Question
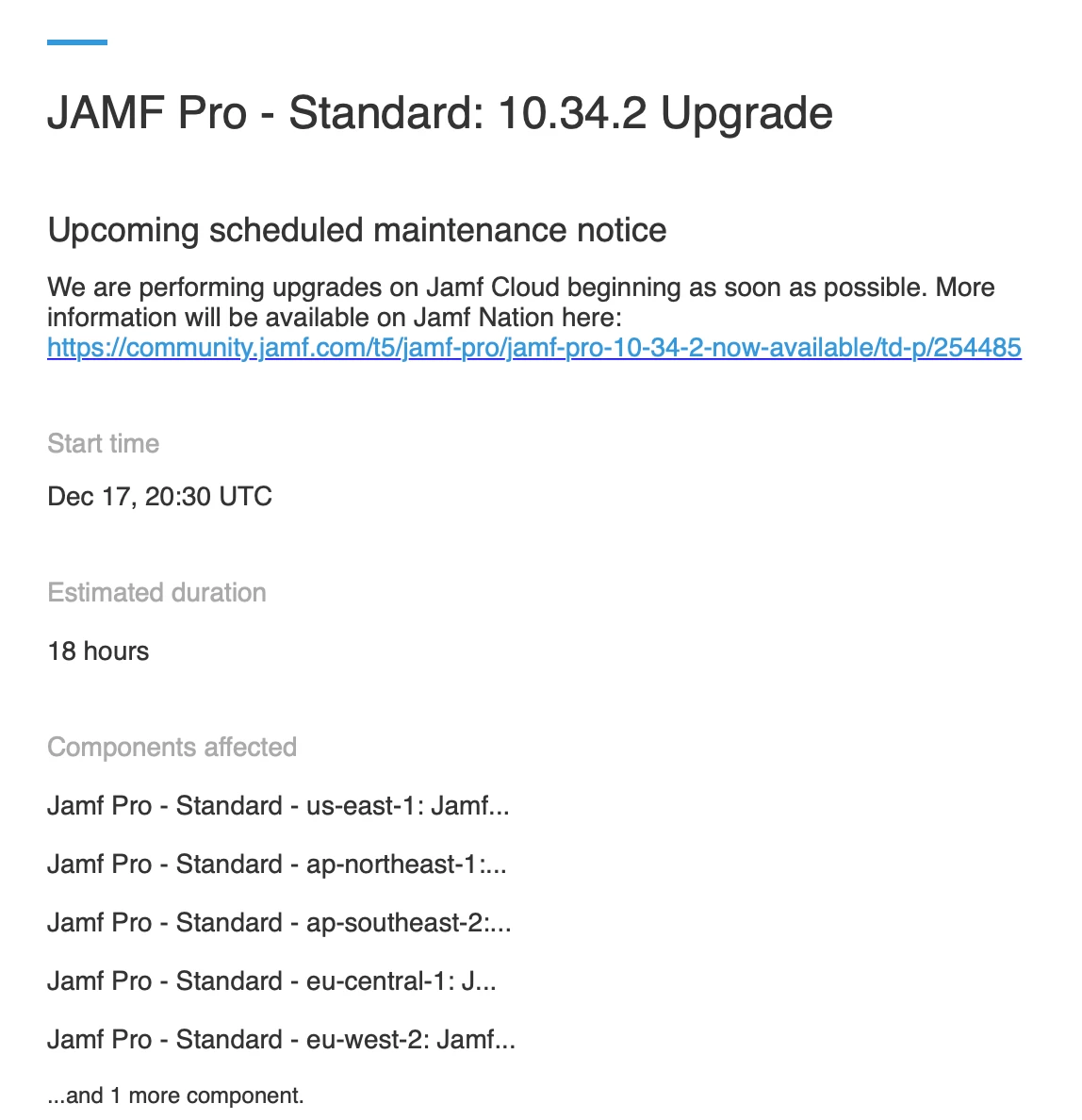
Jamf Pro 10.34.2 Now Available
 +10
+10Hello Jamf Nation,
Today we're releasing an update for Jamf Pro that addresses critical security issues CVE-2021-44228 and CVE-2021-45046. For details on how we’re addressing these vulnerabilities across the Jamf platform, please see this Jamf Nation post. Because keeping our customers’ environments secure is of the utmost importance, we’ll continue to be very intentional about when and how we communicate.
We strongly recommend that you upgrade to Jamf Pro 10.34.2 as soon as possible. Customers utilizing our cloud-based products have had the vulnerability mitigated through layered security controls. We are confident that these mitigations are effective against all known attacks. Out an abundance of caution, we are releasing Jamf Pro 10.34.2 to include log4j 2.16 and mitigate all currently known log4j vulnerabilities.
Please read the resolved issues section of the release notes for more information. Additional details on the resolved vulnerability will be made available on a future date to allow for Jamf Pro instances to be updated before full disclosure.
We will also be sending this information via email to primary technical contacts at affected organizations.
Thank you!
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.