Hi All,
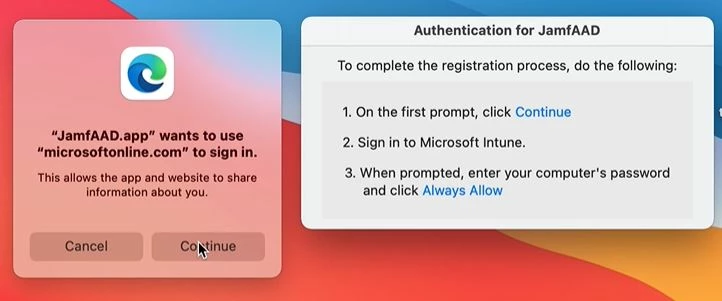
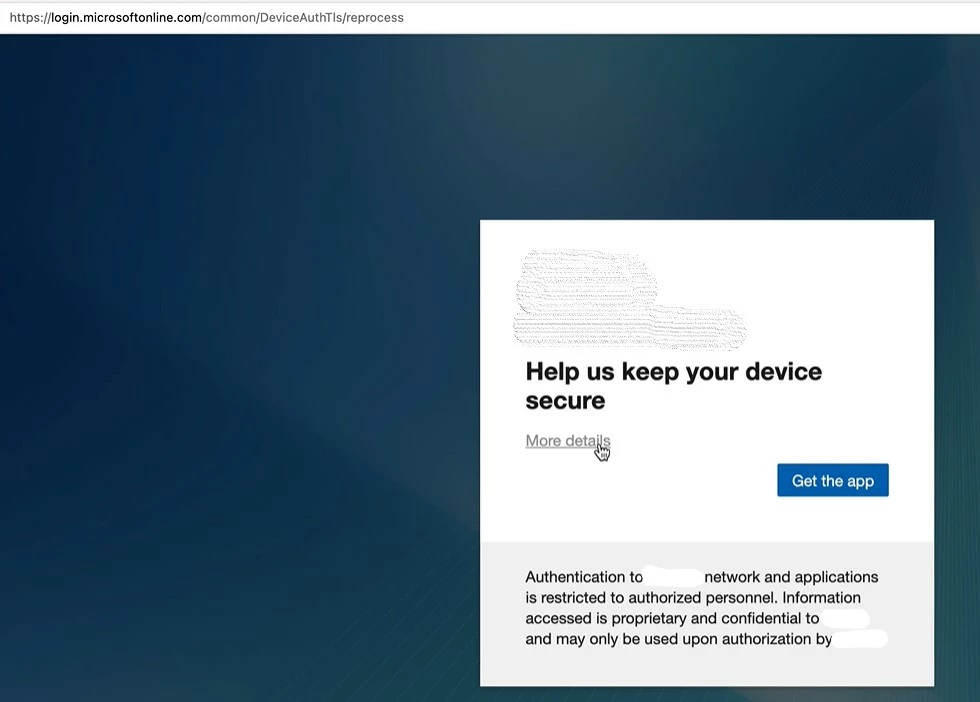
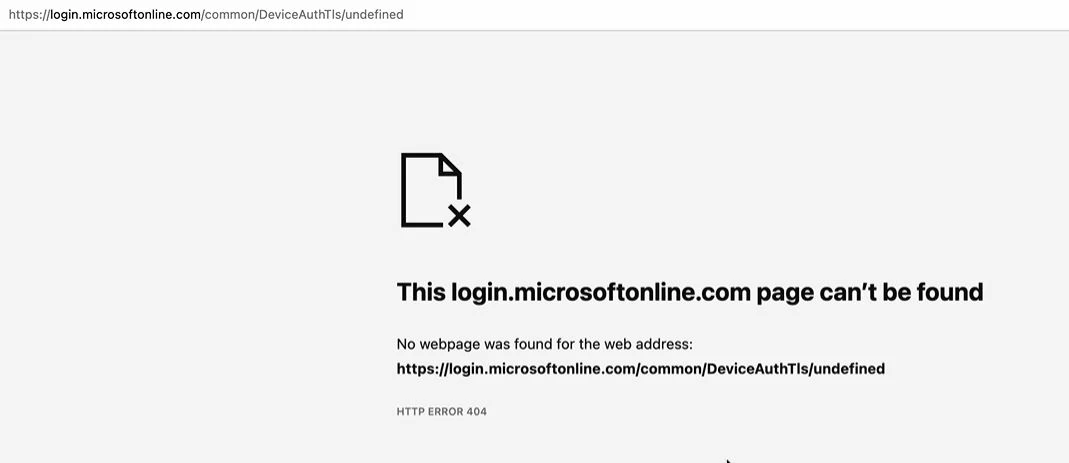
One of my user is getting the below pop up and after clicking on Get App it is redirecting to a weird broken link. This user is already registered in Intune/Azure AD and it just randomly started to happen. I am mostly curious about the link. Any ideas where this is coming from?