Hey everyone,
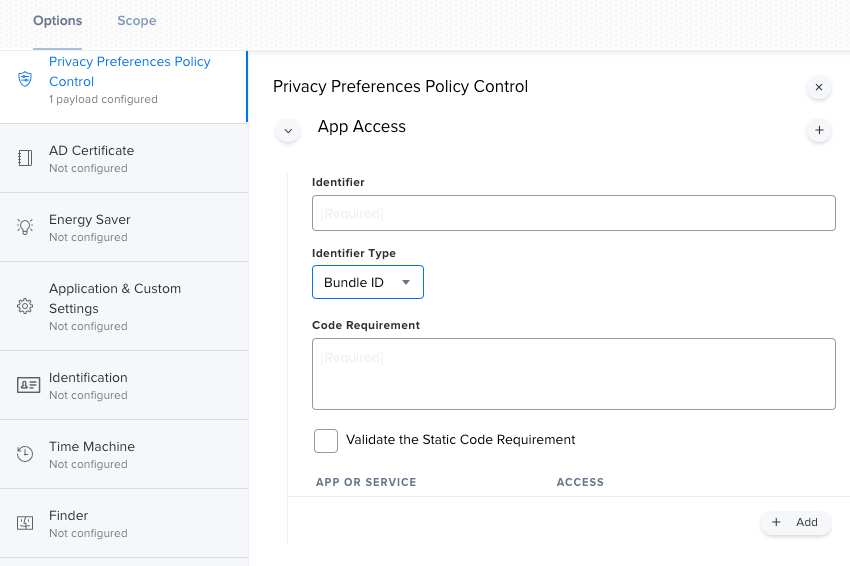
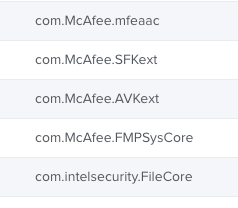
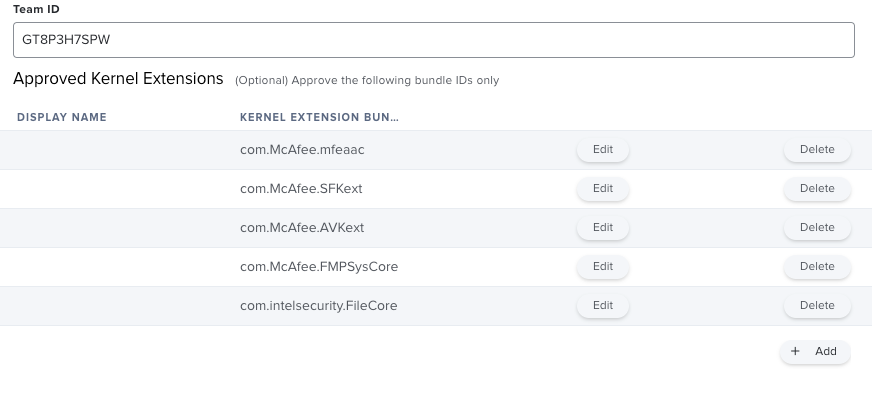
I would like to create a PPPC config file to allow McAfee to install without macOS blocking its system extension. Following this link: https://kc.mcafee.com/corporate/index?page=content&id=KB91109
it tells me the PPPC profile key needs to be "SystemPolicyAllFiles". Using PPPC Utility, has anyone successfully accomplished what I'm trying to do?
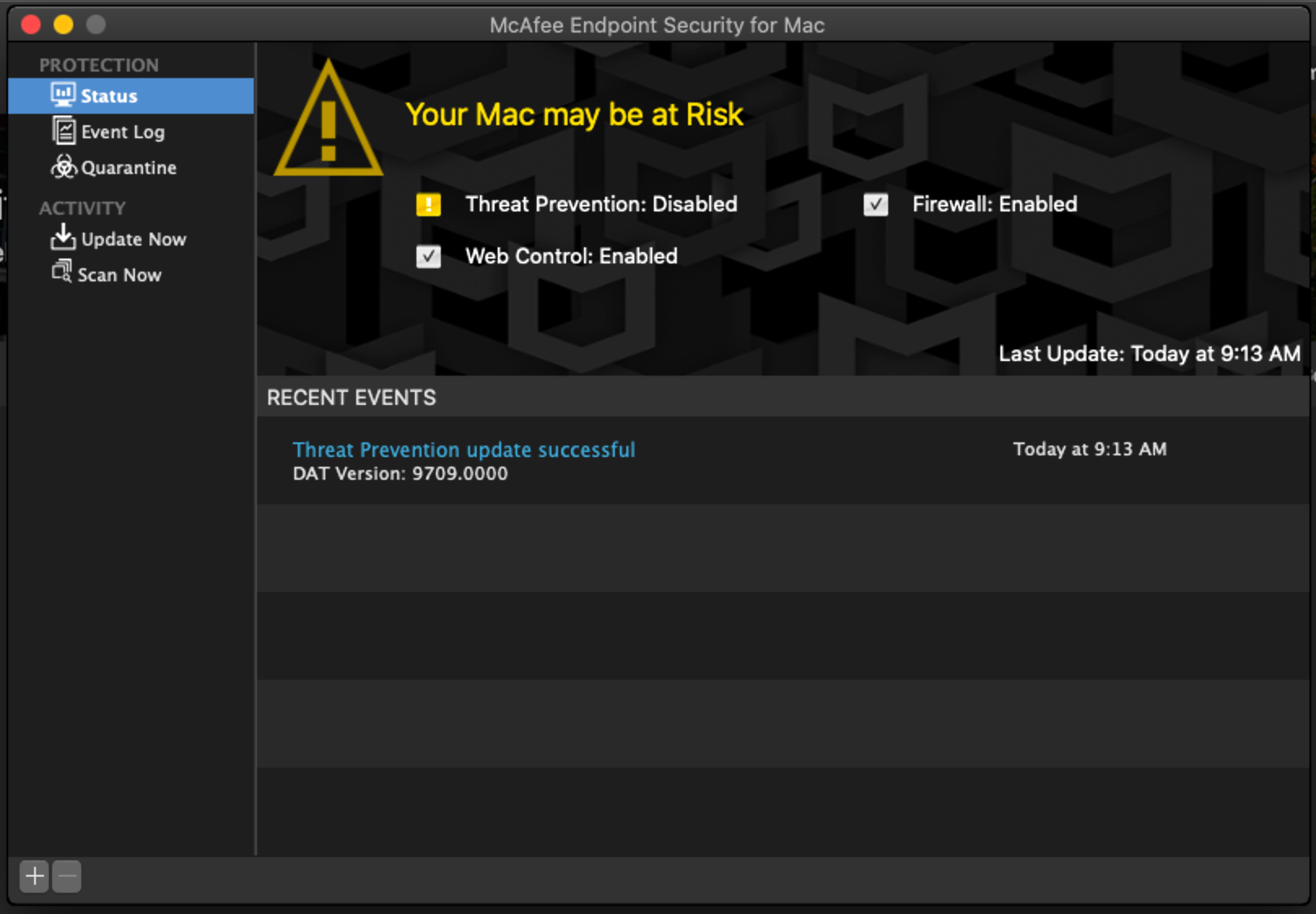
Essentially I want to push Endpoint Security and it not prompt the user to allow the extension.
Thanks,
Mike