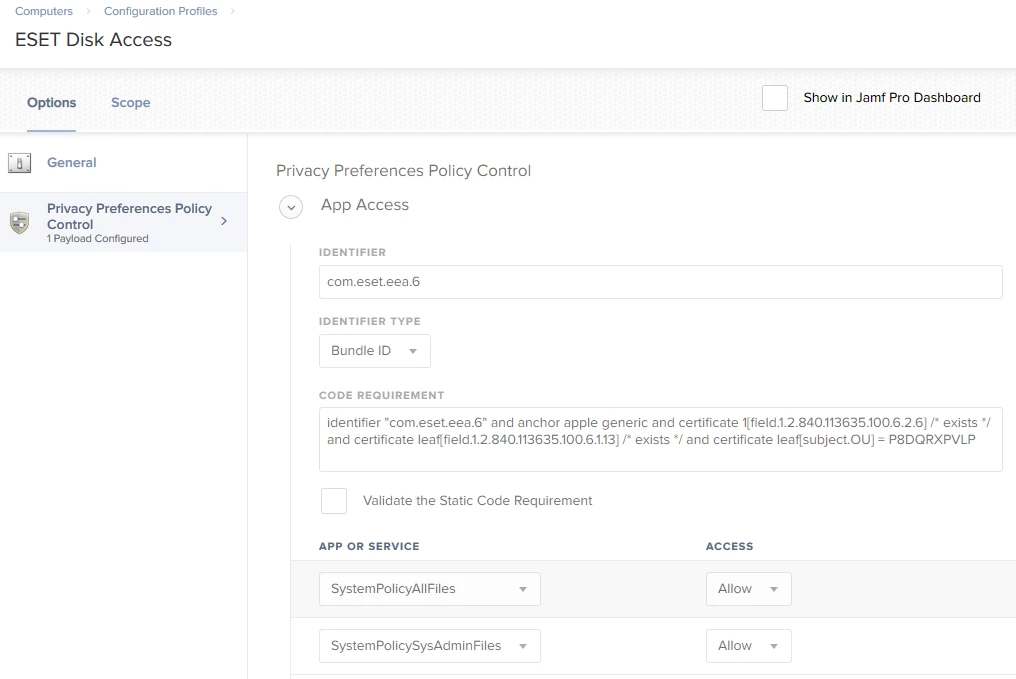
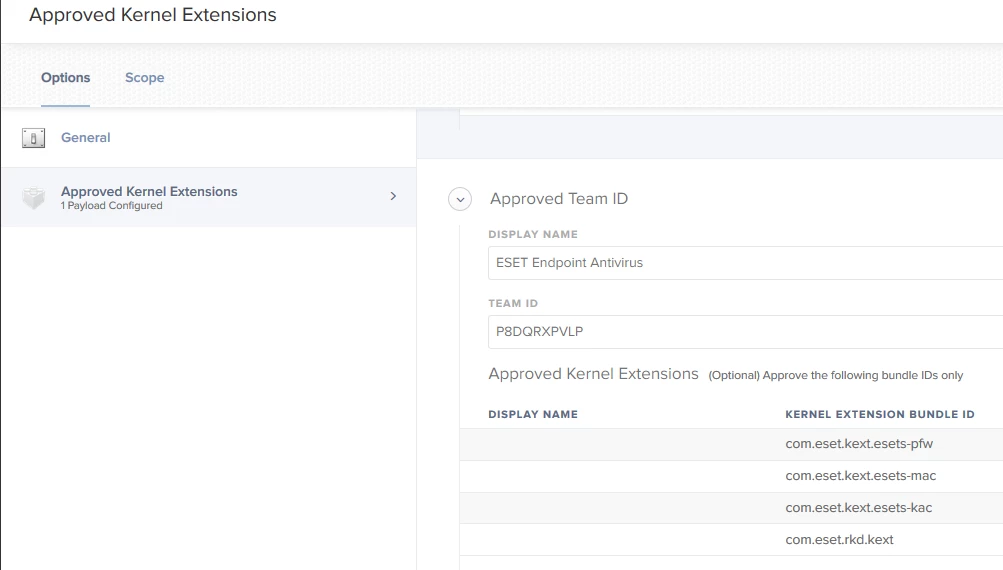
I am testing a migration from Microsoft SCEP to ESET EndPoint Security. I have the package installing and activating, but on launch ESET prompts requesting full disk access. Has anyone gotten around this?
The ESET support page says this must be done manually on 10.14
I am testing with 10.14.1 and JAMF Pro 10.8