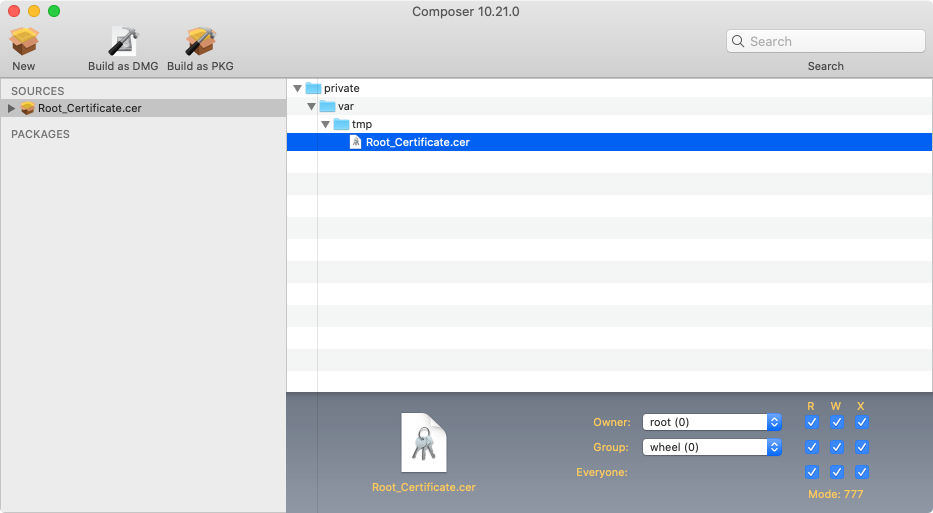
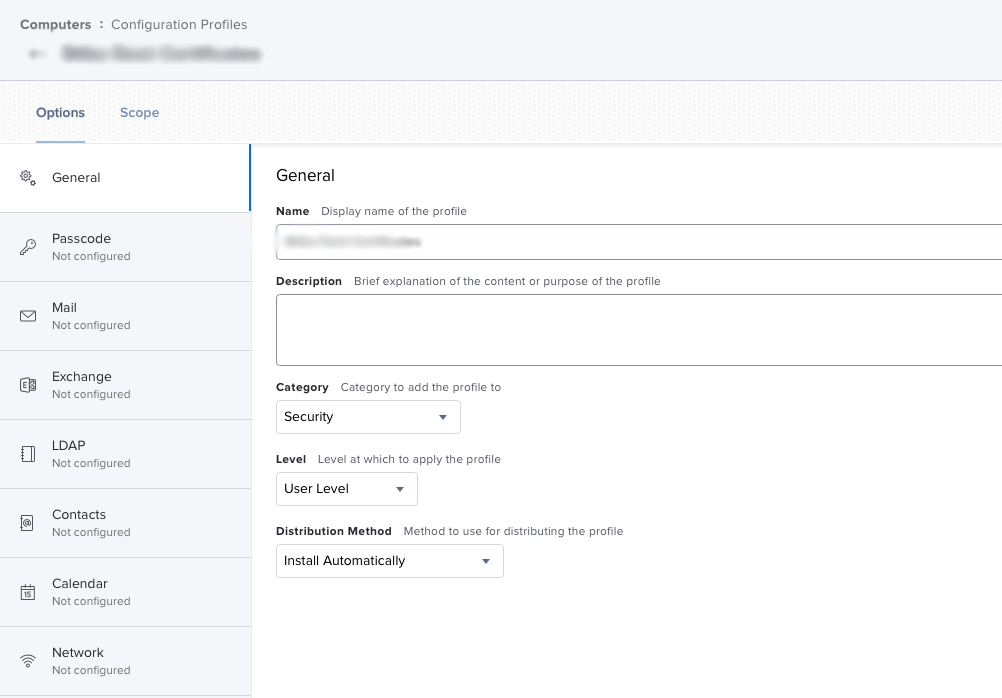
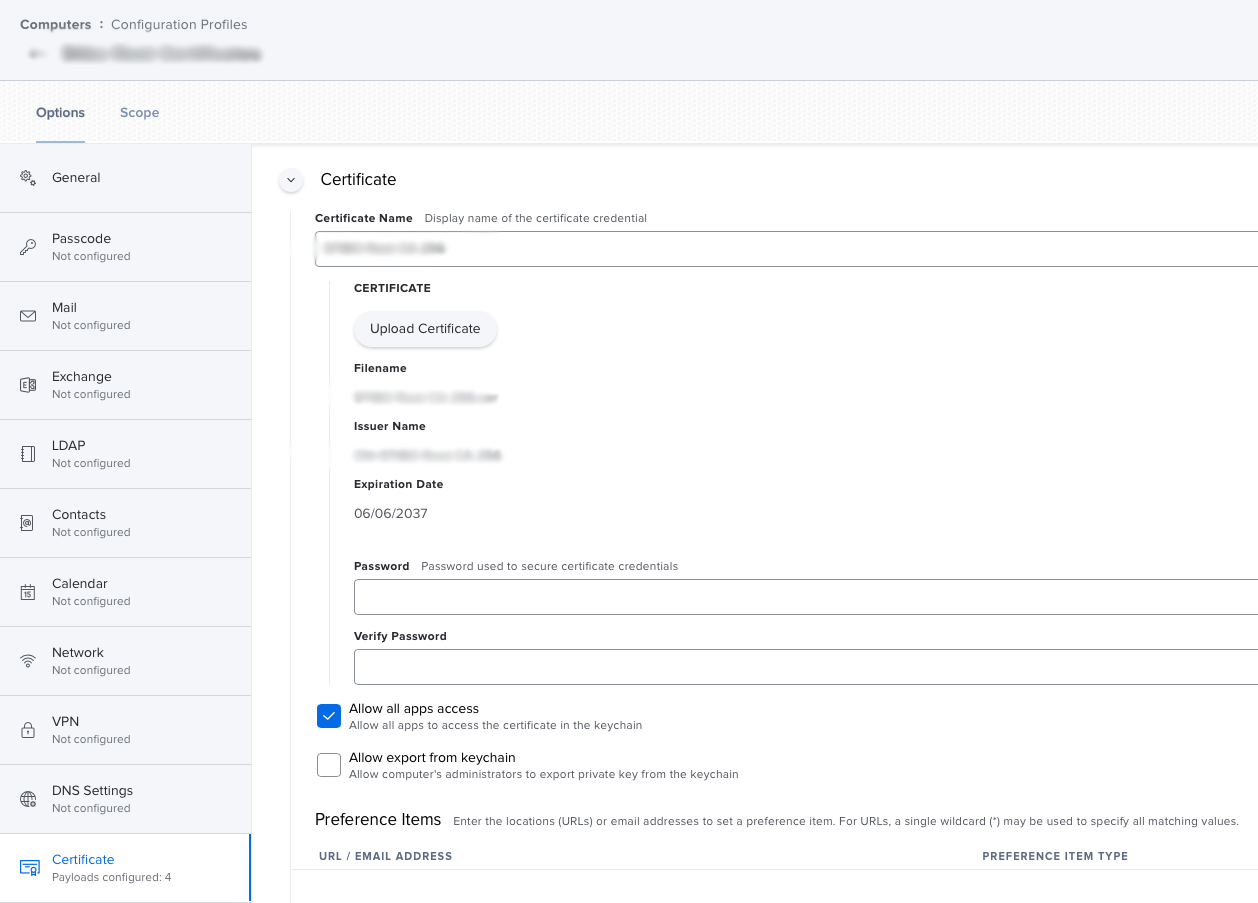
Hello, we where able to deploy a self signed certificate via JAMF configuration profile using the certificate manager.
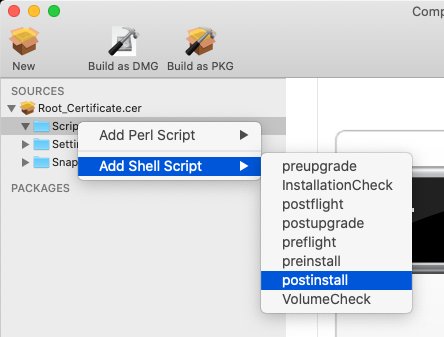
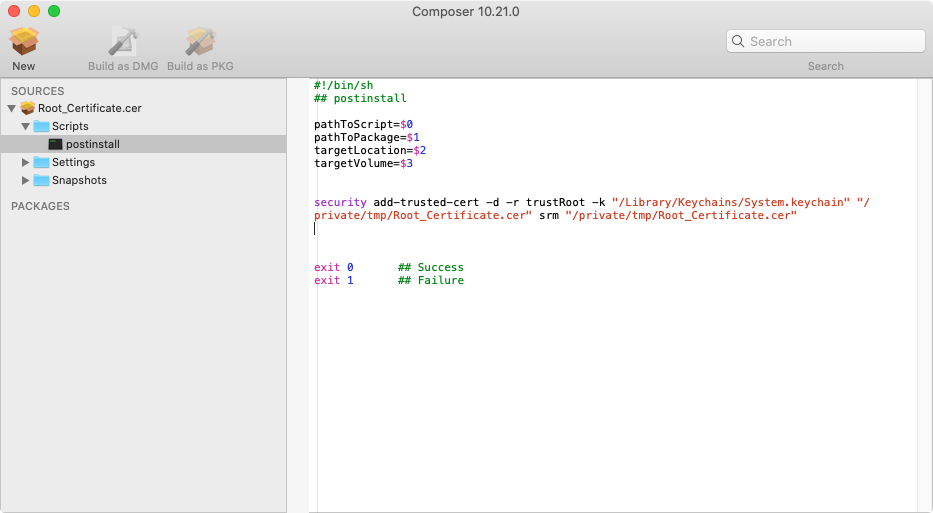
Unfortunately the certificate is not set to trust. I can set it to trust via command line but I would need to find a way to deploy the certificate file to the macbook laptop then run a trust command via script. Unfortunately there seem to be no documented way to do this.
How can I achieve my goal. How can I deploy a self signed certificate and tell all our jamf computers to always trust that certificate.