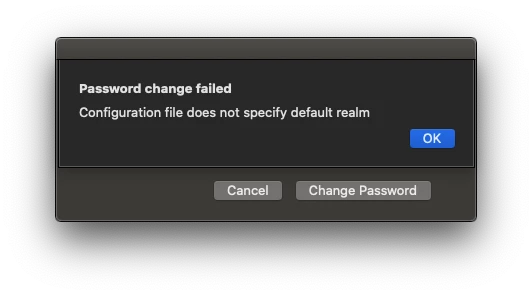
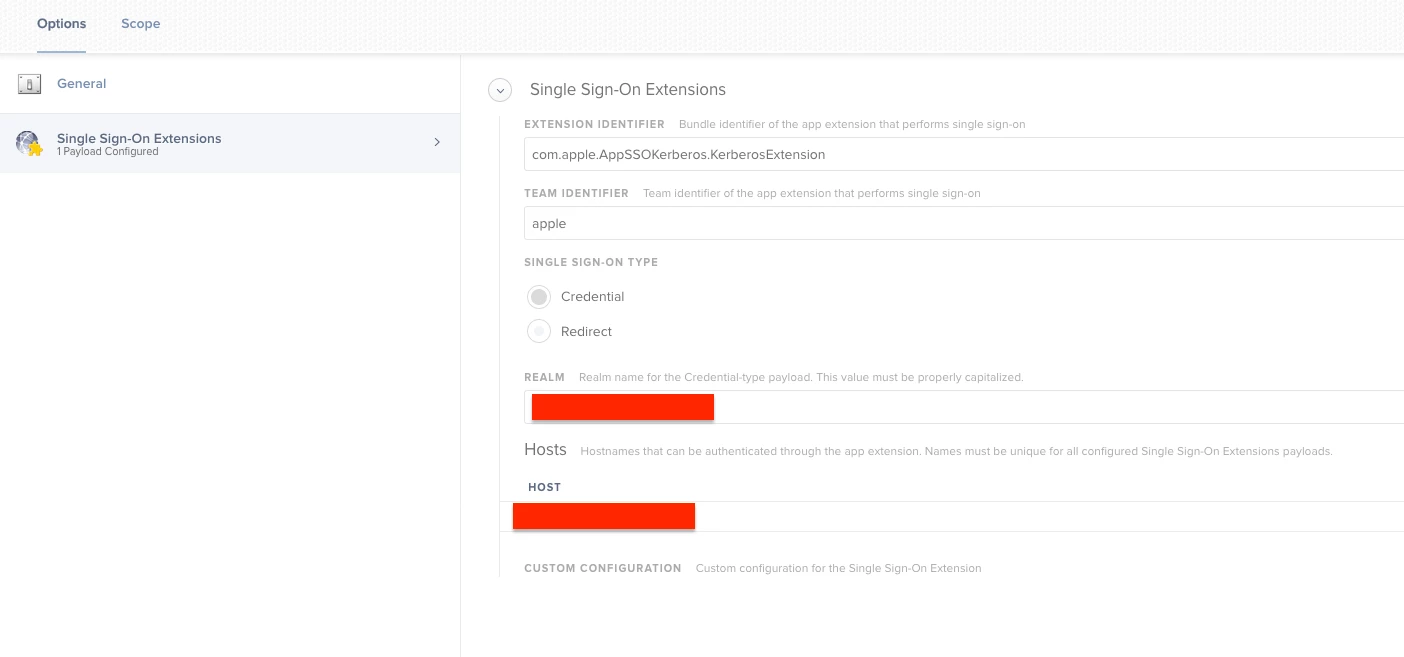
Has anyone setup Single Sign on with Catalina OS? I heard about it in during their last event. I am up to date with the Catalina Beta but cannot find anything to set it up. https://developer.apple.com/videos/play/wwdc2019/303/ towards the end of this video is where it is mentioned. We want to have the Mac users login to their computers the same way our PC (All PCs are joined to Azure) users do by using their email address and password. Any recommendations?
Question
Catalina Single Sign On
 +4
+4Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.