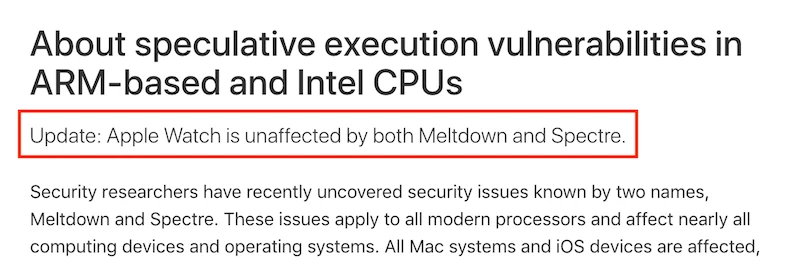
Hello,
I have been searching the web to see if anyone has any information on new macOS security updates regarding this security risk. I have seen that this issue may have been resolved in 10.13.2 and 10.13.3, but no word on those Macs still on El Capitan or Sierra. Has anyone else come across anything?