Lately, every Mac that has tried to perform user-initiated enrollment in Jamf has been met with "Device Signature Error in the jamf log.
To resolve, we perform these steps:
1. Remove Jamf Framework
2. Remove Jamf CA certificate
3. Remove contents of /Library/Application Support/JAMF/Downloads/
4. Run this command: sudo update_dyld_shared_cache -force
5. Delete the mac from Jamf console
6. Run the QuickAdd package on the mac
7. Approve the Device Management Profile on the Mac
8. Assign the user to the Mac in the Jamf Pro console
This issue seems to have started with MacOS 10.14.5, but that may be coincidence. I have attached screenshots from an affected Mac. We have 3 macs that are broken right now, and 2 that were repaired using the procedure above.
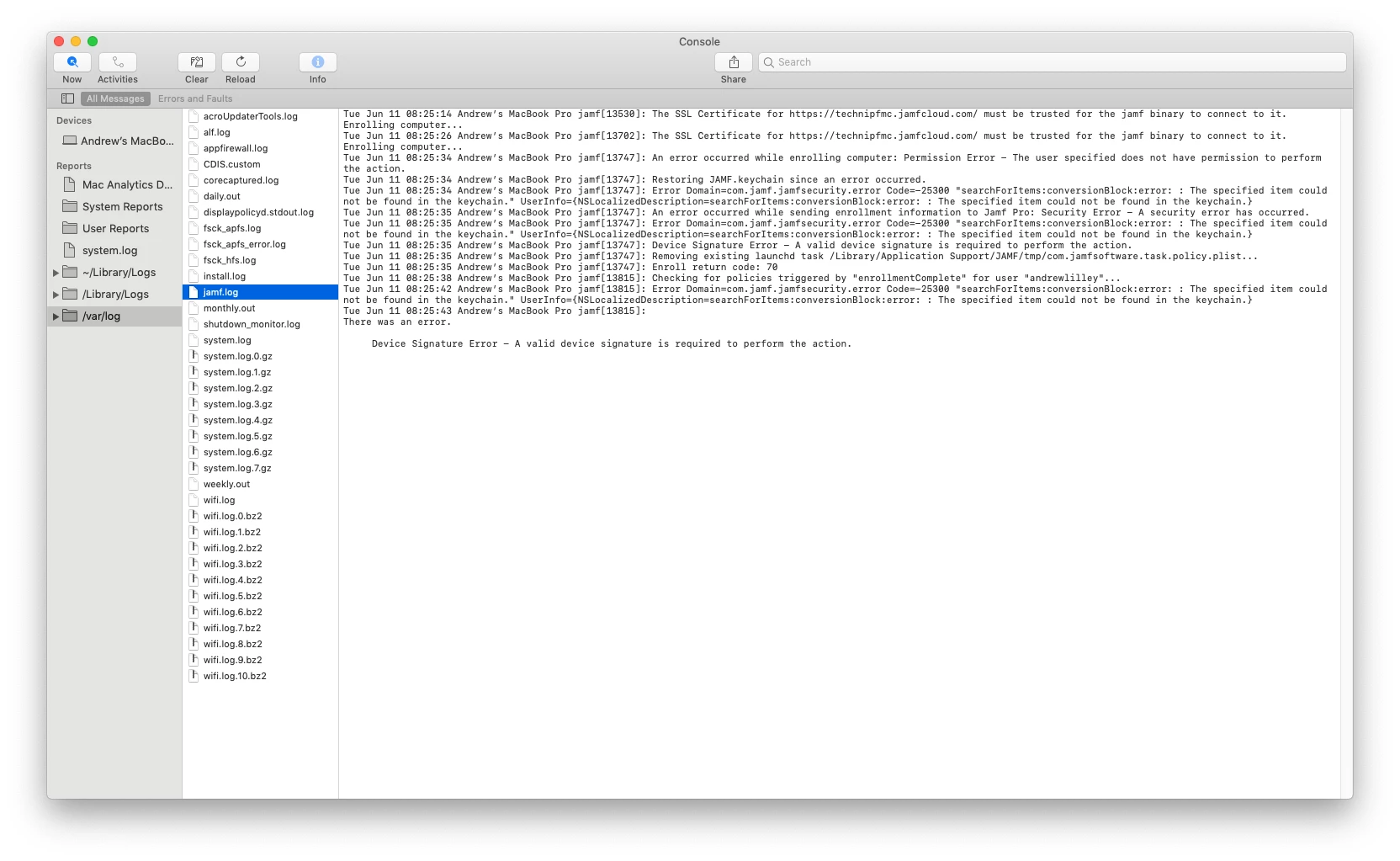
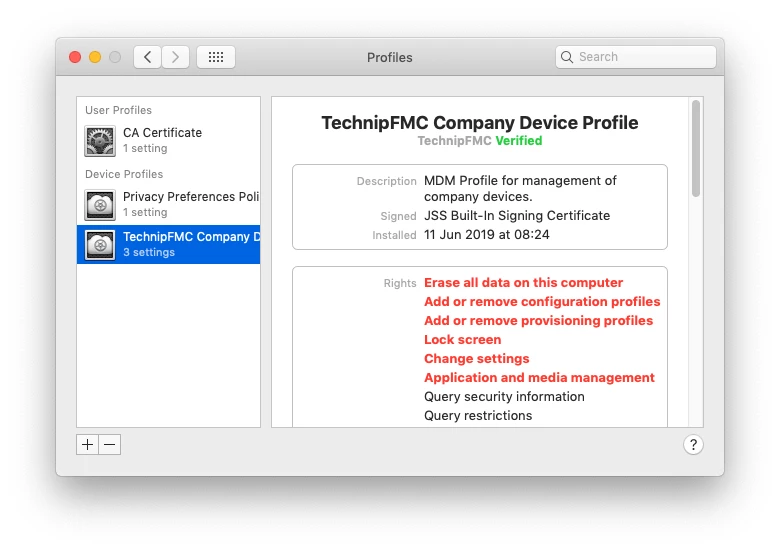
Anyone else seeing encountering this?












