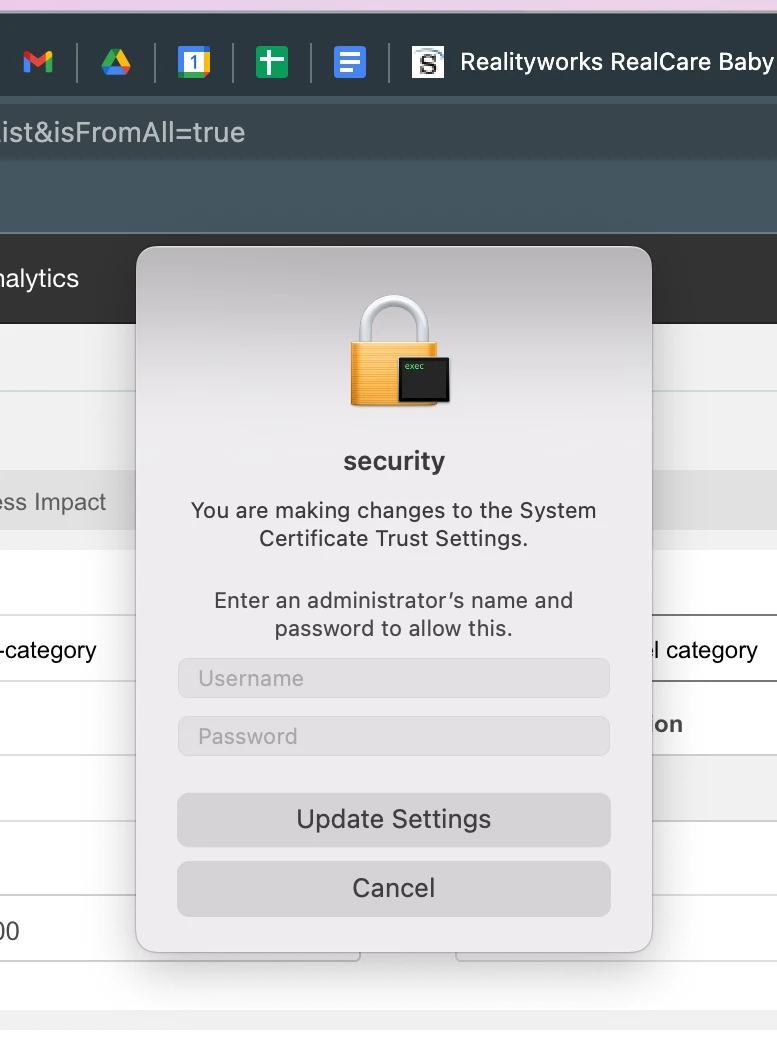
I'm seeing this popup on some of our users devices since the upgrade to Monterey, but I'm not entirely sure what it's trying to do, and it seems like I need to know in order to prevent it from popping up by automating what it's trying to do. I think this is from trying to install FortiClient, but I'm not positive.
How can I tell what it's doing so I can make this easier on our users?