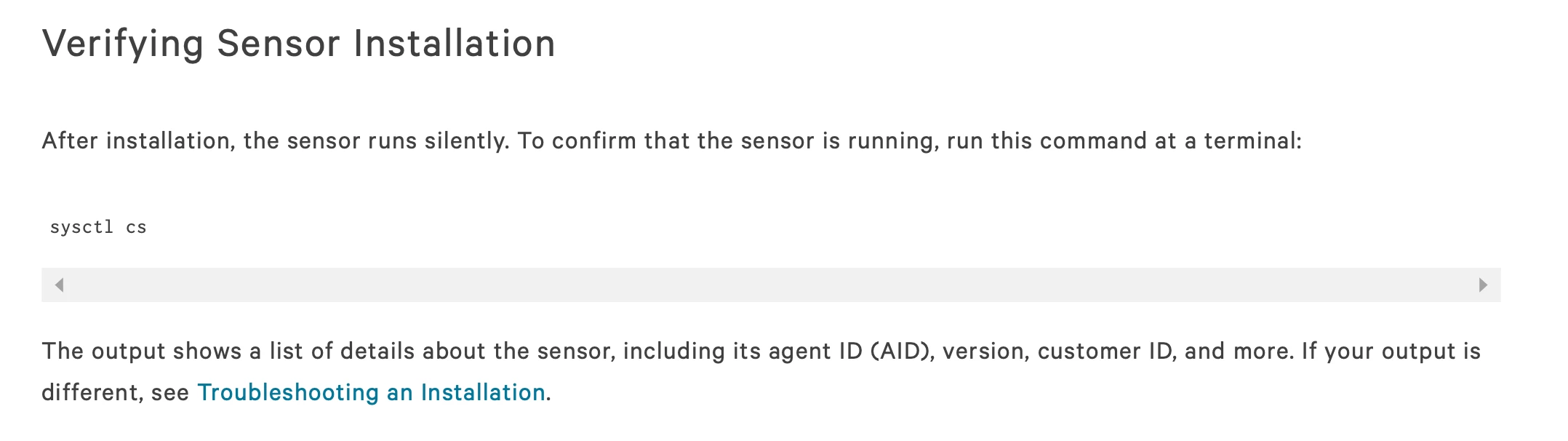
Hi is there anyone on here that has created a smart group for Macs that have CrowdStrike Endpoint protection installed? It doesnt install as a app so having trouble. Goal is to make a smart group to see which machines actually have it installed, since on my policy it says completed but in logs failed for some reason
Question
CrowdStrike Veryifing install via Jamf
 +3
+3Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.