We are using Jamf Device Compliance with InTune.
Following this tech paper we have it working fairly well. Technical Paper: Integrating with Microsoft Intune to Enforce Compliance on Mac Computers Managed by Jamf Pro 10.43.0 or Later
When the end user goes through computer registration and JamfAAD opens they are prompted to "Always Allow" "Microsoft Workplace Join Key". This is expected and documented here. (Although it would be great to have a smoother workflow)
Our issue is the certificate in the login keychain for Device Compliance is not trusted for some reason. (See attached image)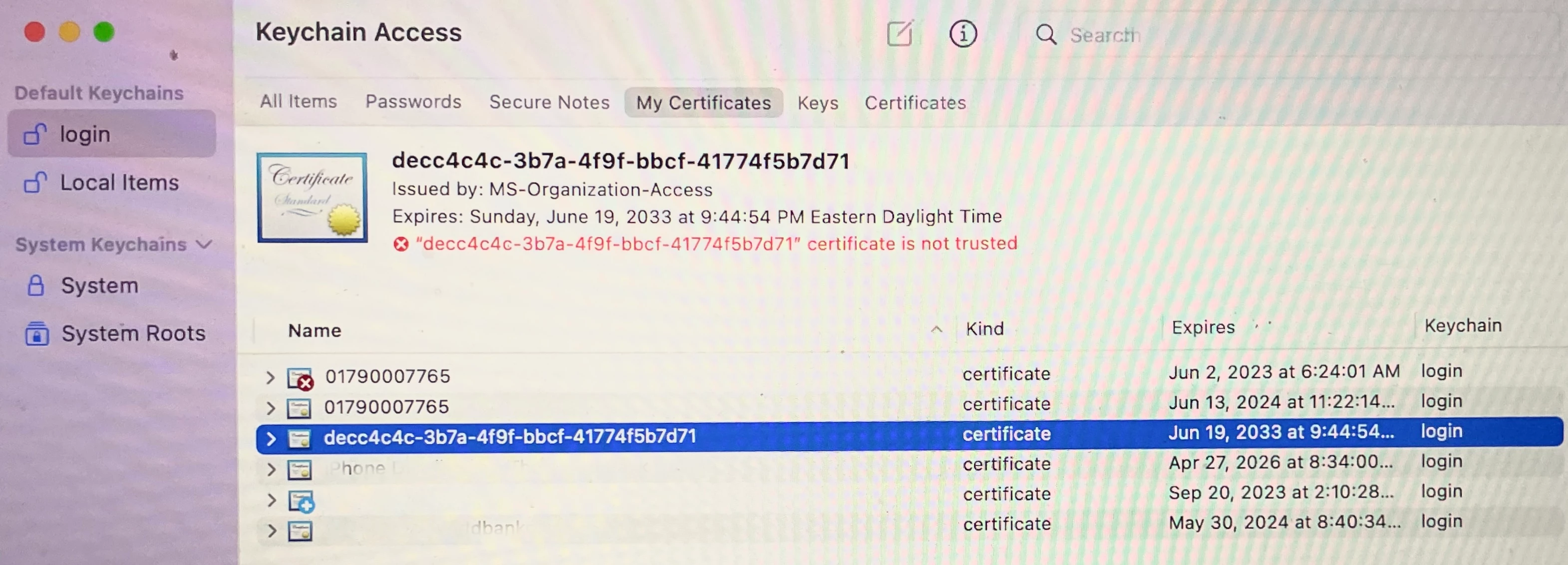
The cert seems to be issued by "MS-Organization-Access" I don't have that CA and our Azure folks don't seem to know about it either.
Thoughts?
Eric