Hi all,
Just wonder if any of you ever came accross this and possibly have a solution.
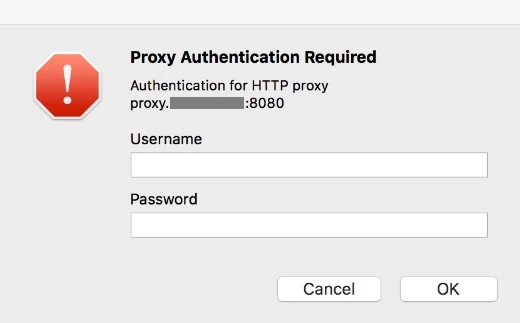
A few users in my company have complain that when they get onto the internet, they are greeted with a pop-up window asking for Proxy Authenication. This happens everytime, so obviously the user gets quite frustrating having to type in their password all the time.
I personal don't seem to have this issue. I believe my keychain has saved my password properly, and therefore doesn't ask me over and over and over again.
So, is there something wrong with the end-user's keychain? Or is it something else?
Anyone got a easy way to resolve these?
Most of the users are on OS X El Capitan 10.11.6, btw.







