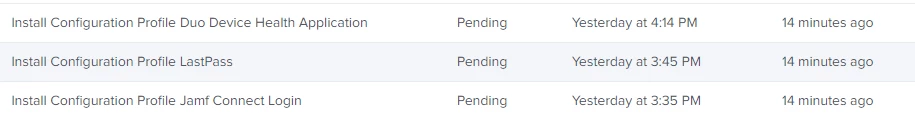
I am having a handful of systems with Configuration Profiles stuck in pending state. Does anyone know of a fix for this?
These systems are all Automatic Device Enrolled, they are checking regularly to jamf. I have tried having them reboot, sending blank push from management commands.
These commands have been pending for months.