When testing the SSO connection to AD over our VPN, if I disconnect and then later reconnect to our VPN, the SSO extension can't find the network. If I run a kinit command in terminal, this seems to resolve it, but I can't have users constantly do this because we're all WFH.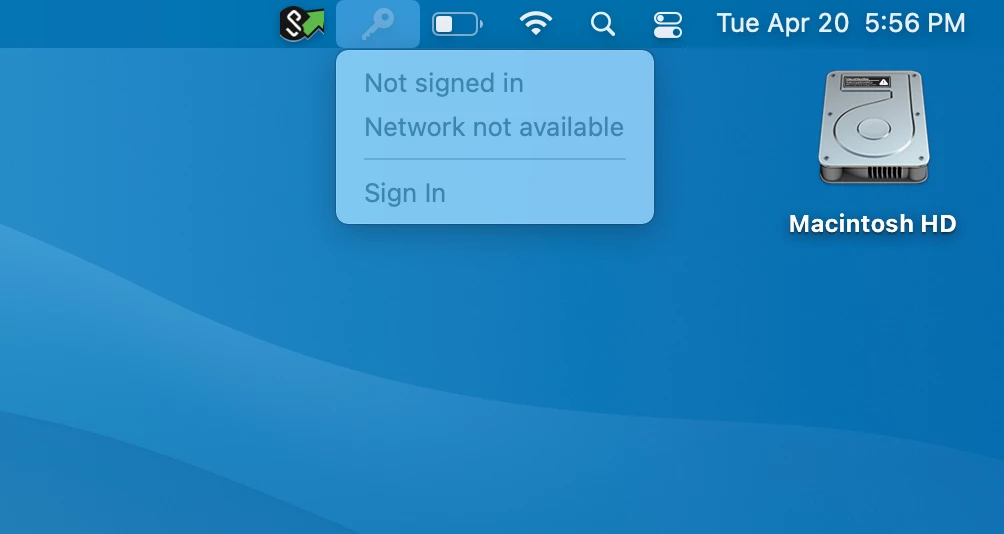
Question
SSO Extension not finding network
 +5
+5Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.


