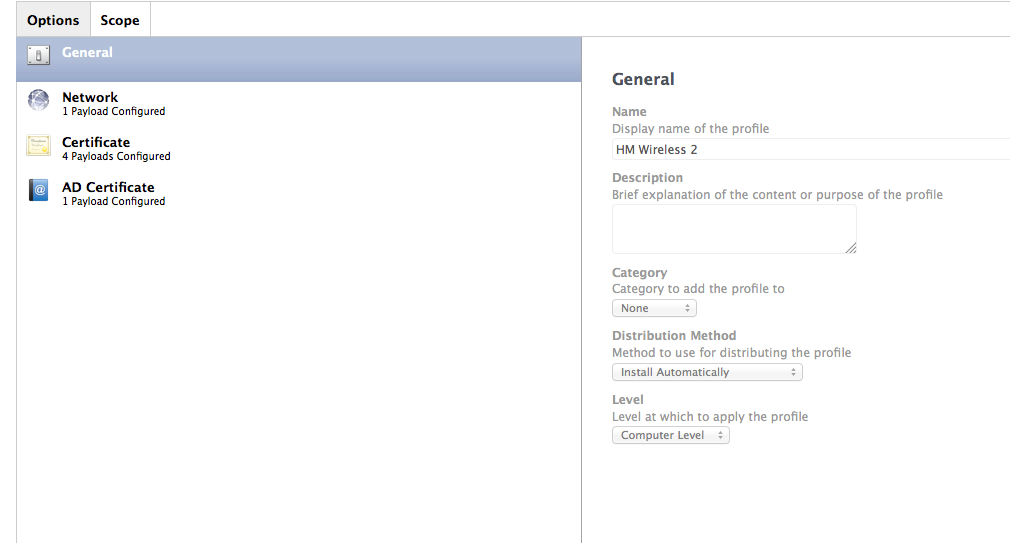
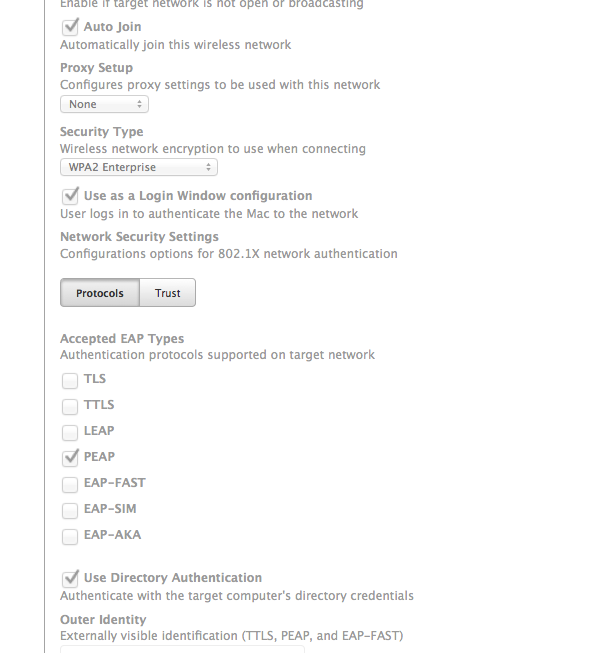
Has anyone successfully set up both types of authentication? What I am trying to accomplish:
- This is a wireless-only lab.
- As the machine sits on the login window it connects to our 802.1X wireless with machine Directory Authentication.
- When a user logs in with AD credentials, it uses those to authenticate as a Login Window Configuration.
The reason behind this is we have many network rules set up based on username, but when no one is logged into the computer we still want it to get updates from the munki and JSS servers.
I created a Configuration Profile with both payloads and it defaults to the Login Window Configuration and ignores the Directory Authentication. When I test them by having only one at a time, they both work flawlessly by themselves. It is when they are both configured at the same time I have issues.
It does work if I use a non-.1X network and a .1X Login Window Configuration at the same time. I can create a Configuration Profile with two network payloads: one to connect to the non .1X SSID while on the login window and one to authenticate using the user's AD credentials when they log in. That works fine. This leads me to believe that it is unintended for it to fail when using two .1X payloads. I'd prefer to always have it connected to the .1X network, but we may have to do it this way.