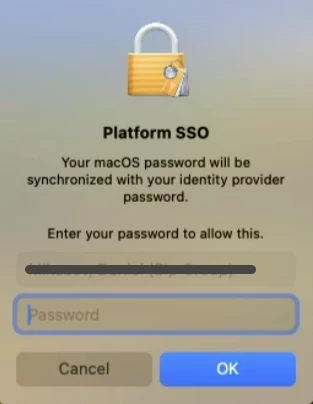
Microsoft has released Company Portal 5.2401.2 with support for Platform SSO.
Users with SSO profiles receive a pop-up requesting registration with Azure Account to synchronize the local Mac password.
Has anyone had this experience?
Microsoft has released Company Portal 5.2401.2 with support for Platform SSO.
Users with SSO profiles receive a pop-up requesting registration with Azure Account to synchronize the local Mac password.
Has anyone had this experience?

Best answer by rabbitt
For anyone following this topic, we have some remediation documented at https://www.jamf.com/blog/entra-id-platform-sso-device-compliance/ [link updated 4APR2024]
 +4
+4Yes, I have the same issue. This registration windows show, have not find a way t0 disable the notification either.
Please review your SSOe configuration profile within Jamf Pro and disable the Platform SSO support. That should prevent the pop up for users. May require a system reboot after you deploy the updated profile to your fleet.
Please review your SSOe configuration profile within Jamf Pro and disable the Platform SSO support. That should prevent the pop up for users. May require a system reboot after you deploy the updated profile to your fleet.
Removing SSOe means losing the function of SSO
 +4
+4Please review your SSOe configuration profile within Jamf Pro and disable the Platform SSO support. That should prevent the pop up for users. May require a system reboot after you deploy the updated profile to your fleet.
Not a good solution 🤣
 +10
+10This Company Portal v5.2401.2 update 100% breaks existing Intune registrations when users click the prompt and provide their password in the SSO plug-in. It has broken many of our Macs with the only fix being to have users manually re-register via Self Service. We have a Sev A case open with MS since yesterday afternoon with very slow response as usual since MS has very few engineers that understand this configuration.
This Company Portal v5.2401.2 update 100% breaks existing Intune registrations when users click the prompt and provide their password in the SSO plug-in. It has broken many of our Macs with the only fix being to have users manually re-register via Self Service. We have a Sev A case open with MS since yesterday afternoon with very slow response as usual since MS has very few engineers that understand this configuration.
Same for me on several instances of Jamf.
The main problem seems to be related to creating a new computer id under Entra ID, which is not compliant until Intune synchronization which is not so fast.
Does anyone know of a workaround?
Is there an SSOe configuration that does not invoke this new registration while keeping the SSO enabled?
 +10
+10Please review your SSOe configuration profile within Jamf Pro and disable the Platform SSO support. That should prevent the pop up for users. May require a system reboot after you deploy the updated profile to your fleet.
I disabled the Platform SSO setting in our Microsoft Enterprise SSO profile and this seems to have fixed the issue. When you read what the setting does, it is only related to the sign-in window.
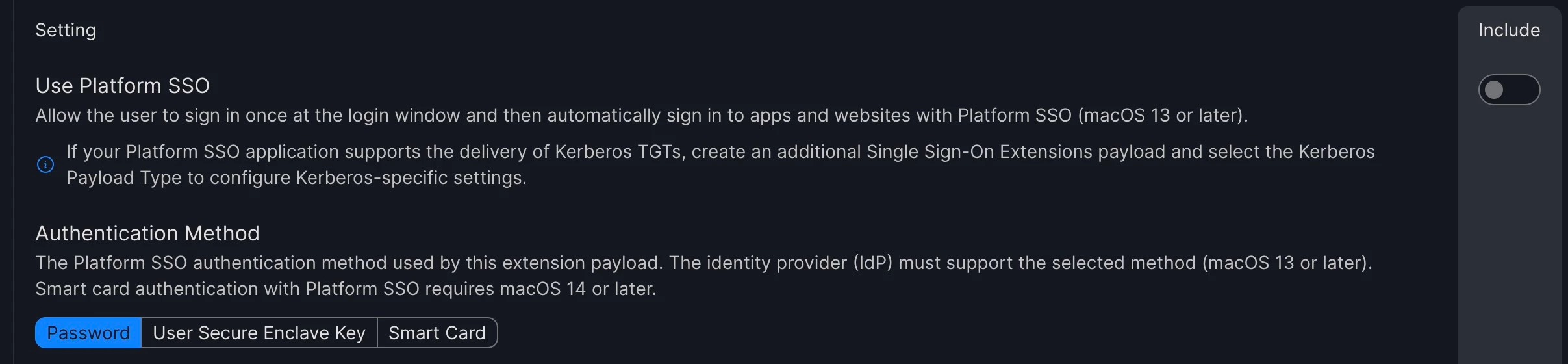
We actually can't support Platform SSO at the sign-in window, so not sure why this was even enabled. To be honest, after testing on my own Mac SSO seems a little better system wide with this setting disabled. Doing further testing now with a new enrollment and older version of CP, then will allow CP to update to see if the issues reappears.
 +4
+4I disabled the Platform SSO setting in our Microsoft Enterprise SSO profile and this seems to have fixed the issue. When you read what the setting does, it is only related to the sign-in window.

We actually can't support Platform SSO at the sign-in window, so not sure why this was even enabled. To be honest, after testing on my own Mac SSO seems a little better system wide with this setting disabled. Doing further testing now with a new enrollment and older version of CP, then will allow CP to update to see if the issues reappears.
And SSO for 365 etc still works?
 +10
+10And SSO for 365 etc still works?
Yes, after restart. Actually seems to work better and more seamless than before when the PSSO setting was enabled.
 +4
+4Yep, getting this too, fortunately we haven't gone live with our conditional access policy yet or this could have been a major issue. If you hear back from microsoft please update us.
We have some devices which still seem compliant after the inputting of information so I'm not sure whether they become compliant again or whether it is hit and miss.
 +4
+4Yep, getting this too, fortunately we haven't gone live with our conditional access policy yet or this could have been a major issue. If you hear back from microsoft please update us.
We have some devices which still seem compliant after the inputting of information so I'm not sure whether they become compliant again or whether it is hit and miss.
When we disabled platform SSO it totally broke the Entra compliance registration and we had to re-register to get it to work again.
 +1
+1We also have been hit by this issue. We have updated our SSO Config Profile to toggle "Platform SSO" off, and redistributed to all of our Macs. However, we are still having some users getting Platform SSO login prompts after reboot. Has anyone found a solution to the login prompts?
The behavior is not the best.
If you have Company Portal 5.24 and PSSO enabled, the macOS starts the registration notification.
If the user does not register, removing the PSSO stops the notification. So far, it is consistent:
PSSO ON = notification enabled
PSSO OFF = notification disabled
Problems start when the user completes registration:
1st problem: a new device is registered in Entra ID with a different ID and compliant is N/A - then fails Conditional Access.
2nd problem: "password change" is disabled on macOS, so it is necessary to change the password from Entra ID. Here I need further testing, but in the first facts the local user password is not changed and I fear for FileVault.
All these settings seem to introduce interesting new features, but there is a lack of documentation and tests and we are going by trial and error at this time.
Updating the documentation is very urgent
 +10
+10Microsoft really screwed alot of us with this and has been zero help so far. But that isn't a surprise. Anyway....
Here is what we have found. Anyone that incorrectly clicked to do the PSSO is probably never going to get fully straightened out just by redoing the Intune Integration registration from Self Service. If a user didn't click it and you disabled the “use Platform SSO” setting in your profile then they are probably good to go. Anyone that had already accidentally enabled it, it will stay enable no matter what the profile says. Reboots don't help.
What I found is that anyone who clicked and technically enabled PSSO there is appears that there is no way to get rid of it....but there is.
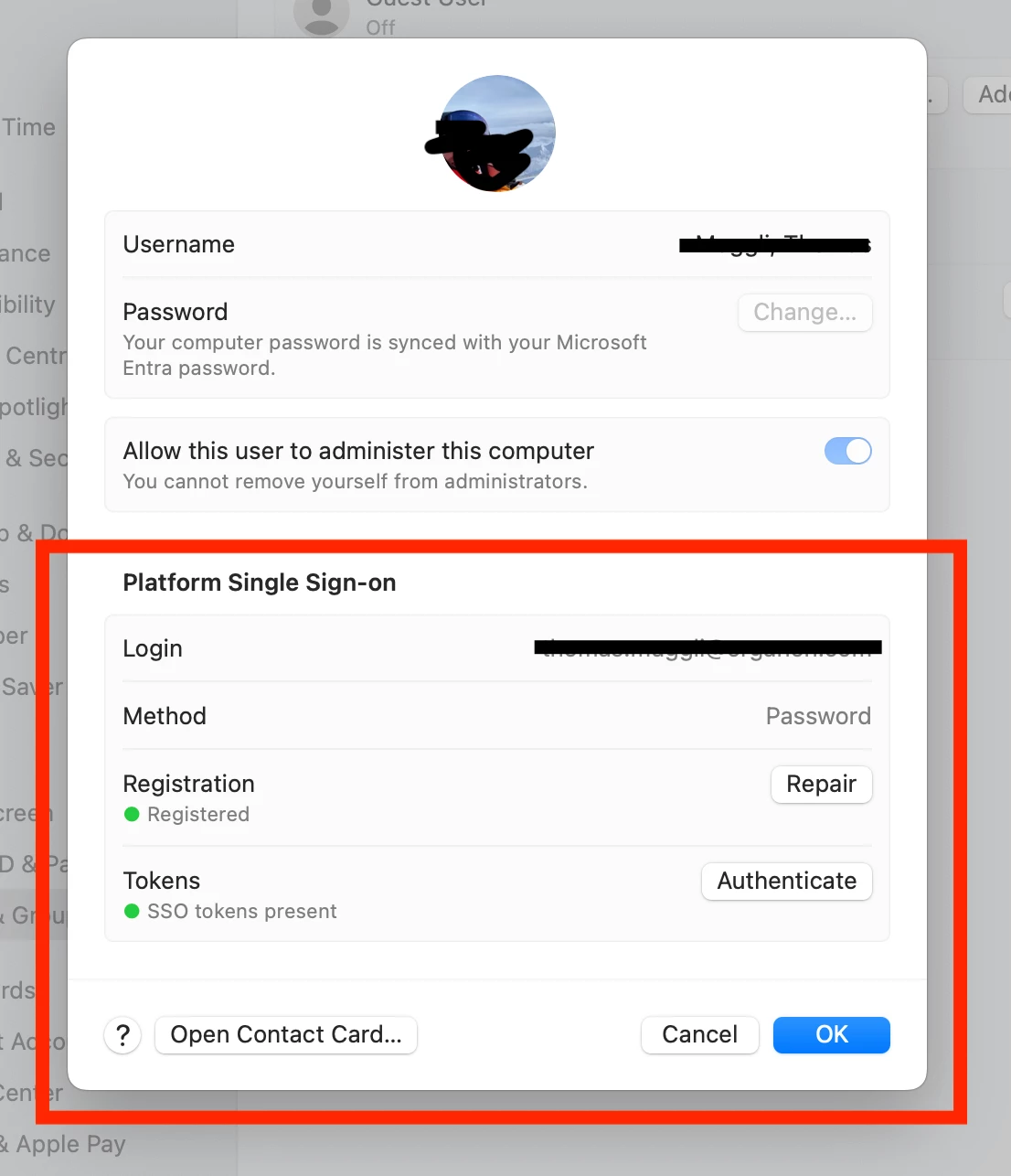
If you look at the user's System Settings>Users & Groups> {user's account} and click the i....
This is bad, it means the PSSO is enabled and Enterprise SSO is going to continue to have issues. If they show the Platform single Sign On section in their account then it is already enabled and messing with SSO.
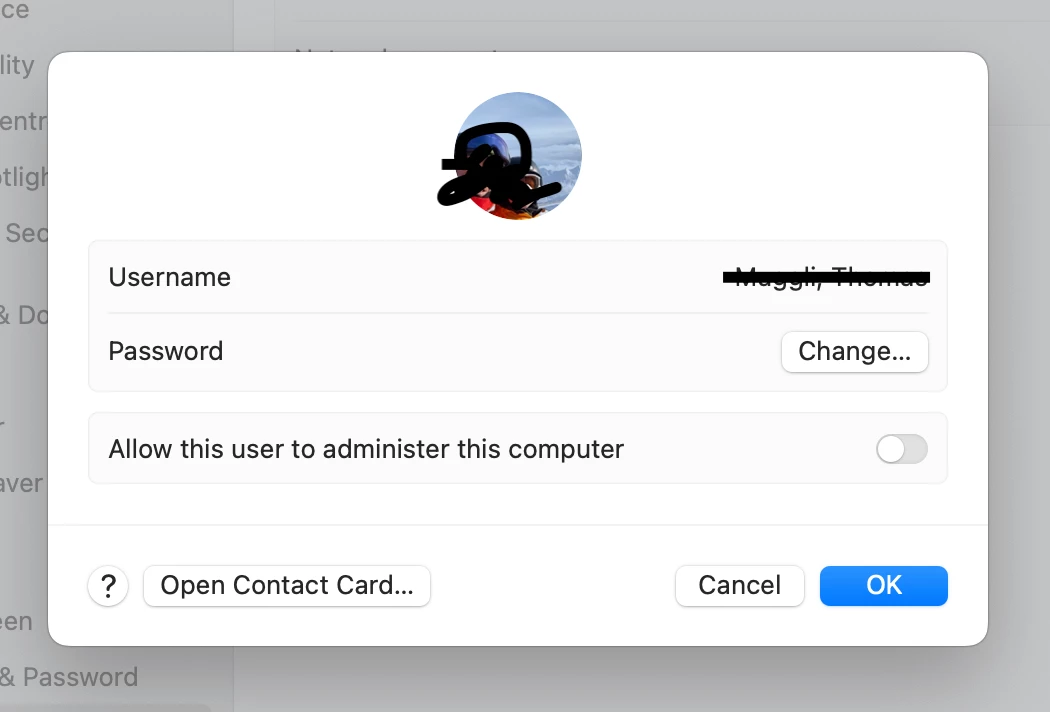
This is good, it means that the user didn't click and didn't enable PSSO. These users probably aren't having issues or just need to register again from Self Service.
The only way I have found to get rid of the "bad" is to exclude the user's computer or some smart group from the SSO profile so it is removed from their Mac. This will disable the SSO extension and get rid of the PSSO. Wait a few minutes, then remove the exclusion so the SSO profile is installed on their Mac again which will reenable the SSO extension including not enabling PSSO since you probably/hopefully already disabled the setting. After getting the profile back on the Mac, confirm the PSSO section is removed from their account info. After this the user should be able to register again via the Self Service policy, wait a few minutes for Entra/Intune to catch up, then they should be able to sign in again, use SSO and all of their problems should be solved. No restart was need in my experience.
Hope this makes sense and helps those pulling their hair out with the mess.
 +10
+10Microsoft really screwed alot of us with this and has been zero help so far. But that isn't a surprise. Anyway....
Here is what we have found. Anyone that incorrectly clicked to do the PSSO is probably never going to get fully straightened out just by redoing the Intune Integration registration from Self Service. If a user didn't click it and you disabled the “use Platform SSO” setting in your profile then they are probably good to go. Anyone that had already accidentally enabled it, it will stay enable no matter what the profile says. Reboots don't help.
What I found is that anyone who clicked and technically enabled PSSO there is appears that there is no way to get rid of it....but there is.
If you look at the user's System Settings>Users & Groups> {user's account} and click the i....
This is bad, it means the PSSO is enabled and Enterprise SSO is going to continue to have issues. If they show the Platform single Sign On section in their account then it is already enabled and messing with SSO.

This is good, it means that the user didn't click and didn't enable PSSO. These users probably aren't having issues or just need to register again from Self Service.

The only way I have found to get rid of the "bad" is to exclude the user's computer or some smart group from the SSO profile so it is removed from their Mac. This will disable the SSO extension and get rid of the PSSO. Wait a few minutes, then remove the exclusion so the SSO profile is installed on their Mac again which will reenable the SSO extension including not enabling PSSO since you probably/hopefully already disabled the setting. After getting the profile back on the Mac, confirm the PSSO section is removed from their account info. After this the user should be able to register again via the Self Service policy, wait a few minutes for Entra/Intune to catch up, then they should be able to sign in again, use SSO and all of their problems should be solved. No restart was need in my experience.
Hope this makes sense and helps those pulling their hair out with the mess.
Oh yeah, and any records in Entra that show as "Microsoft Entra joined" are the bad records created by PSSO. If the record shows as "Microsoft Entra registered" then this should be a good record created when the registration was done via the Self Service policy. I decided I wasn't going to delete any of the bad records in Entra to avoid any possible issues. I will just let them go stale or purge them down the road when the dust settles.
 +1
+1Microsoft really screwed alot of us with this and has been zero help so far. But that isn't a surprise. Anyway....
Here is what we have found. Anyone that incorrectly clicked to do the PSSO is probably never going to get fully straightened out just by redoing the Intune Integration registration from Self Service. If a user didn't click it and you disabled the “use Platform SSO” setting in your profile then they are probably good to go. Anyone that had already accidentally enabled it, it will stay enable no matter what the profile says. Reboots don't help.
What I found is that anyone who clicked and technically enabled PSSO there is appears that there is no way to get rid of it....but there is.
If you look at the user's System Settings>Users & Groups> {user's account} and click the i....
This is bad, it means the PSSO is enabled and Enterprise SSO is going to continue to have issues. If they show the Platform single Sign On section in their account then it is already enabled and messing with SSO.

This is good, it means that the user didn't click and didn't enable PSSO. These users probably aren't having issues or just need to register again from Self Service.

The only way I have found to get rid of the "bad" is to exclude the user's computer or some smart group from the SSO profile so it is removed from their Mac. This will disable the SSO extension and get rid of the PSSO. Wait a few minutes, then remove the exclusion so the SSO profile is installed on their Mac again which will reenable the SSO extension including not enabling PSSO since you probably/hopefully already disabled the setting. After getting the profile back on the Mac, confirm the PSSO section is removed from their account info. After this the user should be able to register again via the Self Service policy, wait a few minutes for Entra/Intune to catch up, then they should be able to sign in again, use SSO and all of their problems should be solved. No restart was need in my experience.
Hope this makes sense and helps those pulling their hair out with the mess.
Great thank you Scottlep,
Do you happen to have Jamf Connect in your environment?
 +10
+10Great thank you Scottlep,
Do you happen to have Jamf Connect in your environment?
We do not. We just use the Enterprise SSO (formerly Enterprise Connect) for password management with unbound Macs running Zscaler. No issues as long as the devices are correctly registered (and MS doesn't break it 😀).
 +1
+1I want to check if the downgrade is a temporary fix but cannot find any PKG for Company Portal 5.2401.0 anyone have it?
 +10
+10I want to check if the downgrade is a temporary fix but cannot find any PKG for Company Portal 5.2401.0 anyone have it?
I can confirm that a downgrade is not a temporary fix for those that have already experienced the issues, had users click to register PSSO, etc.
 +1
+1I can confirm that a downgrade is not a temporary fix for those that have already experienced the issues, had users click to register PSSO, etc.
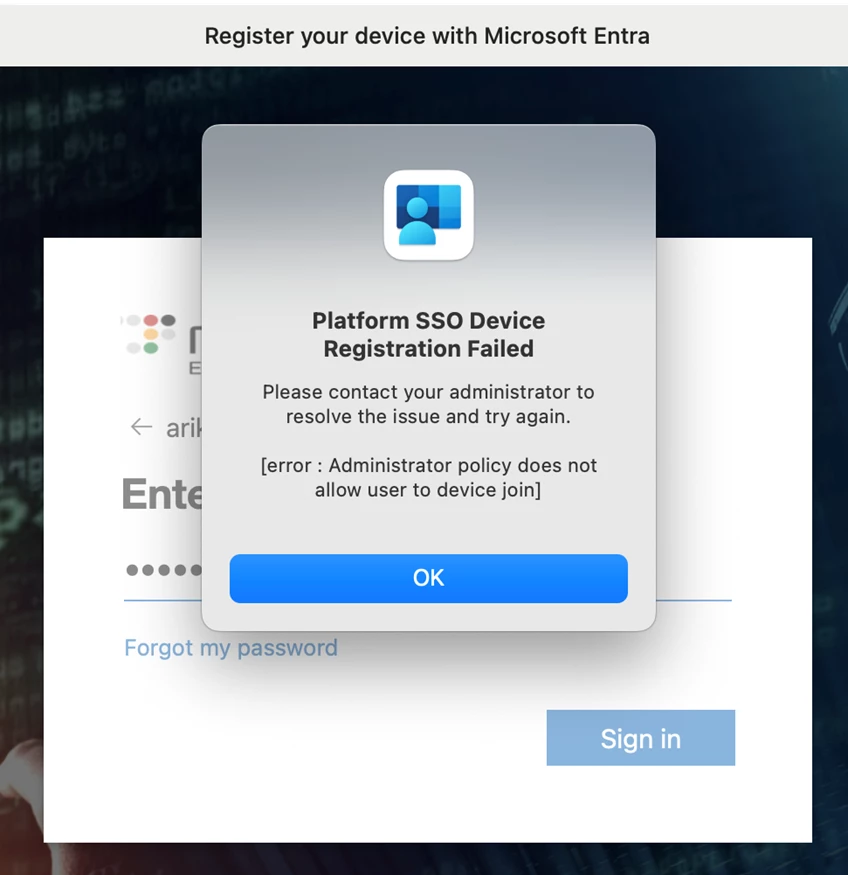
We have a different issue but very similar, we got the error attached after the 5.2401.2 update.
Think that a downgrade will work for me, but I can't find any PKG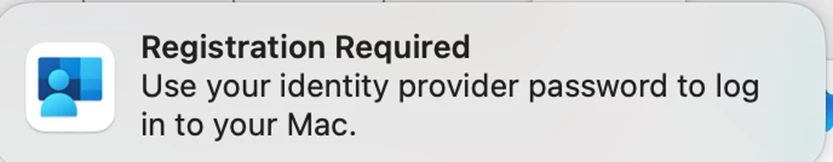
 G files.
G files.
 +2
+2Microsoft really screwed alot of us with this and has been zero help so far. But that isn't a surprise. Anyway....
Here is what we have found. Anyone that incorrectly clicked to do the PSSO is probably never going to get fully straightened out just by redoing the Intune Integration registration from Self Service. If a user didn't click it and you disabled the “use Platform SSO” setting in your profile then they are probably good to go. Anyone that had already accidentally enabled it, it will stay enable no matter what the profile says. Reboots don't help.
What I found is that anyone who clicked and technically enabled PSSO there is appears that there is no way to get rid of it....but there is.
If you look at the user's System Settings>Users & Groups> {user's account} and click the i....
This is bad, it means the PSSO is enabled and Enterprise SSO is going to continue to have issues. If they show the Platform single Sign On section in their account then it is already enabled and messing with SSO.

This is good, it means that the user didn't click and didn't enable PSSO. These users probably aren't having issues or just need to register again from Self Service.

The only way I have found to get rid of the "bad" is to exclude the user's computer or some smart group from the SSO profile so it is removed from their Mac. This will disable the SSO extension and get rid of the PSSO. Wait a few minutes, then remove the exclusion so the SSO profile is installed on their Mac again which will reenable the SSO extension including not enabling PSSO since you probably/hopefully already disabled the setting. After getting the profile back on the Mac, confirm the PSSO section is removed from their account info. After this the user should be able to register again via the Self Service policy, wait a few minutes for Entra/Intune to catch up, then they should be able to sign in again, use SSO and all of their problems should be solved. No restart was need in my experience.
Hope this makes sense and helps those pulling their hair out with the mess.
Instead of excluding it I updated the config profile to disable Use Platform SSO, that removed the settings on those Mac that had registered using the pop-up.
but I do hear compliant about Microsoft apps not working for those who registered.
Microsoft really screwed alot of us with this and has been zero help so far. But that isn't a surprise. Anyway....
Here is what we have found. Anyone that incorrectly clicked to do the PSSO is probably never going to get fully straightened out just by redoing the Intune Integration registration from Self Service. If a user didn't click it and you disabled the “use Platform SSO” setting in your profile then they are probably good to go. Anyone that had already accidentally enabled it, it will stay enable no matter what the profile says. Reboots don't help.
What I found is that anyone who clicked and technically enabled PSSO there is appears that there is no way to get rid of it....but there is.
If you look at the user's System Settings>Users & Groups> {user's account} and click the i....
This is bad, it means the PSSO is enabled and Enterprise SSO is going to continue to have issues. If they show the Platform single Sign On section in their account then it is already enabled and messing with SSO.

This is good, it means that the user didn't click and didn't enable PSSO. These users probably aren't having issues or just need to register again from Self Service.

The only way I have found to get rid of the "bad" is to exclude the user's computer or some smart group from the SSO profile so it is removed from their Mac. This will disable the SSO extension and get rid of the PSSO. Wait a few minutes, then remove the exclusion so the SSO profile is installed on their Mac again which will reenable the SSO extension including not enabling PSSO since you probably/hopefully already disabled the setting. After getting the profile back on the Mac, confirm the PSSO section is removed from their account info. After this the user should be able to register again via the Self Service policy, wait a few minutes for Entra/Intune to catch up, then they should be able to sign in again, use SSO and all of their problems should be solved. No restart was need in my experience.
Hope this makes sense and helps those pulling their hair out with the mess.
I can confirm the behavior.
The only way to disable PSSO is to remove the SSOe profile completely. Disabling PSSO in the SSOe profile is not enough.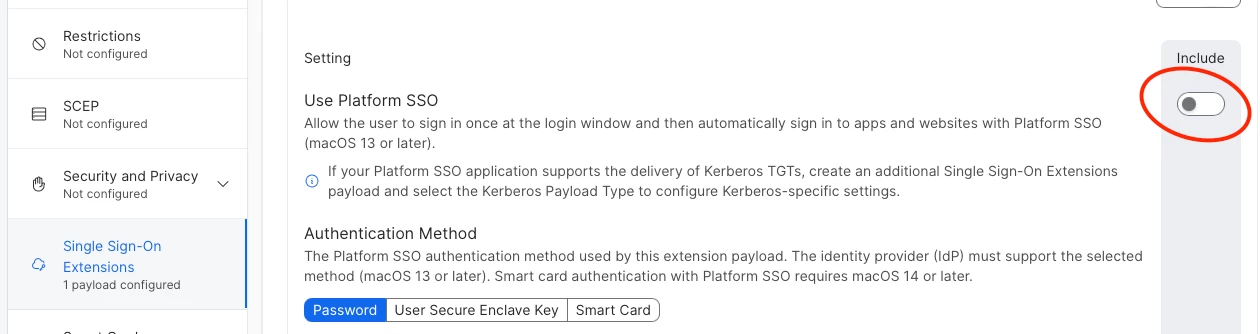
Once removed, you can deploy SSOe without PSSO
 +1
+1Good morning.
Has anyone managed to remove the notification?
Good morning.
Has anyone managed to remove the notification?
To remove the notification, it is necessary to remove the SSOe profile completely, then deploy it again without PSSO.
it is not sufficient to remove only PSSO
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.
Sorry, we're still checking this file's contents to make sure it's safe to download. Please try again in a few minutes.
OKSorry, our virus scanner detected that this file isn't safe to download.
OK