Hello
We have been using SSO Kerberos Extension with local accounts for a few months now (Big Sur). (Mac is not joined to the AD anymore).
It works fine, with one major exception:
If a user is connected to the corporate network for more than 10 hours, the Kerberos tickets expire and unfortunately are not renewed automatically!
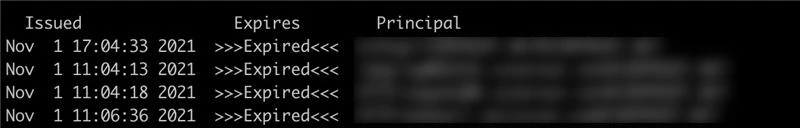
The TTL period for a Kerberos ticket is 10 hours. This is normal. But if the user doesn't log out daily, he doesn't even notice that his tickets have expired.
You can delete the tickets manually in the terminal with kdestroy and recreate them with kinit, but of course most users don't know that. (Besides, this should work automatically).
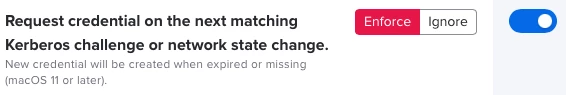
I actually expected this SSO extension to notice itself when the tickets have expired and then automatically re-login to the AD in the background. (The credentials are stored locally anyway).
When connecting to the corporate network it does this automatically. Why can't it renew the tickets automatically?
Is this normal or have we configured something wrong?
Thanks for any hint!