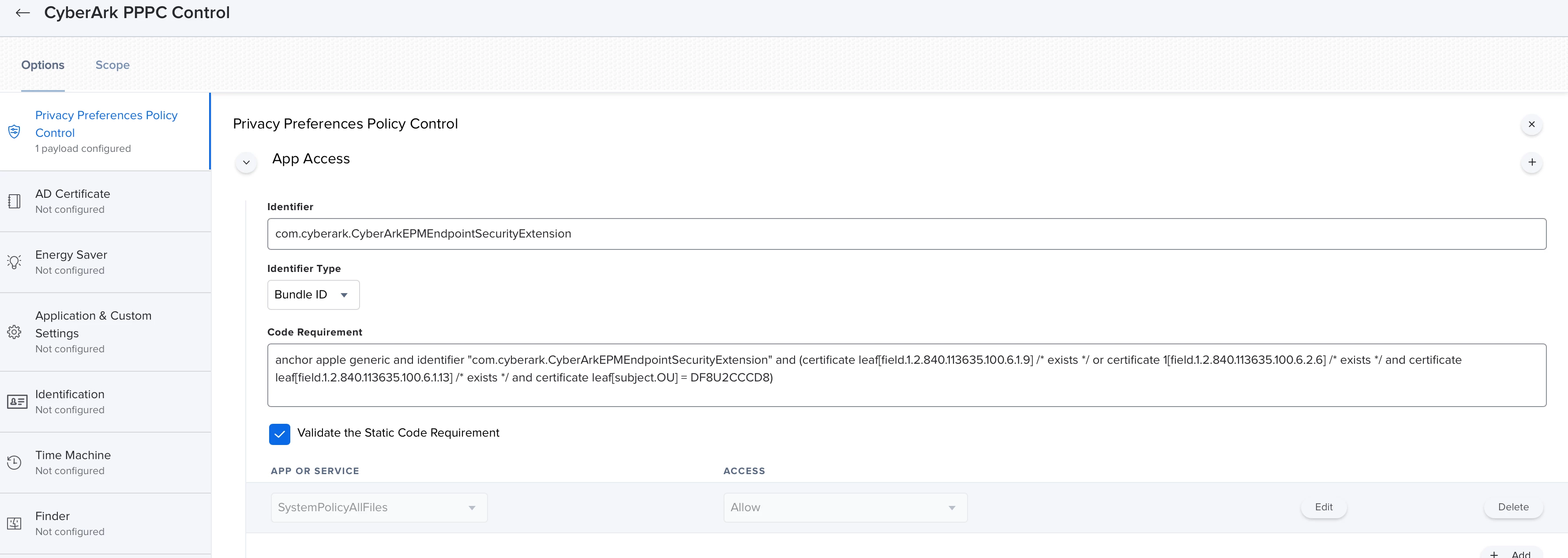
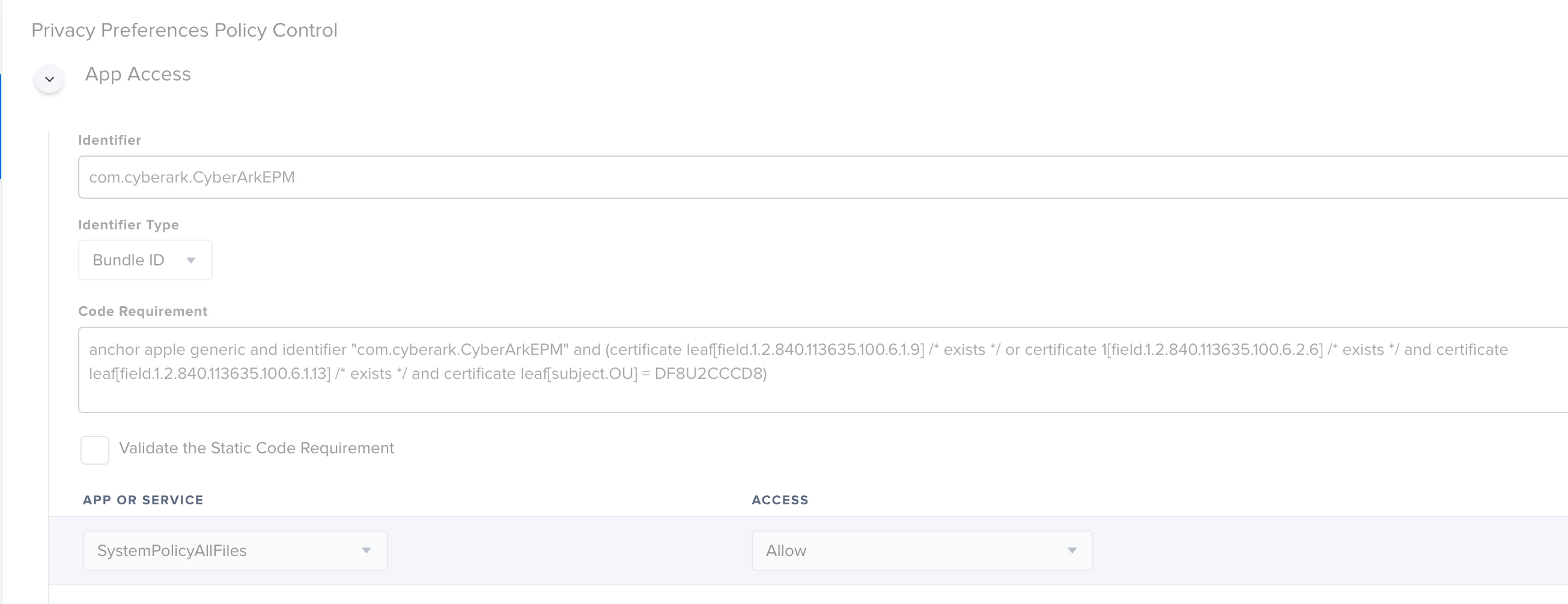
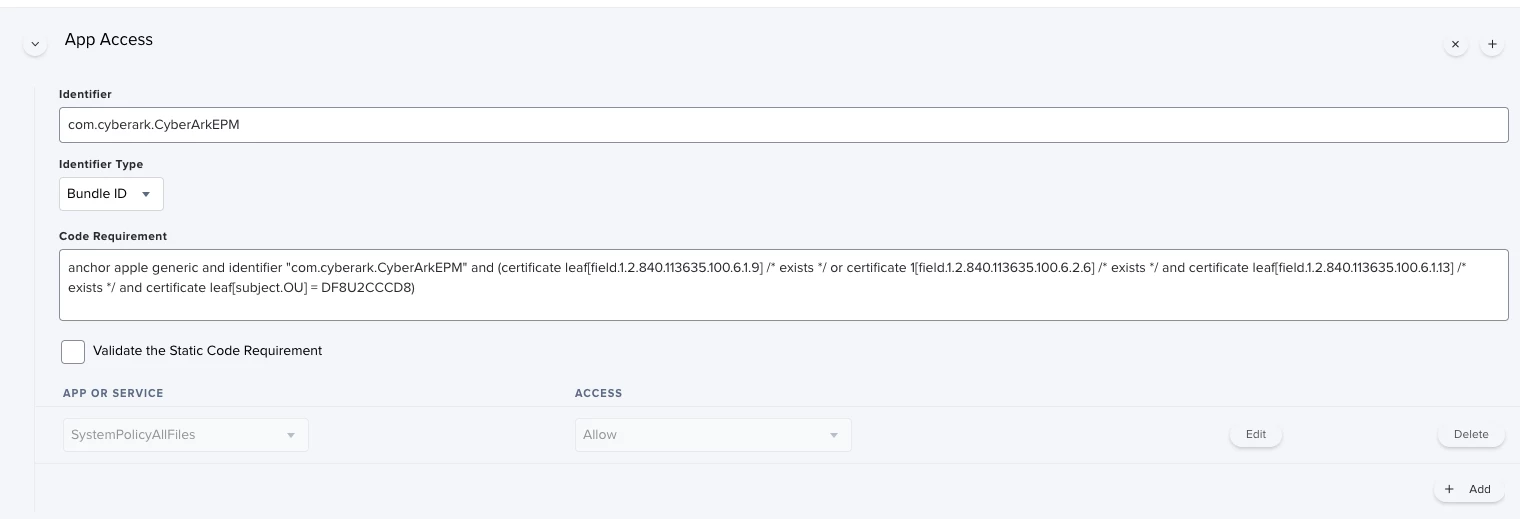
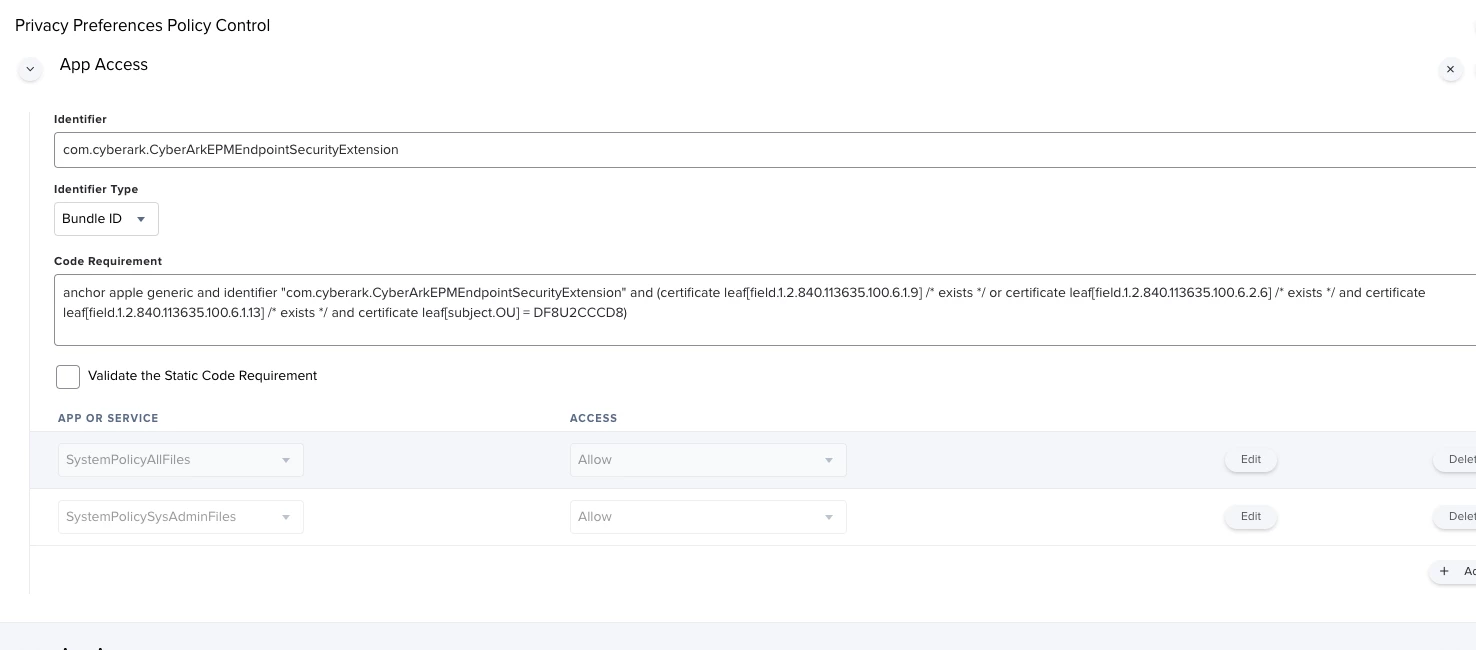
Hey there - does anyone else use CyberArk EPM (end point management) to manage admin rights and third party app installations more easily? We're beginning to roll out a test bed in my company, and I'm working on the mac deployment.
CyberArk provides some instructions for deploying here, but I'm struggling with them. It seems to want the zip file deployed as the package, and there is no pkg, but I've never used a zip file as an installer through Jamf. Anyone got this deployed? Or have any insight on using zip files to deploy apps?