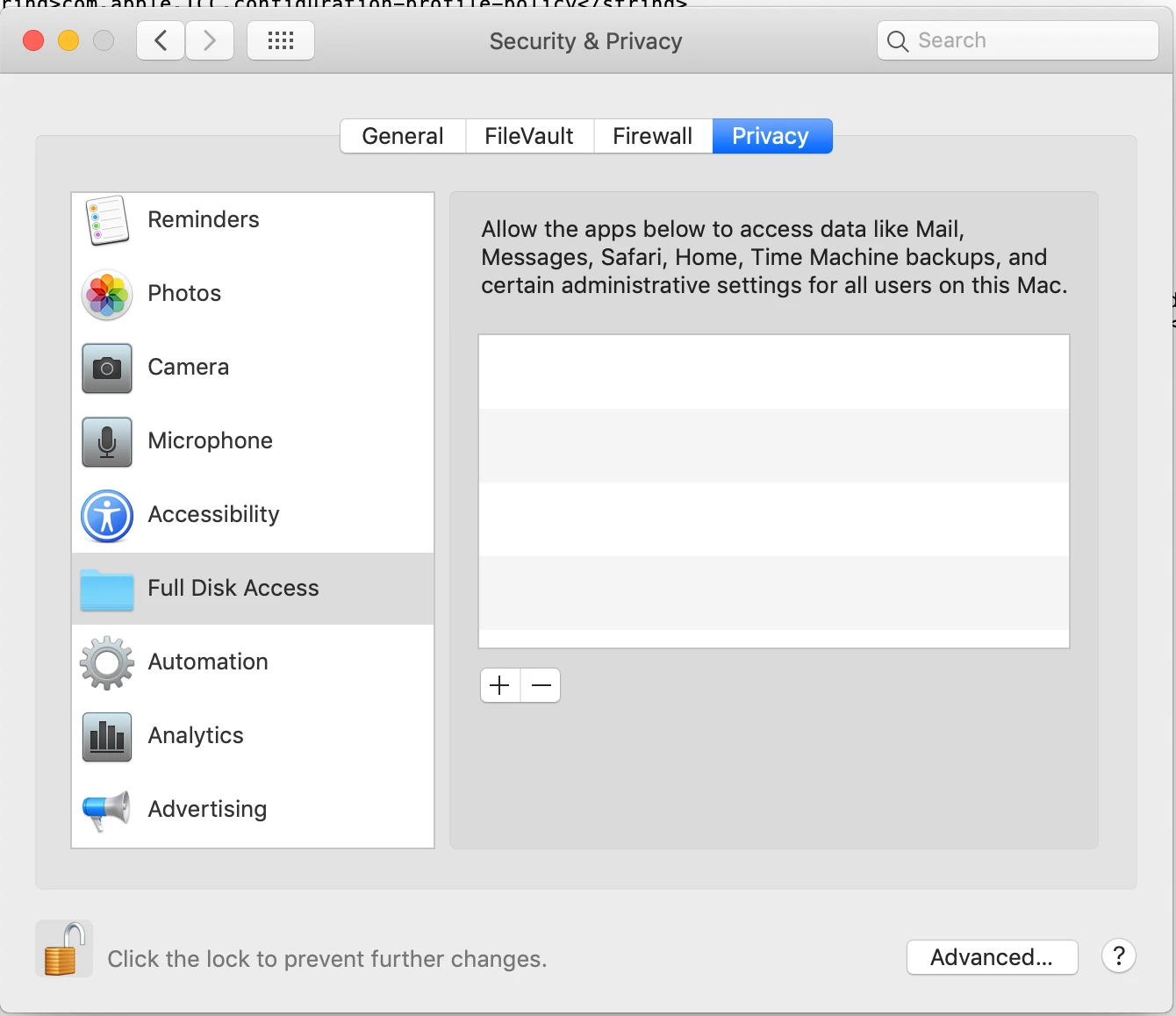
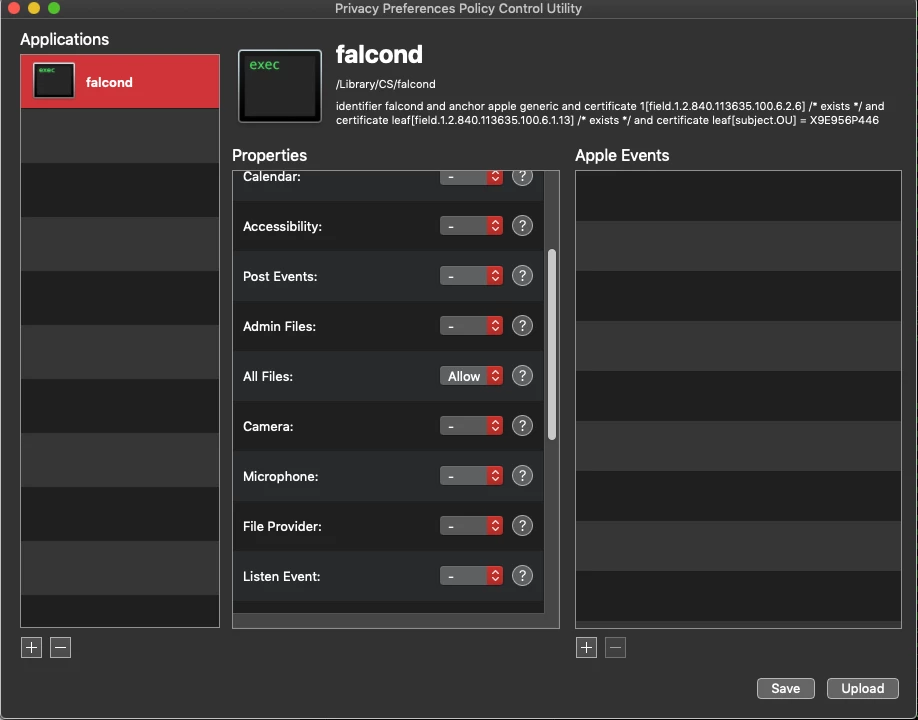
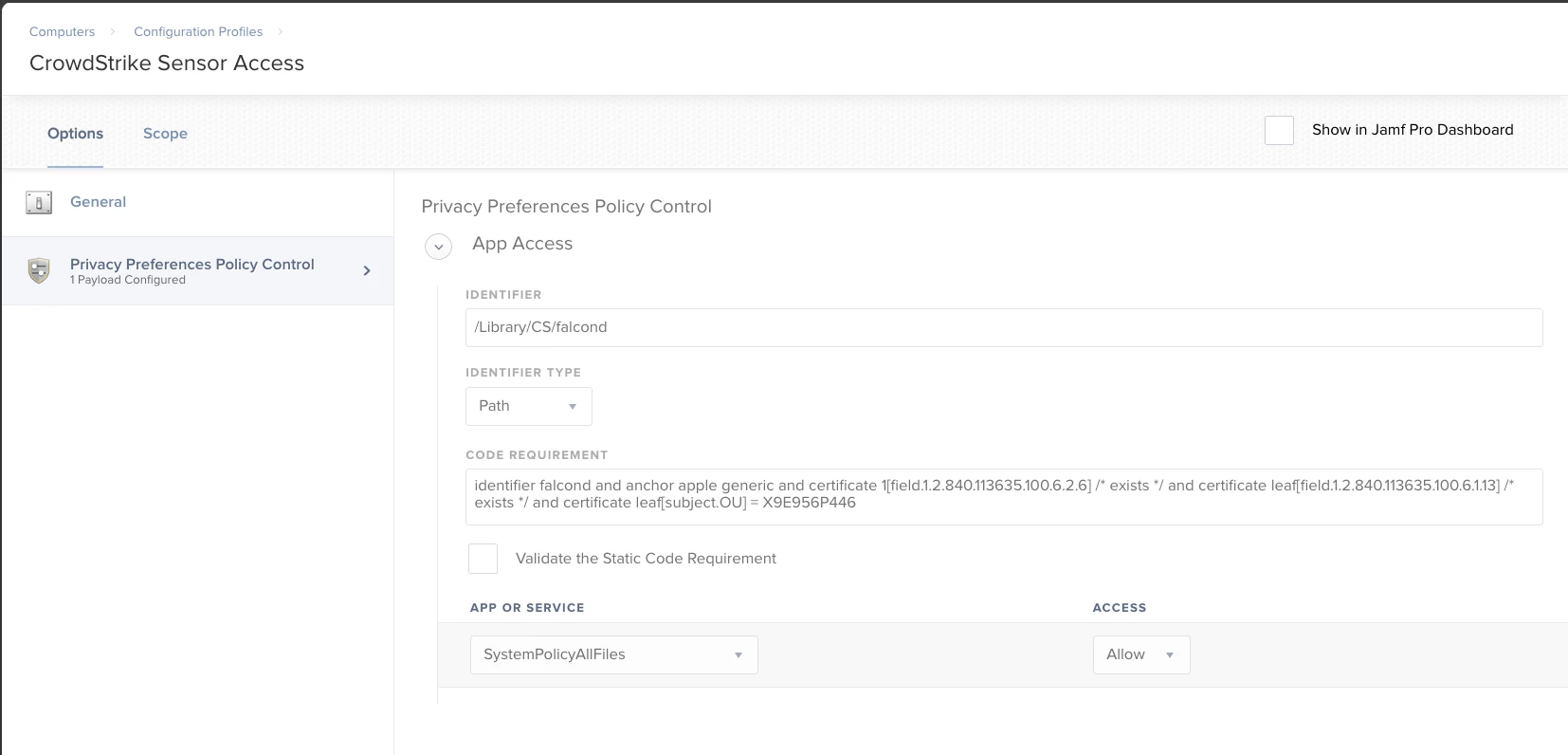
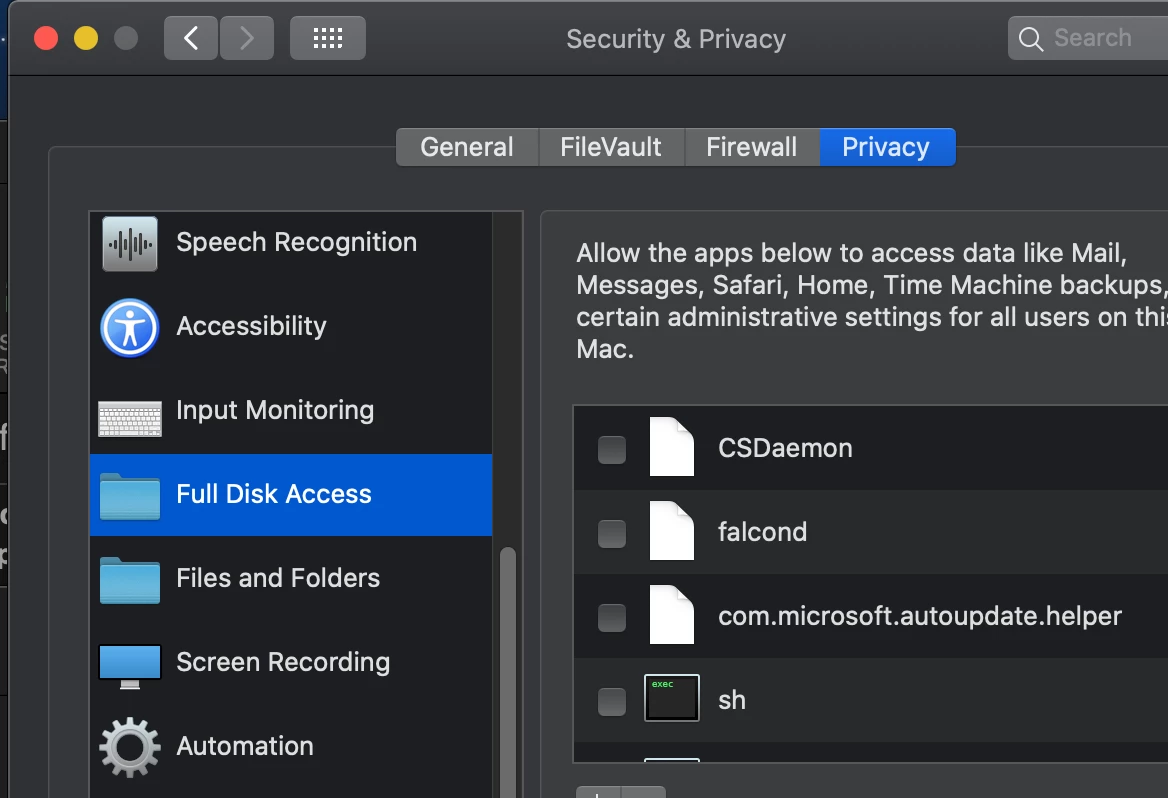
Anyone have to create a TCC.xml for crowdstrike yet? Looking for some assistance as I am having some troubles getting the proper informaiton needed to build it out.
Question
Crowdstrike TCC.xml for PPPC
 +2
+2Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.