Anyone out there deploying Crashplan 6.5 via Jamf? This used to be a simple process. Deploy a custom folder along with the installer via self service while logged in as the end user. Code42 decided to remove the custom folder replacing it with a deployment file that gets created in the admin console. If you ask me it's a huge pain to have to rework my install workflow. If anyone out there has ideas or experience with this I would love to hear about it. Hmmm, I wonder if Jamf has a support article on this......that's how I setup my installs in the first place.
- Home
- Community
- Get Support
- General Discussions
- Deploy Crashplan 6.5
Deploy Crashplan 6.5
- October 26, 2017
- 24 replies
- 129 views
24 replies
 +5
+5- Contributor
- October 26, 2017
It's quite simple. You deploy a package with the deploy.properties to /tmp/mountpt/Code42CrashPlan/ and then install the installer simply. That's in short terms the way to go. Code42 support helps you out in case of doubts. We had the same problem to rework our workflow. But this way is easier for us and customizations are all done in admin console. Great
Mike
 +15
+15- Contributor
- October 26, 2017
I'm leaving my 5.4.3 installer in place for now. It works with a 6.5 server and it'll auto-upgrade the client to 6.5 as soon as its installed. But, yeah, the change with 6.5 means major workflow changes.
In some situations I like to prompt for a username. I think my 6.5 workflow will be to run an applescript (or windows vise installer) to prompt for the user to assign the backup account to. then I'll save that to /tmp/code42install.tmp. Then I'll invoke my installer with the token parameter. the server side script will read in the contents of that tmp file to assign the username.
 +7
+7- Contributor
- November 10, 2017
We've been running into an issue where CrashPlan won't auto configure properly since going to 6.5. I've set up a Deployment Policy and distribute the deploy.properties to /mnt/mountpt/Code42CrashPlan where it is picked up by the installer (according to the Code42 install.log).
However it doesn't seem to be able to make use of our custom script to define the username.
With our LDAP setup the users e-mail is used as the username instead of the users shortname.
The custom script currently looks like this:
function main() {
local user=$(last | egrep 'console.*still' | egrep -v 'root|admin|reboot|shutdown|local|_mbsetupuser' | awk '{print $1}' | sort -u | head -n1)
local dsclEmail=$(dscl /Search read "/Users/${user}" mail)
echo "C42_USERNAME=${dsclEmail##*mail: }"
echo "C42_USER_HOME=$(dscl . -read "/users/${user}" NFSHomeDirectory | cut -d ' ' -f 2)"
}
main "$@"Has anyone else run into similar problems?
 +12
+12- Contributor
- November 22, 2017
Hey @emilh,
Did you get this sorted? I haven't seen this particular issue, but 6.5 is still pretty new. We'd love to help out with this if you want to submit a case with Code42 support.
Cheers,
-Daniel F.
Technical Support Engineer
Code42 Software, Inc.
 +7
+7- Contributor
- November 23, 2017
Hi @dferrara,
Yeah, I opened up a case with Code42 last week and got it sorted. Apparently it doesn't work unless you've got CA signed SSL set up properly. Sorted that and now the same custom username detection script works.
Thanks!
 +5
+5- Contributor
- December 3, 2017
So to make sure I get the workflow straight based on @mbracco 's post:
- Package deploy.properties (located in /tmp/mountpt/Code42CrashPlan/ ) in Composer (presuming this is done on a clean computer as directed previously)
- Create a new policy that installs deploy.properties before the CrashPlan 6.5 installer.
- Have users run the policy.
Thanks!
 +18
+18- Honored Contributor
- December 4, 2017
Because I didn't like that location for deploy.properties i used the /Library/Application Support/CrashPlan that being said through casper you're probably installing for everyone. Currently Code42's documentation references using the user directory.. This is incorrect, nor does it mention the global Library folder
While you're installing it, you can definitely look at
/Library/Logs/Crashplan in console, the installer file will show you what its doing and if it's found your deploy file.
 +7
+7- Contributor
- December 8, 2017
@emilh or anyone...
Has anyone run into deploying it and needing to sign in for it to work? I used to have it deferred so I could have new users not sign in and still have their files backup... I feel like I am missing something obvious.
I started using the default script incase I have an issue with SSL...
 +7
+7- Contributor
- January 5, 2018
Hey!
is anyone having trouble with crashplan just spinning on "connecting" with a customized push?
 +7
+7- Contributor
- January 9, 2018
@rderewianko Any more information about ports?
We install the custom package and it spins for ever. If we install vanilla from the server it prompts for username and server and it works fine for existing users.
Im stuck on this and was hoping some one here had a solution before working through with Crashplan support
 +1
+1- New Contributor
- January 11, 2018
@bizzaredm did you ever get this issue resolved? I have ran into the same connecting spin after the custom package install.
 +7
+7- Contributor
- January 11, 2018
@GHC Nope... Opened a support case with CrashPlan today and sent them some logs from a test VM. From what I can see in the logs it isnt pulling the right info, server address 0.0.0.0:4xxx for example. Not sure why as it does find the deployment properties file. Im guessing its a connection issue between the client and server, invalid token or something along those lines thats causing the app to throw in default values that of course dont work. but im truly guessing here..
 +4
+4- New Contributor
- January 18, 2018
can you post back here when you get this resolved? we are having the same issue.
thanks!
 +1
+1- New Contributor
- January 18, 2018
Hey guys for what it's worth I got this working for me using this custom script for our infrastructure.
!/bin/sh
function main() {
user=$(scutil --get ComputerName)@email.com
userdir="/Users"
echo "C42_USERNAME=${user}"
echo "C42_USER_HOME=${userdir}
}
main "$@"
The deploy.properties file is stored in the /Library/Application Support/CrashPlan also as mentioned above.
Now has anyone figured out a script to auto enter the password? dont really want users to know this password
 +7
+7- Contributor
- February 5, 2018
Update:
Working with Crashplan support we found that our spinning connecting issue was due to our SSL/Certificate setup. This was easy enough to tell from the logs the SERVICE log file had the answers in it. Java wasn't able to make a chain of trust.
- Jamf Heroes
- February 7, 2018
I'm in the loop of "Connecting..." and looking at the logs it's trying to connect to https://ourserver:4280, but we don't use https when connecting over 4280. Is this similar to the SSL issue you were seeing?
 +7
+7- Contributor
- March 1, 2018
- Jamf Heroes
- March 1, 2018
Ya I worked with them. We had to enable SSL and Reset our keystroke. Now it's working and all is GLORIOUS.
- Valued Contributor
- June 14, 2018
Hey all,
Also having this deployment problem. After dropping deploy.properties into the various locations (tried all of them), I get nothing but a spinning circle. Server.log shows that the deploy.properties file is being properly discovered.
I do have SSL enabled, with a valid just renewed commercial certificate, so it would seem like that shouldn't be a problem. (We've been using SSL for years).
One thing I do notice from the server.log file on the test client-
Unable to retrieve deployment policy from https://<mybackupserverurl.edu>:4285; response 404 {"data":null,"error": [{"primaryErrorKey":"DEPLOYMENT_PACKAGE_NOT_FOUND","otherErrors":null}],"warnings":null}
I do have a Deployment policy configured, and everything seems to be set properly. We are using LDAP for CrashPlan user names, but the user name script doesn't help us for this because we do not use LDAP on most of the computers.
 +15
+15- Contributor
- June 14, 2018
You can view the crash plan install log to see what it's doing. If it's seeing your deploy.properties file, then you need to see why youre getting a 404 from the server. Can you pull down the URL from the crash plan install log file manually? Do you use a proxy server? The installer will use a system proxy regardless of other settings.
- Valued Contributor
- June 15, 2018
No proxies in place.
From Install.log, I can see that it's finding the deploy.properties file and copying to /Library/Application Support/CrashPlan.
> > Can you pull down the URL from the crash plan install log file manually?
There is nothing in install.log that even remotely looks like a URL, so that would seem a non-starter.
From service.log, this is the only line that gives me any information about where it's looking {I changed the server url to protect the innocent and not-so-innocent):
[06.14.18 14:37:29.021 INFO EventBus 0 ice.deployment.DeploymentService] Deploy:: Retrieving deployment package from https://<myserver.edu>:4285
 +5
+5- Contributor
- June 15, 2018
We also found a bug, that the installer does not create a LaunchAgents folder inside the users folder so Code42 icon in the Menu Bar cannot launch at login, the below script fixed this issue, run before installing CrashPlan. I do believe 6.72 has now fixed this problem
!/bin/bash
Get the Username of the currently logged user
loggedInUser=/bin/ls -l /dev/console | /usr/bin/awk '{ print $3 }'
Creates the folder LaunchAgents inside User's Library folder
mkdir /Users/$loggedInUser/Library/LaunchAgents
Changes the owner permission on the LaunchAgents folder to allow the user to write to it
/usr/sbin/chown $loggedInUser /Users/$loggedInUser/Library/LaunchAgents
- Valued Contributor
- October 9, 2018
Hi Folks,
I have been working on automating the deployment of CrashPlan this past week, and thought I would share what I came up with in this post, hoping someone would benefit from it.
First, you need to create a user that has api read access to computer objects in your organization. You would need to consult code42 support documentation or reach out to their customer champions to get the best advice on how to go about that.
Second, you should create a deployment under "Client Management" on your code42 server. make a copy of the deploy.properties information, as you would need it to populate the policy in Jamf Pro. You can find plenty of information on this on code42 support site.
Third, assuming you have the above, and have tested the credentials you can use the following script in your Jamf Pro instance. The script assumes that the local username is same as the CrashPlan account user name, and that it is being run from a self service policy from the profile of the user it is intended to backup.
#!/bin/bash
#############################################################################
# This script was intended to download and install the latest version of
# the Code42 CrashPlan app from an on-premise Code42 Server.
# writen by: Kamal Taynaz
# Senior Systems Engineer
# Carnegie Mellon University Qatar
#
# Use at your own risk
#############################################################################
# global variables
local_user=$(ls -l /dev/console | awk '{print $3}')
c42_tmp="/tmp/c42_tmp_folder"
c42_user=$4 #api user with read and console access to code42 server
c42_pass=$5 #api password for above user
c42_url=$6 #code 42 server url https://code42.example.com:4285
c42_host=$(echo ${c42_url} | awk -F[/:] '{print $4}') #code 42 server url FQDN code42.example.com
c42_deploy_token=$7 #deploy token from the deployment properties from code42 server
# check for previously installed app
echo "Checking for previously installed app..."
if [[ -d "/Applications/CrashPlan.app" ]]; then
echo "Found previous installation.."
echo "Removing previous installation..."
find "/Library/Application Support/CrashPlan" -type f -name *uninstall.sh* -exec sh {} ;
find "/Library" -type d -iname *CrashPlan* -exec rm -rf {} ;
find "/Users/${local_user}/Library" -type f -iname *CrashPlan* -exec rm -rf {} ;
echo "Previous installtion removed..."
echo "Staring new installtion process..."
else
echo "No installation found..."
echo "Staring installtion process..."
fi
# create temp working folder
if [[ -d "${c42_tmp}" ]]; then
echo "Found old temp folder..."
echo "Deleting old temp folder now..."
rm -rf "${c42_tmp}"
echo "Creating new code42 temp folder..."
mkdir -p "${c42_tmp}"
else
echo "Creating code42 temp folder..."
mkdir -p "${c42_tmp}"
fi
# find and eject CrashPlan disk image if found
find /Volumes -type d -name "*Code42CrashPlan*" -maxdepth 1 -exec hdiutil detach {} -quiet ;
# create .netrc file to store credetials
echo "Creating temp credetials file..."
echo "machine ${c42_host}" > "${c42_tmp}/.netrc"
echo "login ${c42_user}" >> "${c42_tmp}/.netrc"
echo "password ${c42_pass}" >> "${c42_tmp}/.netrc"
# create deploy properties file
echo "Creating deploy properties file..."
echo "DEPLOYMENT_URL=${c42_url}" > "${c42_tmp}/deploy.properties"
echo "DEPLOYMENT_POLICY_TOKEN=${c42_deploy_token}" >> "${c42_tmp}/deploy.properties"
echo "CP_SILENT=false" >> "${c42_tmp}/deploy.properties"
# construct URL to download latest app
echo "Conneting to code42 server with temp credetials..."
api_token=$(curl -X POST -sk --netrc-file "${c42_tmp}/.netrc" ${c42_url}/api/authToken
| perl -pe 's/"metadata":.*"data"://; s/^"//; s/",$//'
| sed -e 's/","/-/' -e 's/[^a-zA-Z*0-9*-]//g')
echo "CrashPlan api token is ${api_token}"
echo "Deleting temp credetials file..."
rm -f "${c42_tmp}/.netrc"
echo "Conneting to code42 server with token..."
app_productVersion=$(curl -X GET -sH "Authorization: token ${api_token}" ${c42_url}/api/Computer?osName=mac
| python -m json.tool | grep productVersion
| awk '{print $2}' | sed -e 's/[^0-9*.]//g'
| sort -u -t. -k 1,1n -k 2,2n -k 3,3n -k 4,4
| tail -n1)
echo "Creating version properties file..."
echo "Collecting app version information..."
echo "Lastest product version is ${app_productVersion}..."
curl -X GET -sH "Authorization: token ${api_token}" ${c42_url}/api/Computer?osName=mac
| python -m json.tool | grep -E "(version|productVersion|buildVersion)"
| grep -C 1 "${app_productVersion}" | tail -n3 | sed -e 's/^ *//' -e 's/[^a-zA-Z*0-9*.* ]//g' > "${c42_tmp}/version.properties"
app_version=$(grep version "${c42_tmp}/version.properties" | awk '{print $2}')
echo "Lastest version is ${app_version}..."
app_buildVersion=$(grep buildVersion "${c42_tmp}/version.properties" | awk '{print $2}')
echo "Lastest build version is ${app_buildVersion}..."
app_download="Code42CrashPlan_${app_productVersion}_${app_version}_${app_buildVersion}_Mac.dmg"
echo "Installer to be downloaded is ${app_download}..."
app_download_link="${c42_url}/client/installers/${app_download}"
echo "Installer download link is ${app_download_link}..."
# download the code42 crashplan app
echo "Downloading CrashPlan Installer..."
curl -o "${c42_tmp}/crashplan.dmg" "${app_download_link}" --progress --retry 5
# convert the disk image and added properties file
echo "Converting DMG to read/write..."
hdiutil convert -format UDRW "${c42_tmp}/crashplan.dmg" -o "${c42_tmp}/crashplan_tmp.dmg" -quiet
echo "Mounting DMG disk image..."
hdiutil attach "${c42_tmp}/crashplan_tmp.dmg" -quiet -nobrowse
echo "Copying deploy.propertis to DMG..."
find /Volumes -type d -name "*Code42CrashPlan*" -maxdepth 1 -exec cp "${c42_tmp}/deploy.properties" {} ;
echo "Ejecting DMG disk image..."
find /Volumes -type d -name "*Code42CrashPlan*" -maxdepth 1 -exec hdiutil detach {} ;
echo "Converting DMG back to read-only..."
hdiutil convert -format UDRO "${c42_tmp}/crashplan_tmp.dmg" -o "${c42_tmp}/crashplan_final.dmg" -quiet
# install the application
echo "Mount final DMG disk image..."
hdiutil attach "${c42_tmp}/crashplan_final.dmg" -quiet -nobrowse
echo "Locate CrashPlan installer volume..."
c42_vol=$(find "/Volumes" -type d -name "*Code42CrashPlan*" -maxdepth 1)
echo "CrashPlan volume is ${c42_vol}..."
echo "Locate CrashPlan installer path..."
c42_pkg=$(find "${c42_vol}" -type f -iname "*install*pkg*" -maxdepth 1)
echo "CrashPlan installer path is c42_pkg..."
echo "Installing Code42 CrashPlan..."
installer -package "${c42_pkg}" -target LocalSystem
echo "Ejecting DMG disk image..."
find /Volumes -type d -name "*Code42CrashPlan*" -maxdepth 1 -exec hdiutil detach {} ;
echo "Removing temp folder now..."
rm -rf "${c42_tmp}"
echo "Done."
exit 0Forth, after uploading the script to jamf pro or jamf admin, set the following option label. You can obviously name the label what you like, but be sure they correspond to the correct information.
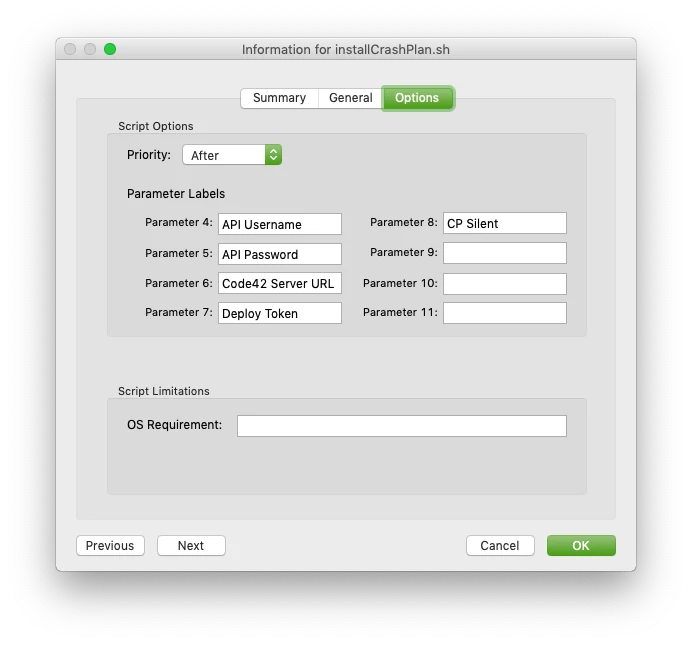
Fifth, Create your policy, and populate the script information required for the variables. Scope the policy to a test machine and let me know how it worked out for you.
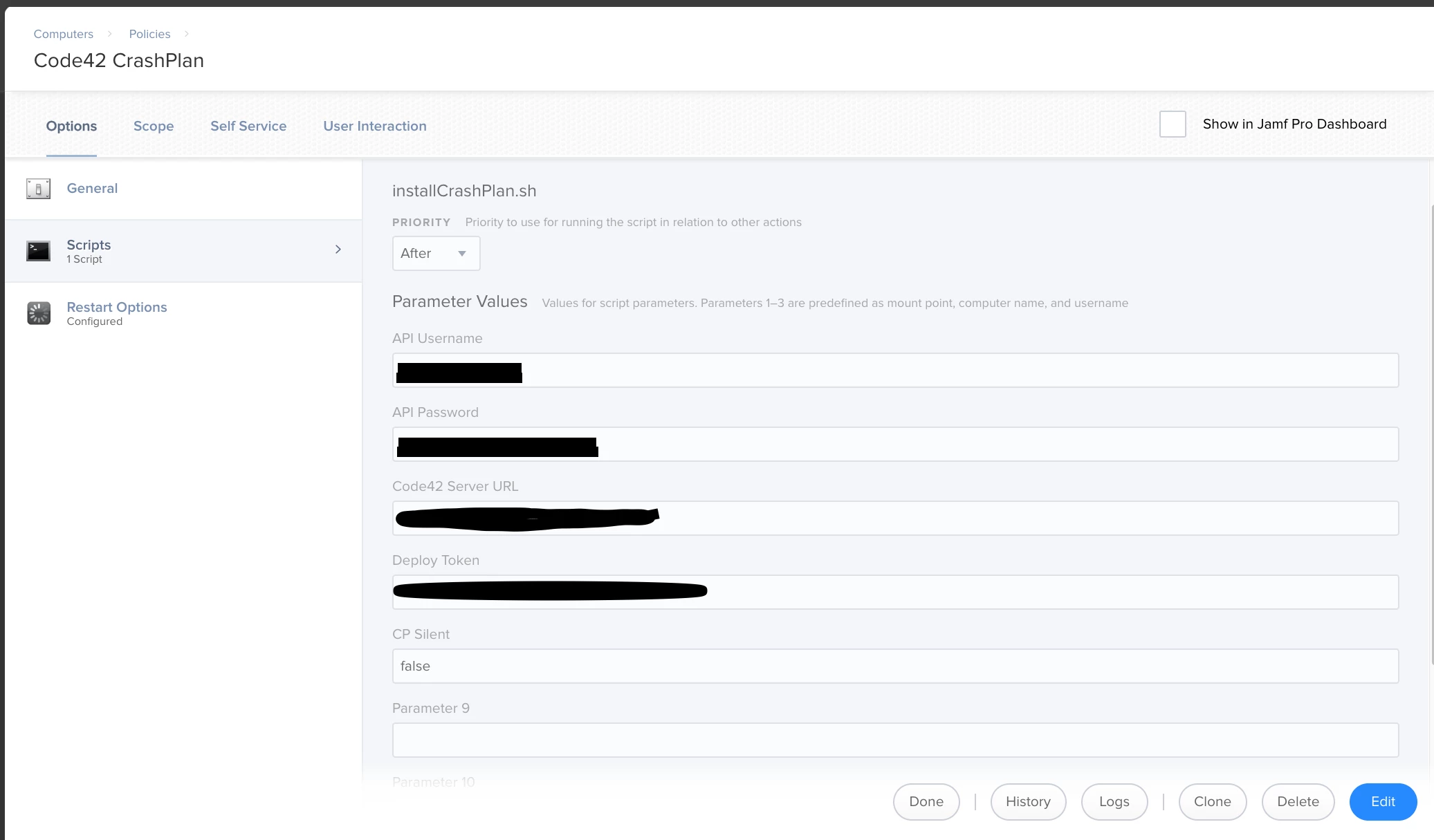
Again, hope this is useful for someone. Its definitely a time saver.
Best wishes,
Kamal
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.
Scanning file for viruses.
Sorry, we're still checking this file's contents to make sure it's safe to download. Please try again in a few minutes.
OKThis file cannot be downloaded
Sorry, our virus scanner detected that this file isn't safe to download.
OK

