Hi All,
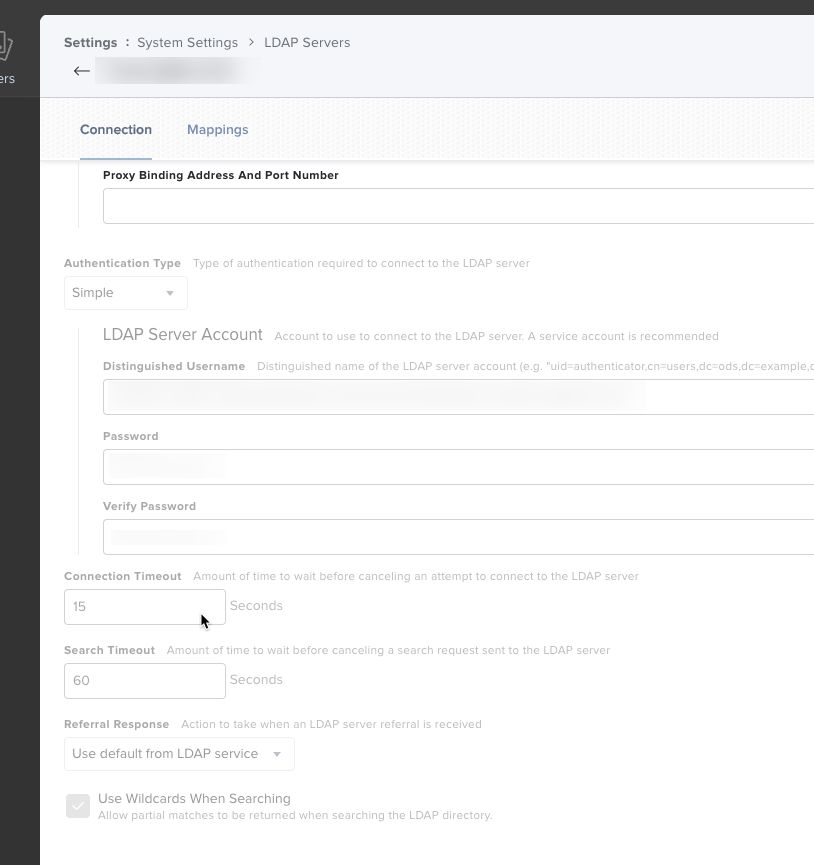
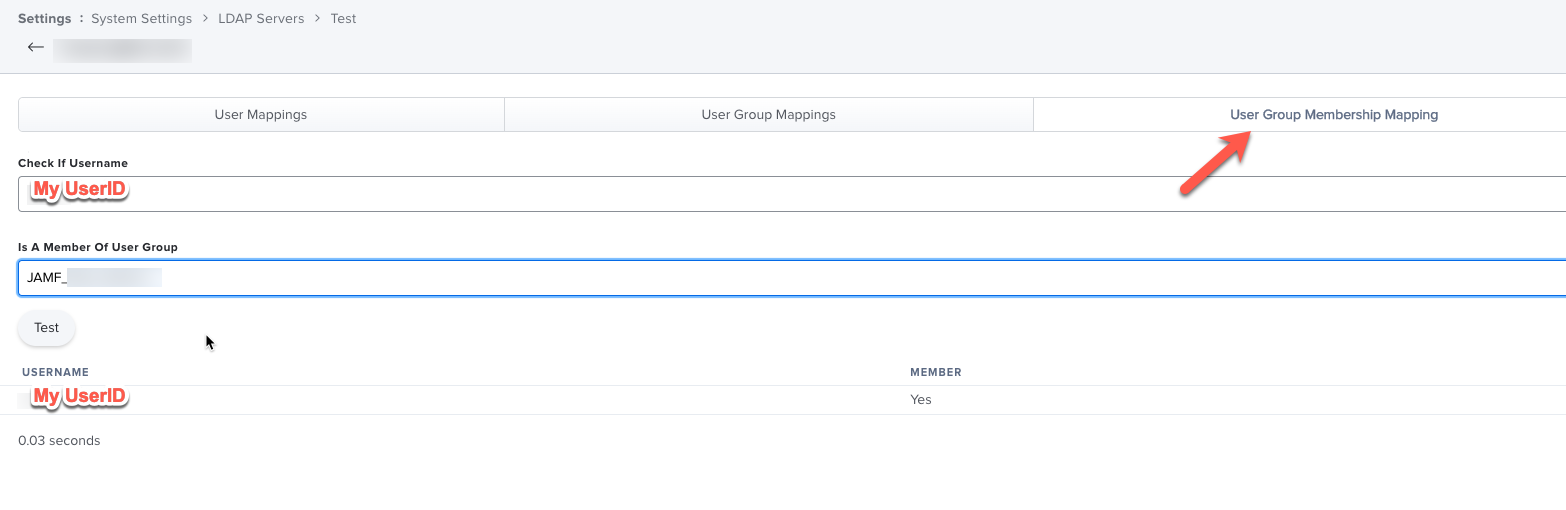
We've managed to setup Okta LDAP as an LDAP server for Jamf PRO and it shows correct in tests.
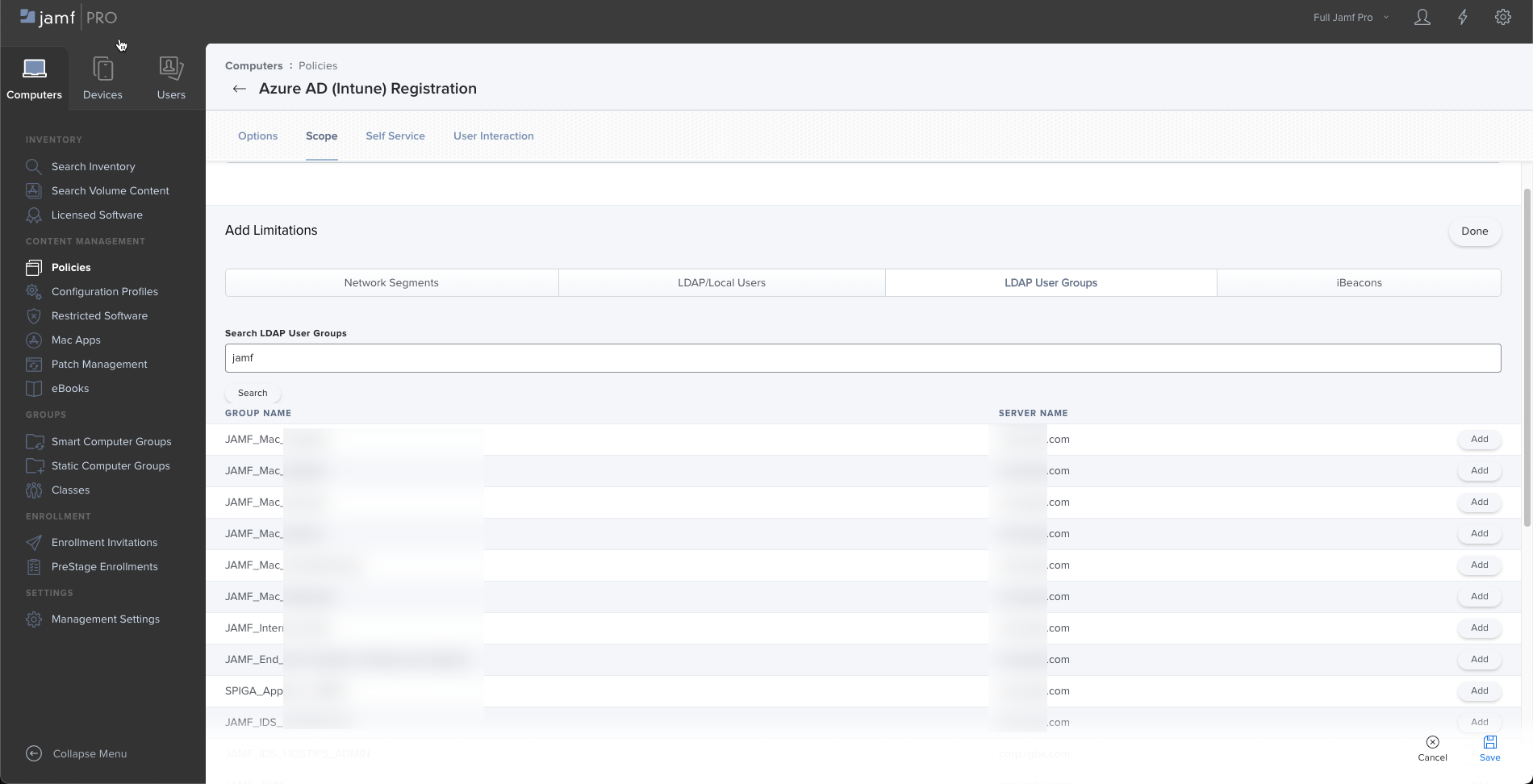
We've been wanted to setup an Extension Attribute for computers based on the LDAP group membership of the relevant user.
But no matter what we do (we use the memberOf or uniqueMember attribute) it won't show up with any value.
We also have JAMF Connect if that's relevant but I haven't been able to populate the UserGroups field in the state plist no matter what I do either.
At the end of the day we are trying to limit policies based on LDAP groups - and while we manage to setup the rule, no Computer/User is assigned to the group.
Any and all help would be greatly appreciated. Also let me know if you need any more info.