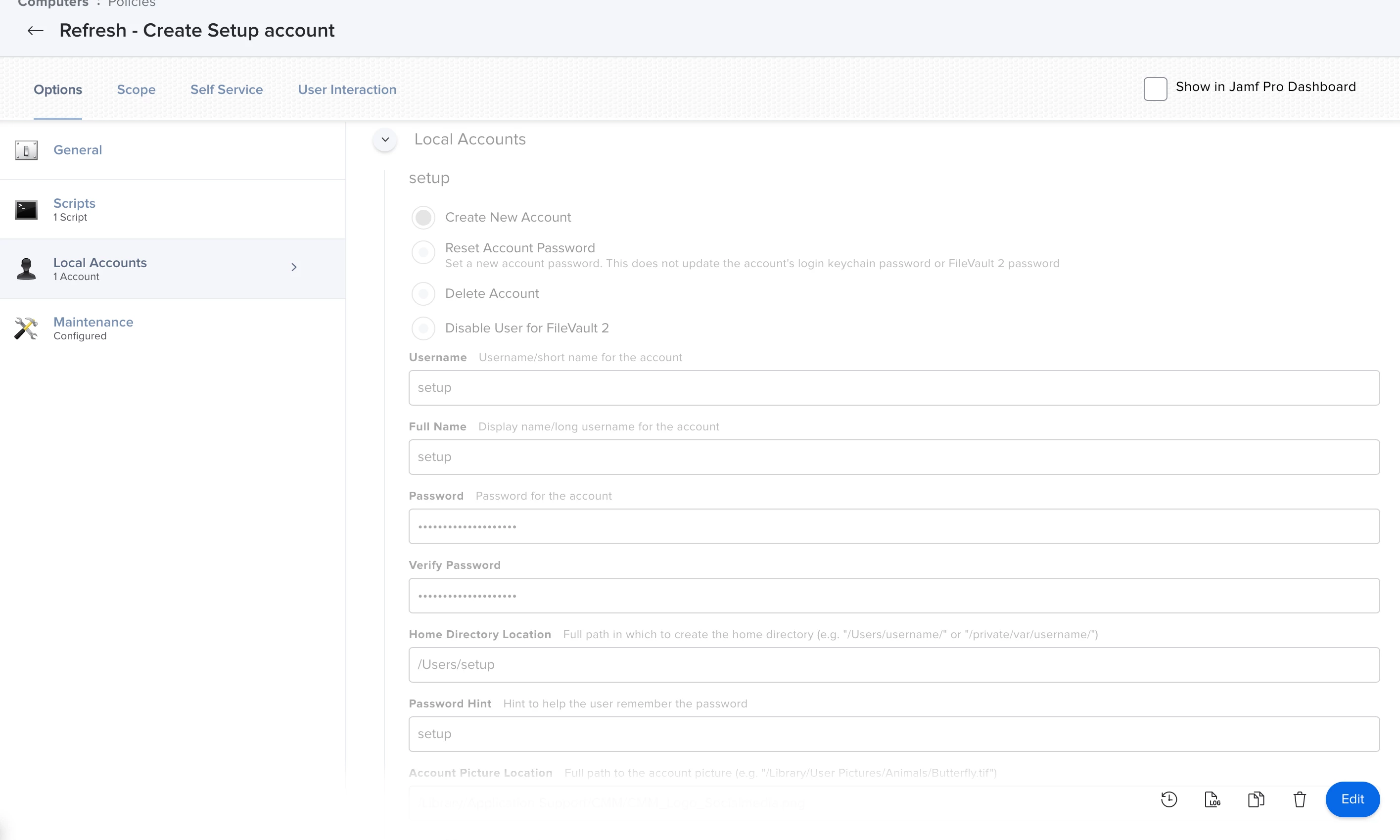
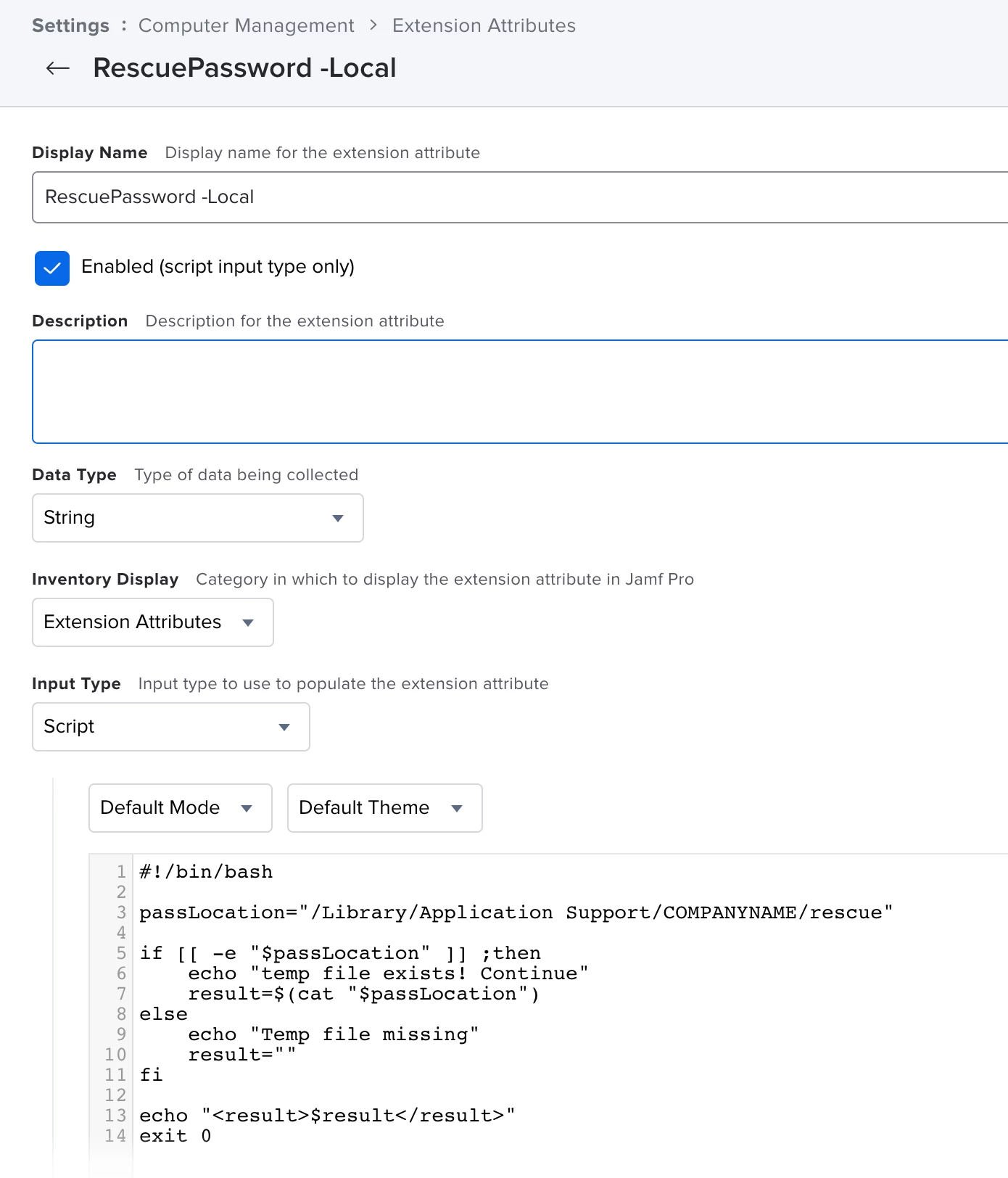
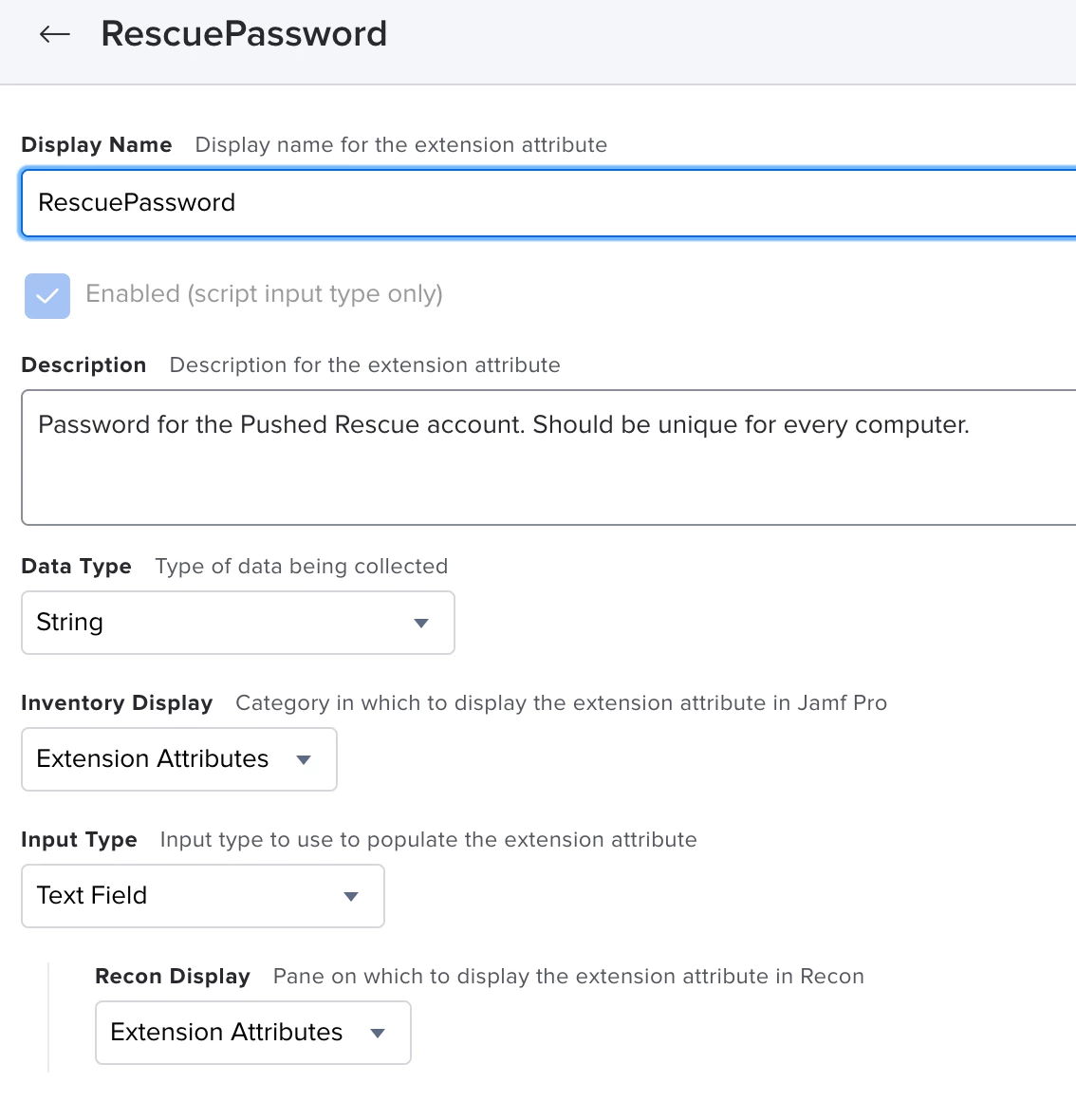
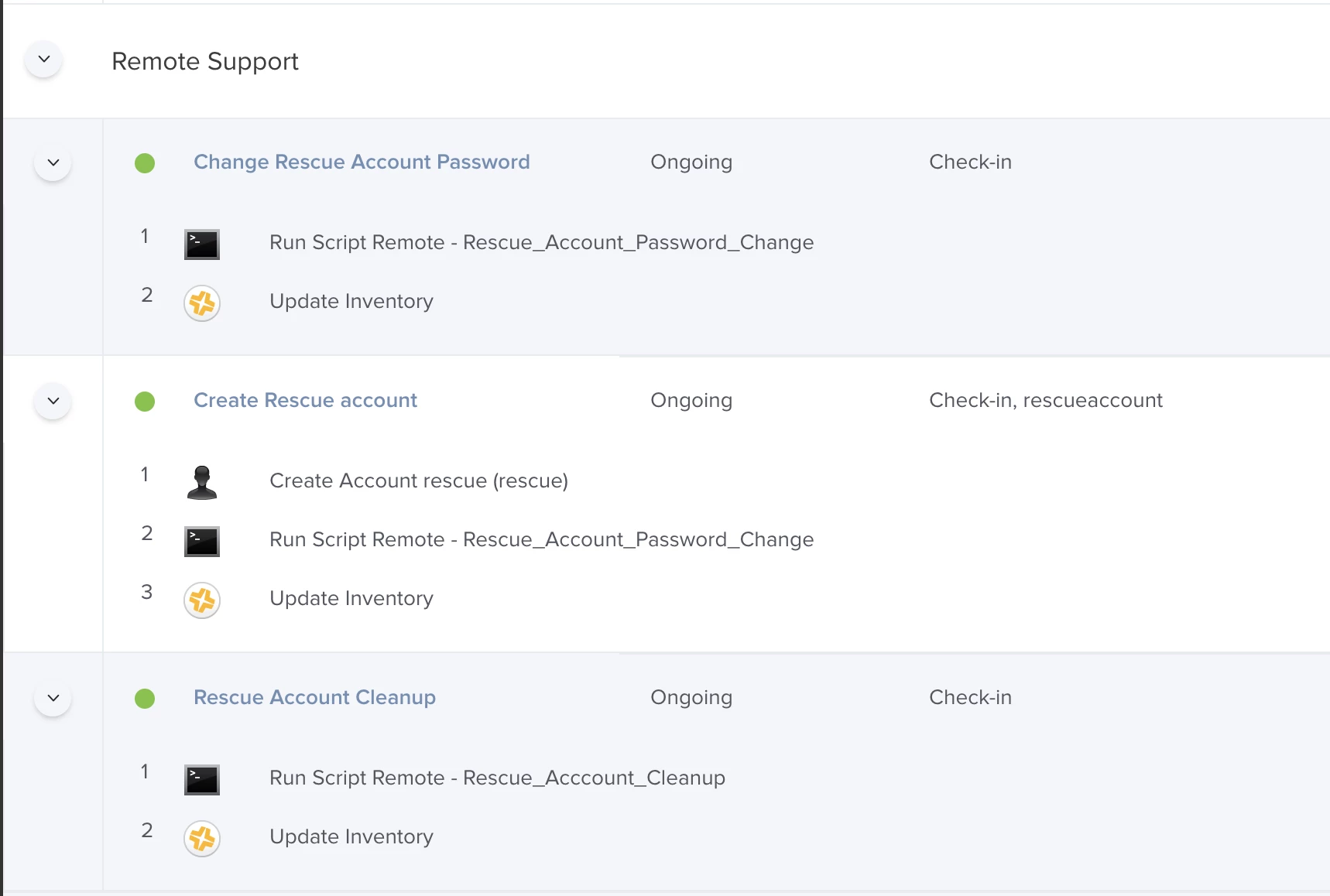
I have no doubt that this has been discussed before but I can't seem to find any discussions relevant to my scenario.
In the event that a user locks themselves out from their machine, how can I push a policy to reset the local account password or even create a new account when the user is unable to login and the administrator is unable to get hands on the machine?