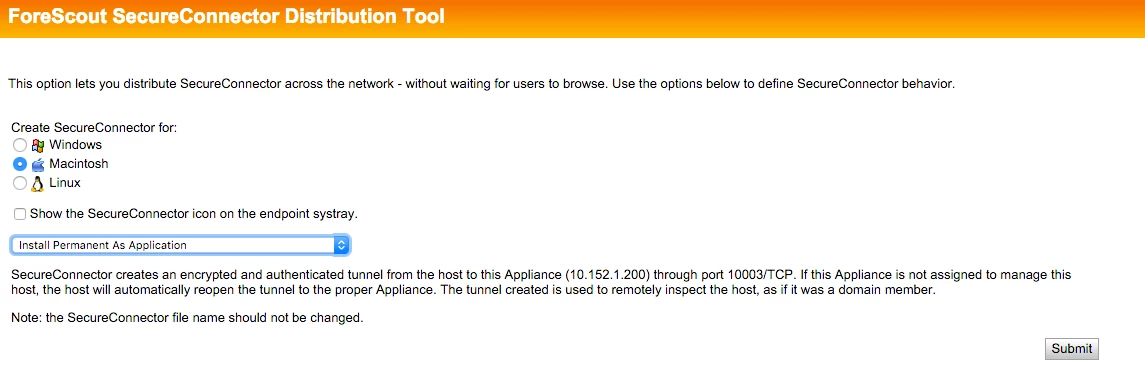
Hey guys, I created a bash file. Just put it in your scripts and deploy... It works perfectly.
[START CODE]
!/bin/sh
Downloading OSX Update Package to /tmp on the host
curl -o /tmp/update.tgz http://IPADDRESS/SC_packages/update.tgz; sleep 3
Extracting update.tgz to /tmp
tar -zxvf /tmp/update.tgz -C /tmp; sleep 3
Installing SecureConnector as a Daemon/Dissolvable w/ visible/invisible menu bar icon
echo '[Enter Password]' | sudo -S /tmp/Update/Update.sh -t daemon -v 1; sleep 3
Checking/Starting processes in case they did not start on install
daemon_pid=ps auxww | grep -v grep | egrep "ForeScout SecureConnector.-daemon" | awk '{print $2}'
agent_pid=ps auxww | grep -v grep | egrep "ForeScout SecureConnector.-agent" | awk '{print $2}'
daemon_plist=/Library/LaunchDaemons/com.forescout.secureconnector.daemon.plist
agent_plist=/Library/LaunchAgents/com.forescout.secureconnector.agent.plist
if [[ -z "$daemon_pid" && -z "$agent_pid" ]]; then
#Starting Daemon process
launchctl unload $daemon_plist
launchctl load $daemon_plist
#Starting GUI process
launchctl unload $agent_plist
launchctl load $agent_plist
elif [[ ! -z "$daemon_pid" && -z "$agent_pid" ]]; then
#Starting GUI process
launchctl unload $agent_plist
launchctl load $agent_plist
fi
Clean-up a little
rm -rf /tmp/update.tgz /tmp/Update/
[END CODE]