Hi,
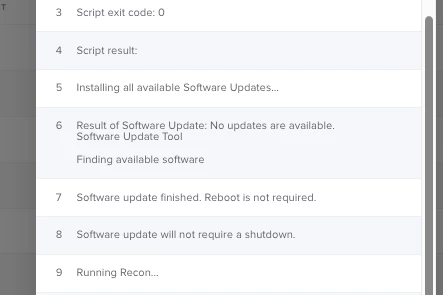
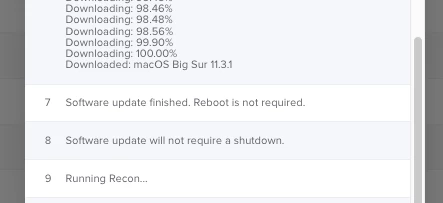
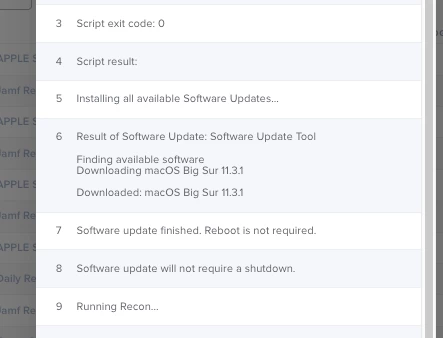
I am trying to do minor software updates via a policy, and I have a strange result on macOS 11. The targeted devices (running 11.2.3) download the 11.3 installer, and then the log claims "reboot not required" - so the update does not get installed.
Any idea what is wrong there?