Hello,
we have the following problem:
Nobody can change their AD password via NoMAD. This error shows up:
"Unable to change password: Configuration file does not specify default realm"
I found out as soon as I go to the nomad app container and execute the unix file, another NoMAD instance is opening and showing an icon in the menu bar, where I can successfully change my AD password:
In Jamf we deliver nomad and the launch agent as a policy and a Plist as a configuration profile.
This comes from the past, I dont know if this is enough and correct in this time:
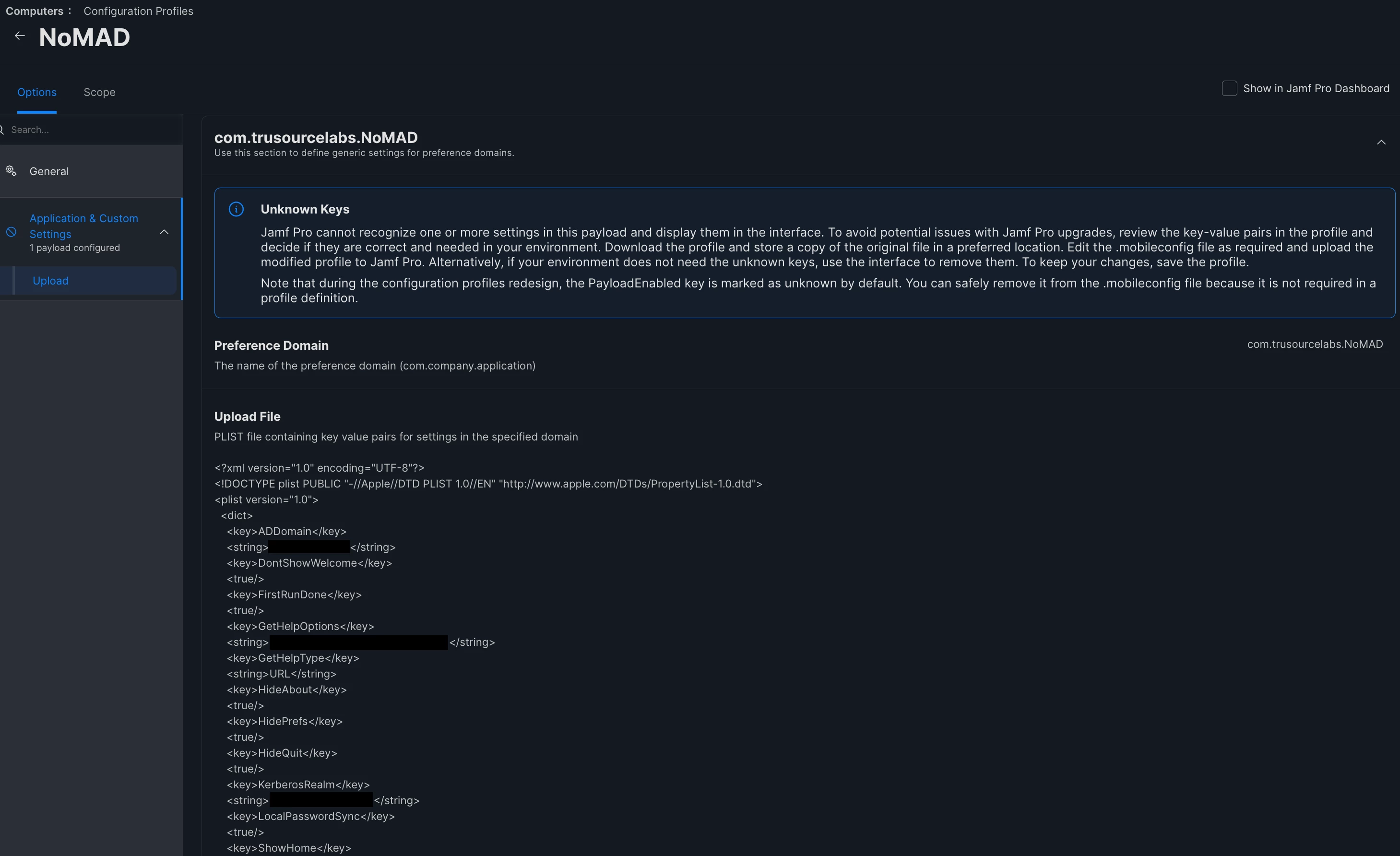
The weird thing is that it is working with the unix file inside the nomad.app which is on all our Macs.
Thank you for your help in advance!




