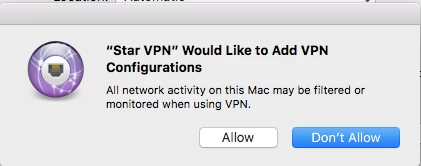
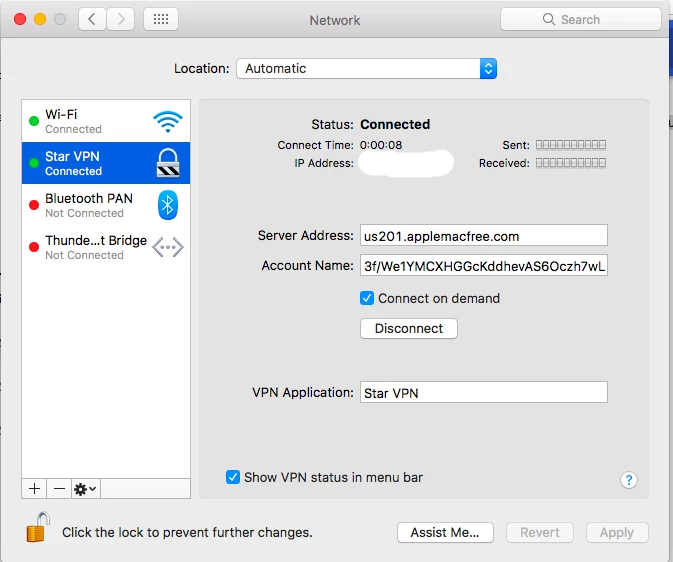
The latest VPN they have is StarVPN it doesn't show up as running, the only way to see it (so far that i've noticed) is it adds a network service, which they shouldn't even be able to do without admin permissions.
any suggestions on preventing this further? We are being forced to hold off on device collection until the last day of school and are worried that VPNs will prevent us from locking computers that aren't returned.