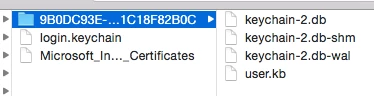
Would anyone have any idea on how to script a logout hook to remove the entire login keychain of the user logged in?
Solved
Remove login Keychain logout hook
 +8
+8Best answer by davidacland
@m.higgins that would be:
#!/bin/bash
user=$(ls -la /dev/console | cut -d " " -f 4)
rm -rf /Users/$user/Library/Keychains/*
exit 0Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.