I am having a little brain fart here, but I'm sure it's simple. When I run this jamf policy using the event flag from Terminal, it runs just fine (probably because it prompts for my credentials). But if I try to run it from self service, I get an error that a Terminal is required for the password.
Script:
#!/bin/bash
#Find current logged in user
loggedInUser=$( scutil <<< "show State:/Users/ConsoleUser" | awk '/Name :/ && ! /loginwindow/ { print $3 }' )
#Runs SysDiagnose as Current User
su $loggedInUser -c "sudo /usr/bin/sysdiagnose -u -f ~/Desktop/"
Error:
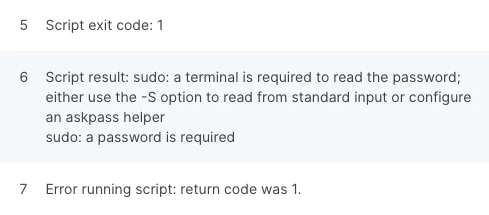
I want users to have the capability to run SysDiagnose from Self Service, without it prompting for a password.


