Hello, Using hybrid joined Azure, we appear to have an issue with our Conditional Access configuration between Jamf and Entra. We have configured Jamf Device Compliance with a Compliance Test Group and an Application Group, the connection verification status: Success between Jamf and Intune is confirmed and partner compliance management configured.
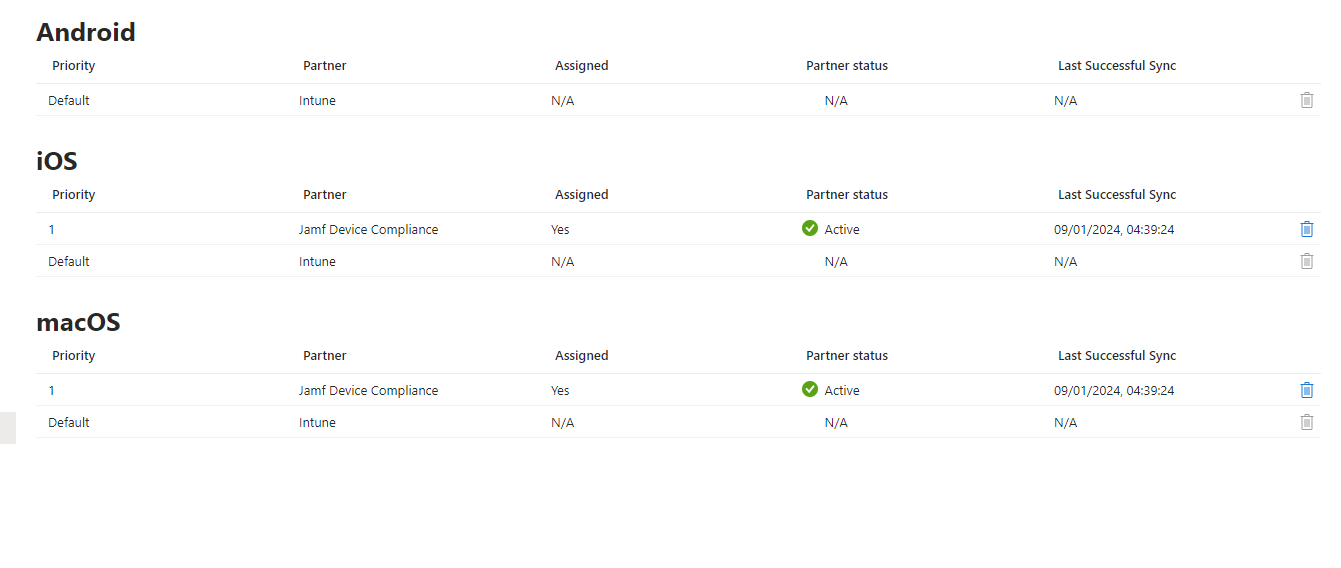
A group of test Mac’s in Jamf have Company Portal and Intune integration policies installed and they are registered in Entra
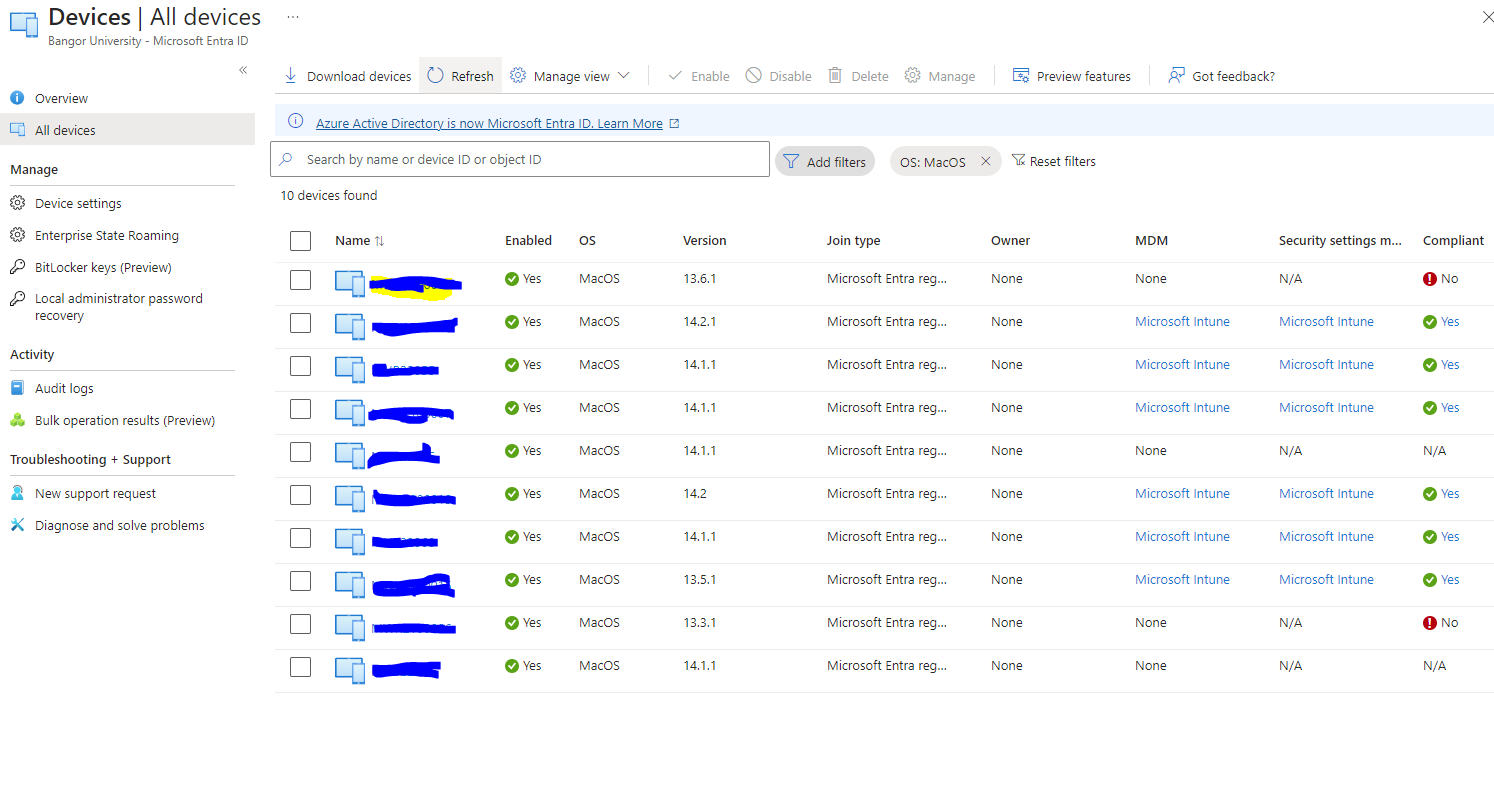
We have configured Conditional Access policies in Intune and targeted all cloud apps but when we run the CA policy we are locked out of Cloud Apps because according to Entra Sign-in logs the Mac is non-compliant
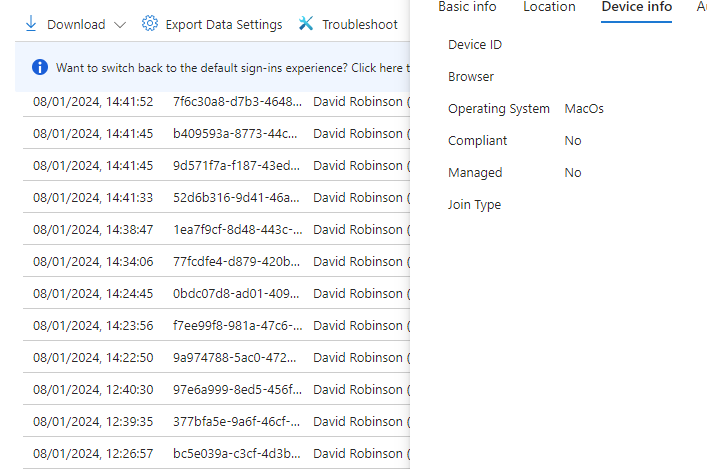
Am I missing something?


